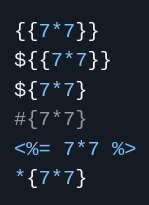Server Side Template Injection (SSTI).
Server Side Template Injecton Tutorial; Types, Detection, Exploitation...
This is just a tutorial on SSTI detection. If you want to learn more about it and even exploit this vulnerability, visit my GitHub for further details on Github - Server Side Template Injection (SSTI).
What is SSTI?
Server-side template injection is when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side.
Server-side template injection attacks can occur when user input is concatenated directly into a template, rather than passed in as data. This allows attackers to inject arbitrary template directives in order to manipulate the template engine, often enabling them to take complete control of the server.
SSTI types
We can distinguis two Server Side Template Injections:
1-Plaintext Context SSTI.
Detection
- First of all we have to see if we can manage the output:
- After that we have to check if the server evaluate the next expressions.
- Depending on the interpreted expression, the payload we’ll use must be in one language or another.
- If the expressions are interpreted we can proceed to do a Plaintext Context SSTI exploitation.
2-Code Context SSTI.
In a Code Context SSTI we have to deploy our payload in the code.